

According to Thomas Owen, Head of Security at Memset: “Many of these exploits require vulnerabilities in the browser or Operating System, ensuring the user’s browser and OS are up to date (and have automatic patches) and running a reputable antivirus product will protect you from the majority of these issues.
“Browser plugins such as Web of Trust can also help warn you when attempting to visit a site that is known to be compromised or host malware. Lastly, general good hygiene is key – don’t routinely visit some of the less ‘reputable’ sites on the internet.”
How does it work?
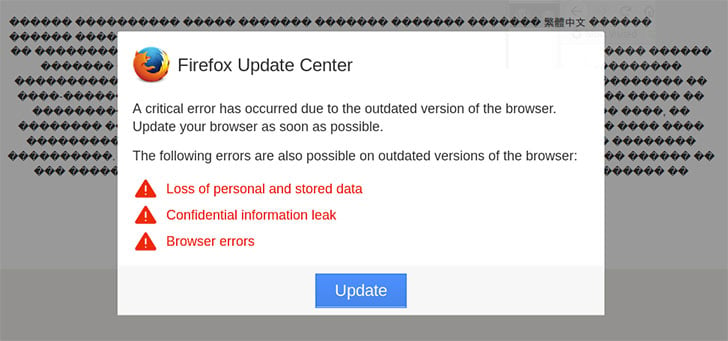
The attack is simple. The attackers compromise a poorly protected website. Users visiting that website see the warning box related to the browser they are using. At the same time the screen appears to show the website as a set of garbage text.
The warning box tells the user that they are at risk of:
- Losing data
- Leaking data
- Experiencing browser errors
To stop all of this all they have to do is click the update button inside the error box.
Clicking on the update button sends the user to a site that attempts to download malware from third-party sites. The malware should be detected by up to date security tools. Users not running anti-malware software run the risk of being infected.
Attacks against Windows users are mainly focused on ransomware. Malware identified by different engines includes Cerber, Kryptik and Crypted.
Attacks against Android are banking malware, with BankBot and Anubis identified. The latter is a particularly nasty piece of malware that targets banks, online payment systems and some crypto currency organisations. It is also claimed that it intercepts 2FA security messages sent to the device on which it is installed.
Website owners need to do a better job
At the heart of this attack, like so many others, are insecure websites. In this case the vast majority of the sites have been built in WordPress. The problem is that the owners have not patched them properly nor are they checking for any attempts to change their core files.
This is not just confined to websites built by individuals. It is widespread across small and medium sized businesses. Many of them have paid for a website believing that a one-off fee is all they can afford or require. While they take over adding content to the site, they don’t have the skills or time to patch the CMS or update plug-ins.
This leaves them open to sites being taken over and used to distribute both malvertising and malware. The former is an ongoing problem as many rely on third-parties to push ads to their site and have no clue whether the ads are appropriate or safe. When it comes to malware, they don’t know what security to use and when they have been hacked.
Owen commented: “First, last and always – Patch your CMS! Out of date CMS, such as WordPress or Drupal are 100% the main culprit for allowing sites to be compromised and to begin hosting malicious scripts and files. Users should also keep on top of password and admin management, ensuring that any administrative access to your hosting infrastructure and CMS is protected by, at minimum, strong random passwords. Default credentials (the password that is set up on installation) or easy to guess passwords mean that people don’t need to ‘hack’ your site, they can just log straight in and upload malware.”
Enterprise Times: What does this mean
Malware distributed via badly secured websites is becoming commonplace. The increasing need for businesses to have an online presence means that they are rushing in to having websites built but not maintained. They often don’t understand the underlying technology nor do they want to. Business owners also baulk at the idea of paying a maintenance contract with their website provider to keep it secure, updated and running.
All of this is good news for hackers. They actively search for insecure and out of date CMS installations. Most attacks come from inserting scripts into the site that can take advantage of when users connect. It also reduces the risk that the site will be flagged by malware hunting sites which would give the game away.
In this case, the malware is not just after Windows based machines but also Android. The mix of ransomware and banking malware is fairly common. Worryingly for Android users is the fact that at least one malware sample is capable of intercepting 2FA messages. This means that the malware owns the entire security chain to move money out of bank accounts. It can also authorise payments to credit cards.
Users need to make sure that they are running up to date security software on their devices. Companies should also ensure that any user with mobile access to corporate bank accounts or authorisation processes only does so from a secure device.


























