
One of the biggest challenges for organisations is the growth of identity. It is more than just an increase in employees. Organisations are opening IT systems to customers and suppliers as part of digital transformation projects. There is also a significant growth in IoT and IIoT with each device having its own identity.
What identity-related breaches have organisations suffered?
The report calls out seven different categories of identity-related breaches. The four that top the list are all easily dealt with through better user education and tooling. They are:
- Phishing (66%): This is the most common cause of identity-related breaches. As the survey was conducted in December, before the COVID-19 pandemic, the number of phishing attacks is lower than some vendors are currently reporting. What it does show is that there is a need for greater employee education to spot and prevent these attacks. Work from home has created an environment where these attacks are more prevalent and more effective.
- Stolen Credentials (32%): Reuse of security credentials is a major issue. Users not only use personal credentials across multiple shopping sites but also reuse business credentials across cloud-based solutions. As the use of cloud-based solutions grows, this will continue.
- Inadequately managed privileges (28%): Privilege bloat is a long-term issue for IT. Users rarely lose privileges as they change roles in an organisation. It means that a successful attack a board member often provides access to substantial portions of the corporate IT systems. Removing privileges is politically sensitive.
- Brute force attacks (24%): Good security software should identify these attacks and lock accounts. Too few organisations spot and remediate this.
What are organisations doing to improve security?
IT security teams believe that solving many of the identity-related breaches is simple. In the report, it sums up the responses saying: “One of the key revelations of this study is that almost all (99%) of security and identity professionals believe the identity-related breaches at their company were preventable.
“Participants reported that better security awareness training for users (71%), improved internal process (61%), better integration of existing technology (50%), better in-house expertise around identity and security (49%), better or wider implementation of technology already owned (41%), and the purchase and deployment of new technology (31%) could all have saved their companies from a breach in the past two years.
“A few individuals also took the time to write in “other” responses, including specific types of training, multi-factor authentication (MFA), and higher-level management approval to enable technologies.”
Knowing what the solutions are and implementing them, however, is where there is a disconnect between practitioners and management. Neither education or technology alone is an effective solution. Both solve parts of the puzzle, and both require management buy-in and support.
Better use of existing technology is required
It is relatively easy to audit any organisation and show it can make better use of existing technology. The survey asked respondents where they were when it came to eight identity-related security outcomes. Organisations can implement most of these without having to buy in specialist software or skills. This raises the question as to why so few are fully implemented.
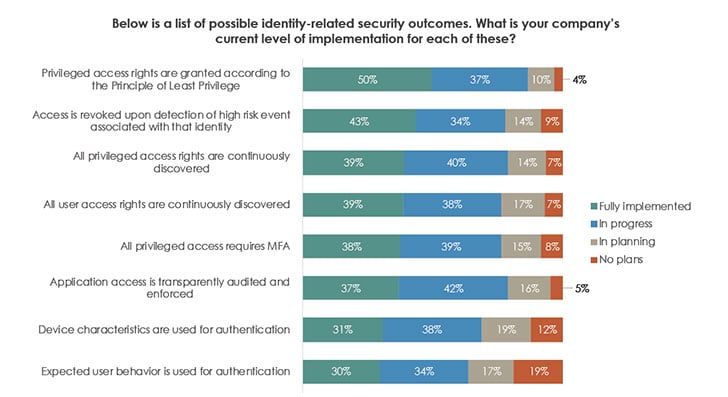
The least implemented is User behavioural analysis(UBA). There is no surprise here. UBA, whether it be for users, applications or devices, takes time to set up and ensure there are no false positives. Many organisations lack the skills necessary to implement it. Those that have implemented it often find themselves overwhelmed by data. It is one reason why there is an increasing use of AI and machine learning in this space.
Enterprise Times: What does this mean
Like any survey dealing with breaches, it is easy to find gaps and wonder why respondents are not doing a better job. It is also easy to get frustrated that those carrying out the survey didn’t do follow-up interviews to get more detail on the significant challenges.
That said, the survey does end on a positive note. It sees a proactive approach in some areas to improve identity-related breaches. It also shows that there has been an increase in security by ensuring ownership of the problem is down to one team inside IT.
The impact of identity-related breaches is not going away. The move to the cloud, digital transformation and greater use of IoT/IIoT will create more opportunities for cybercriminals. As the world emerges from the currency pandemic, larger organisations will see merger and acquisition opportunities. Few of those will see any effort to understand the risk from identity-related issues. It is rare to see any pre-merger/acquisition IT audit carried out. Not doing so only leads to breaches such as that at Marriott (Starwood).
























