
Work long enough on any computer, and you will find yourself looking at log files. Most people, including support teams, just ignore them unless they are trying to debug a problem. Huntress Labs says it has found a new attack that hides is malicious payload inside a fake log file.

The log file is just part of a trio of elements that John Ferrell, VP ThreatOps and co-founder, Huntress Labs describes as a foothold. In a blog, he writes: “We came across an interesting foothold recently; a scheduled task named BfeOnServiceStartTypenChange.”
When Huntress Labs looked more closely at the file, they uncovered a nasty piece of malware that uses the Common Language Runtime and PowerShell to grab data from the local machine. What is interesting is that this is a payload they have previously reported on. It seems that the attackers are just evolving their attack.
How does the malware work?
It’s relatively simple. The attack uses three files:
- BfeonService.exe
- Engine.exe
- a.chk
According to Ferrell, BfeonService.exe is a renamed copy of the mshta.exe utility. It is a program that executes Microsoft HTML Applications, files with the extension [.]hta. Similarly, engine.exe is also a copy of a Microsoft utility, powershell.exe.
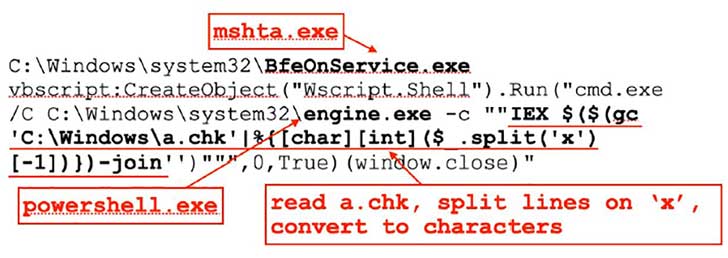
The two files use a script that Ferrell details in his blog and use that to read a.chk. That file contains obfuscated instructions that are reassembled to create a script. Once assembled, that script interacts with several URLs and another PowerShell command to get the payload. This payload collects data from the local machine, including:
- A list of installed applications (specifically looking for browsers, financial applications, and security products)
- IP addresses
- administrative privileges
The data is gathered from the Windows Registry and exfiltrated to the attackers URL.
Enterprise Times: What does this mean
This is a relatively simple yet effective attack. The attackers are using Windows utilities. It means they don’t need to worry about file signatures which allows them to sneak past endpoint security software. Using files that are supposed to be on the local machine is becoming increasingly popular with attackers. It also means that defenders tracking the Microsoft named processes, to stop attackers using them, will not see mshta.exe and powershell.exe.
Hiding the instructions in an innocent-looking log file is also smart. Defenders are unlikely to spot the attack unless they are specifically looking for it. Attackers could refresh the payload file by including it in other downloads from popular sites.
Defenders need to make sure that they are monitoring for new scheduled tasks to spot this type of attack.

























