Security vendor Malwarebytes has taken aim at the AV industry. It has released details showing how ineffective many AV solutions are. It’s primary target are those AV solutions that rely solely on signature-based detection methods.

The blog by Marcin Kleczynski, CEO and Co-Founder, Malwarebytes states: “With signature-based detection methods, traditional AV solutions are simply weak against unknown malware and other malicious content. Meanwhile, consumers and businesses continue to trust AV solutions to protect their devices. So, how ineffective are they and what’s the risk to users?”
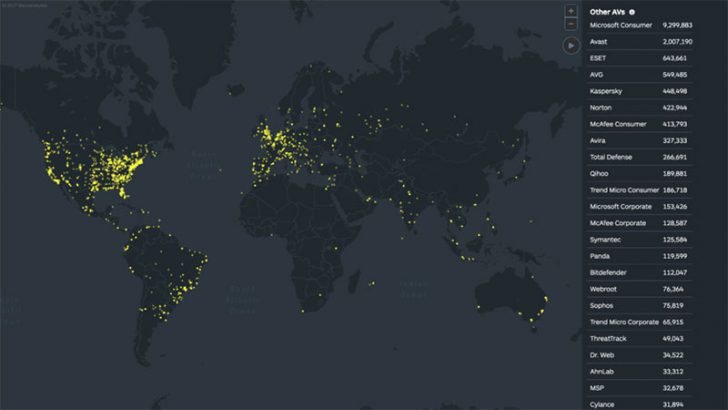
The top 5 AV vendors and the amount of malware they missed are:
- Avast – 2,007,190
- ESET – 643,661
- AVG – 549,485
- Kaspersky – 448,498
- Norton – 422,944
What level of risk does Malwarebytes see?
The risk, according to Kleczynski is that: “In just the month of October, there were about 4 million instances where traditional AV was ineffective against today’s threats.” This isn’t a risk it is a pending disaster. It can sometimes be difficult to separate out numbers from the way security companies report the number of attacks they detect. As a result reports like this can be lost in the number of apparent attacks reported at a global level.
Malwarebytes has given more details in its research and the numbers will worry security teams. It claims that nearly 40% of the malware attacks it cleaned up in the first half of 2017 occurred on machines with two or more of the products it has decided to name and shame. So far, there has been no response to that research from the AV vendors it mentions.
It has also created a real-time heatmap. This shows what malware it has caught and which AV products are installed on the local machines. The methodology to define what “caught” means has also been published. It is:
“For a dot to appear on the map three things must happen. First, a device has a third party anti-virus registered in the Windows Security Center. Second, the user runs a Malwarebytes remediation scan. Third, our scan must detect malware. We then add a numerical count for each detection next to the respective vendor’s name. These three elements represent our real-time global view of the threats detected by our remediation scans. Each dot represents a detection. There can be multiple detections for each dot.”
Interestingly, all of the AV vendors named regularly put out details of the attacks they spot and stop. They also publish their own Malware Top Ten lists. If Malwarebytes is correct about the level of missed attacks, these lists suddenly have very limited value.
What about the awards these companies get from AV test labs?
Interestingly, all of the AV vendors concerned claim to perform extremely well in industry tests. That has also drawn Malwarebytes ire. It has taken issue with the way testing labs deal with AV solutions. Kleczynski said: “..the true value of these tests is yet to be determined, as malware in the wild behaves in a manner significantly different from laboratory samples – even recently captured samples apprehended in security honeypots.”
Testing AV software effectively is difficult. Some labs simply capture as many samples as they can and they fire them at the AV solutions. As the samples are captured over several months, signature-based solutions should detect most or all of the replay attacks. This is the approach that Malwarebytes is attacking.
Labs are not in the position of testing attacks “in the wild”. They don’t have the wide network of endpoint devices that AV companies have. As a result they are using the best methodology available to them. It is also a methodology that, until now, the entire industry including Malwarebytes has been happy with.
What does this mean?
The most important thing here is do not panic. This is not the end of the world. Even if this is Halloween, your personal devices are not going to suddenly turn into malware ridden monsters in front of your eyes. That does also not mean ignore this. Despite the 40% of incidents where two or more AV solutions were installed, it is still best practice.
What is now clear from this and it is something that Malwarebytes admits, is the state of the AV installations. When were they last updated? When was a full check run? Are they legally licensed copies or are the users running pirated copies of software? How is the AV configured?
All of these will have a serious impact on the effectiveness of the AV solutions. However, even allowing for these issues, there are still serious concerns here that need addressing. It will be interesting to see how the AV vendors and test labs choose to respond to this research and heat map.