There has also been a significant increase in the number of companies doing gamification around phishing emails. This often takes the form of internal phishing simulations with companies recording how individuals do. The goal is to see how quickly an individual spots a phish and how they inform their peers and IT security teams. Peer to peer notification is a strong way to get people to take notice.

According to Aaron Higbee, CTO and co-founder at PhishMe: “With phishing attacks up 65% worldwide from last year, this continues to be the number one cyber threat to organisations of all sizes. Phishing attacks have the ability to skirt technology and target human emotion, making it imperative that organisations empower their employees to be part of the solution.
“Our analysis continues to show that conditioning employees to recognise and report on phishing attempts lowers susceptibility, which is proof that progressive anti-phishing programs keep organisations safer.”
What does the research show?
There are several interesting findings from the report. These include:
Susceptibility rates are falling: In 2015 14.1% of phishing emails were clicked on. By 2017 that number had fallen to 10.8%. It is corporate phishing simulation programmes that are key to the drop. It turns out that employees often spot the phishing emails but don’t tell other people. This raises the risk of someone being phished.
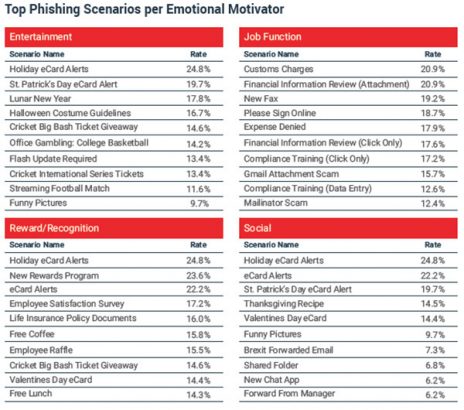
Consumer scams work best: The use of delivery issues, parking tickets and urgent orders are declining. The latest phishes target the users consumer side and job role. Entertainment (19.5%), social media (16%) and reward/recognition (13.8%) are becoming common. See the image below for the different attacks in each category.
Many of the attacks are based on themes and rely on users looking for a distraction. It might be an amusing image, a joke site, an update about a soap opera, celebrity gossip, free goods or tickets to events. All of these reel in the users as they look for something more exciting than spreadsheets, documents and database searches.
The keys to a proper simulation programme
To make a simulation programme work there are several things that organisations must think about. PhishMe believes that many programmes need to be thought through carefully to make sure they are accurate. This means that they need to reflect the sort of attacks users are seeing. They also need to be varied and traceable to see what users do and ideally to see how the spread them or warn other users about them.
There is also a need to keep running campaigns even when the type of attacks disappear. There are so many security alerts today that users become immune to them. If you stop warning about an attack people will forget about it. When the attack reappears, before you can restart the education there is an increased risk staff will already have fallen victim to it.
One tricky area is how to reward users for spotting them. One bank in particular has a departmental reward scheme based on performance in phishing and security attacks. They monitor users and departments to see how effective user training is. Another metric is how users pass warnings around their teams and departments. At the end of the day money, days off and other rewards are provided.
The challenge for reward programmes is dealing with tax liabilities. A more pressing challenge is pitching them at the right level for engagement and to show they have contributed to savings. The PhishMe report takes an aggregate figure for a successful phish of $1.6 million. It’s very misleading. It is based on a third party report which includes some very expensive phishes. Organisations need to do their own research into the cost of a phish as they would any data breach. That will give them some parameters to work into the rewards in their simulation programmes.
What does this mean?
Any time one type of cyber-attack declines, IT needs to look around. It means that there is another attack coming from a different direction. In the case of phishing, it is often a gateway attack to engage a user in order to launch one or more additional attacks. Simulation programmes are a great way to engage a workforce and help improve the ability of users to help themselves and the organisation.