In addition to steganography, the attackers are using PowerShell scripts, spear-phishing and the Mimikatz malware. The latter allows them to steal the Windows credentials of compromised systems. The attacks are customised and localised to match the target business. According to Kopeytsev: “The attacks only launch the malware used in this attack performed destructive activity only if the operating system had a localization that matched the language used in the phishing email.”
How does the attack work?
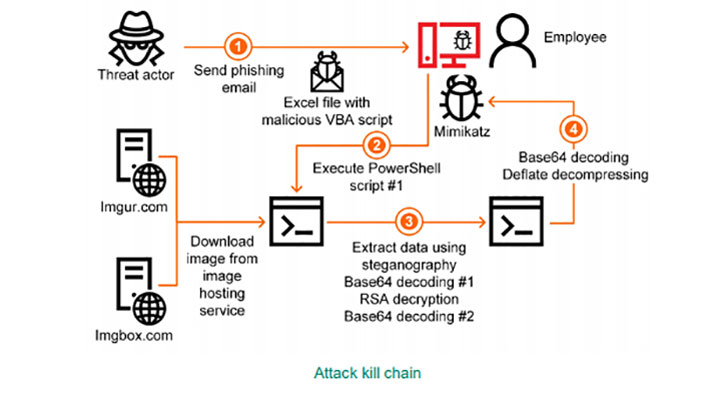
It all starts with a phishing email containing a file with a malicious attachment. The email is tailored in such a way as to persuade the user to open it, the attachment and then execute the embedded malicious macro. Kopeytsev describes an attack against a company in Japan.
- An email arrives with an Excel file attachment. Excel file contains a malicious macro identified as Trojan.MSExcel.Agent.be.
- Attachment is opened and presents the user with a screen asking permission to enable active content.
- User enables active content allowing malicious macro to execute.
- Macro decrypts and runs a PowerShell script, Trojan.PowerShell.Generic. It ignores local policy, runs in a hidden window and does not load the user configuration.
- The PowerShell script randomly selects a URL from an embedded list and grabs an image from imgur.com or imgbox.com.
- Hidden in the image, using steganography, is another PowerShell script which is unpacked and executed.
- Finally, TrojanPSW.PowerShell.Mimikatz malware is executed.
Steganography and encryption makes this hard to detect
Using steganography and encryption makes this a hard attack for security software to detect. The images containing the code are located on public servers that are unlikely to be on any blacklist.
Once the image is on the victim’s computer, the use of multiple tiers of encryption continues to make the attack hard to detect. The data in the image is encrypted three times using the Base64 algorithm, the RSA algorithm and another pass through the Base64 algorithm. In addition, the decryption key is an exception message, something that Kopeytsev says makes it even harder to detect.
Enterprise Times: What does this mean?
Targeted attacks against industrial control systems are nothing new. Attacks as sophisticated and deceptive as this one, are generally restricted to state-sponsored threat actors or complex cybercrime groups. Attacking companies that manufacture the equipment and software makes sense from an attackers perspective. If they can get embedded inside the equipment before it gets to site, they open up a broader target market.
One of the concerns of several cybersecurity companies during the current lockdown is the increase in attacks on the technology sector. Most of the public attention has been on attacks against collaboration and video-conferencing systems. However, Mark Thomas, Global Head of Threat Intelligence at NTT Ltd, recently talked about the increasing number of attacks on technology companies. This report from Kaspersky provides further evidence of those attacks.
There is also evidence that these attacks are drawing on problems with user education as well as taking advantage of work from home. A recent report from Tessian highlighted 52% of office workers feeling they can get away with riskier behaviour when working from home. The user enables this attack by – opening the attachment and allowing active content to execute. It highlights the need for better user education. Would they have done the same if in the office? It is a vector that needs further investigation.
For now, companies manufacturing ICS hardware and software need to increase their user education and security checks. If they do not, we can expect these attacks to underpin new waves of attacks against ICS in the coming months.