

On a media call to announce the report, Robert M Lee, CEO, Dragos, said: “Most of the world’s infrastructure is in no way monitored. So when adversaries get into operations environments, it is very challenging to find them, and it’s very challenging to remediate them. Very often, the threats that we come across, are laying inside of environments for months if not years undetected.”
That sobering assessment set the tone for the report and Lee’s call.
Some key highlights from the report
Some interesting highlights in this report show just how effective ICS/OT attackers have been. They also show how they are evolving their skills. Among the things the report calls out are:
- Dragos discovered three new activity groups with the assessed motivation of targeting ICS/OT, Petrovite, Kostovite and Erythrite. The latter two have achieved Stage 2 of the ICS Cyber Kill Chain showing their ability to get access directly to ICS/OT networks.
- Manufacturing accounted for 65% of all ransomware attacks and two ransomware groups caused 51% of attacks.
- 51% of attackers were caused by two Ransomware groups (LockBit 2.0 and Conti)
- 86% of service engagements have a lack of visibility across OT networks, making detections, triage, and response incredibly difficult at scale.
- 70% of service engagements included finding external connections from OEMs, IT networks, or the Internet to the OT network.
- 44% of service engagements included a finding about shared credentials in OT systems, the most common method of lateral movement & privilege escalation.
- 77% of service engagements included a finding about improper network segmentation.
- More than twice as many common vulnerabilities and exposures (CVE) were published in 2021 than last year.
- 38% of ICS vulnerability advisories contained errors that would make it difficult to prioritize mitigations.
- 49% of the advisories could cause both a loss of view and loss of control in OT systems.
- 65% of advisories contained a patch but no alternative mitigation if patching was not an option.
- 61%, the percentage of advisories for which Dragos provided mitigation advice that was missing.
- 92% of advisories that Dragos tracks had no mitigation and 96% had no alternate mitigation.
Activity groups getting smarter
Dragos refers to those targeting ICS/OT networks as activity groups and names them after minerals. The report mentions six of them Stibnite, Wassonite, Kamacite, Petrovite, Kostovite and Erythrite. They are all believed to be active in either ICS/OT attacks or, in the case of Kamacite, enabling attacks by other groups.
The report also calls out where these organisations are on the ICS Cyber Kill Chain. Lee said, “When we talk about threats, we distinguish between stage one and stage two. The ICS cyber Kill Chain is a paper that Mike Asante and I wrote at the SANS Institute. Basically what it states is stage one is when adversaries are in IT networks, but they’re very clearly trying to get into the OT networks.
“So an intrusion at a power company would not be interesting to us on the surface. An intrusion into a power company where the adversary is doing engineering drawings, trying to get engineering maintenance access into a power plant, things like those would then qualify as stage one. It shows some level of intent to go and do something around the ICS.
“Stage two is where they’re actually in ICS and operations networks. They’re rare to become public. At the end of that kill chain, that’s where adversaries have the ability to then disrupt and cause destructive or disruptive effects. Just because we reached stage two does not imply immediately that you can do that.
“I would say that we track groups and kind of three categories. One As they’re just trying to get access to the ICS, they’re learning. The next category is they’ve gained access. They’re either doing espionage for intellectual property or future capability development, but they’re not quite there. The third category is the much rarer, which is they’ve actually shown the intent and capability to do disruptive and destructive acts.”
Access does not mean taking down networks
Of concern to Dragos is that there is an increasing number of activity groups that have already gained access to target networks. The question now is, when will they start malicious activity? Access, of course, does not mean an attack to take down a network is imminent. There are often multiple rounds of intelligence gathering and exfiltration of data.
Much of that data is held on IT networks and is being targeted by other actors. The problem, is that for many of these organisations, there is little separation of IT and OT networks.
The report states: “In many industrial sector compromises, weak boundaries between OT and IT, and poorly understood interactions between these systems, coupled with the rise in remote access (as more organizations rely on their work-from-home staff), has increased the overall risk. While ransomware mainly targets enterprise IT systems, there are a number of instances when it does impact OT directly and in integrated IT and OT environments.”
Dragos also sees that leakage problem as continuing. It believes that companies will continue to shut down their OT environments when their IT networks are compromised. While this is a sensible precaution it also means companies have to be clearer about what has happened. For example, in the Colonial Pipeline attack, the media attention was focused on it being an OT attack. It turned out that the shutdown of the pipeline was a preventative measure after IT systems were compromised.
However, not all ICS/OT attacks are leakage from IT attacks. Dragos calls out Ekans as a group that specifically targets ICS/OT systems with ransomware. It raises the question of, when will organisations invest more in ICS/OT specific security?
Who is being targeted?
An increasing degree of media attention tends to be focused on ICS/OT attacks and Critical National Infrastructure (CNI). Of interest is that Dragos sees 65% of ransomware attacks being targeted at manufacturers. This is almost six times the number of attacks against the second attacked industry Food and Beverage (11%).
With manufacturing, the main targets are Metal Components (17%), Automotive (8%), and Technology (6%). It will be interesting to see how that shifts over the next few years as vehicles become more autonomous. It is likely that attackers will see vehicle attacks as much more lucrative than current ransomware.
Data-driven insights from the field
This section of the report should be of interest and concern to many organisations. For example, Dragos says that 86% of its services customers had limited to no visibility into their ICS environment. Interestingly it goes on to say:
“Visibility is more than asset inventory. When customers only monitor the IT to OT boundary without monitoring the activity inside the ICS network, Dragos considers this limited visibility. Frequently, defenders are blind to critical network traffic when they do not capture the OT communication flows, or they capture these flows, but do not utilize ICS protocol dissection. Full visibility is achieved when network and device logs are centralized and can correlate various segments with network traffic analysis and asset inventories.”
It raises the question of, how many ICS/OT environments are little more than black holes to many companies? One of the problems of the push to make IT security responsible for ICS/OT environments is a lack of skills and tools. Getting the skills from the subject matter experts, mainly engineering teams, is hard. It also means talking to and engaging vendors to understand what is installed and how it works.
Even with this, few organisations have playbooks that extend outside of their IT networks other than “shut it down”.
Other findings from Dragos include that in 2021, external connections to OT spiked upwards, more than doubling to 70%. It raises the question of, how many were able to track this? Another finding was the level of shared credentials across IT and OT networks. Sadly, that just reflects poor security practice and controls across organisations, especially those in rail, food and beverage and, would you believe, datacentres.
How ready are you?
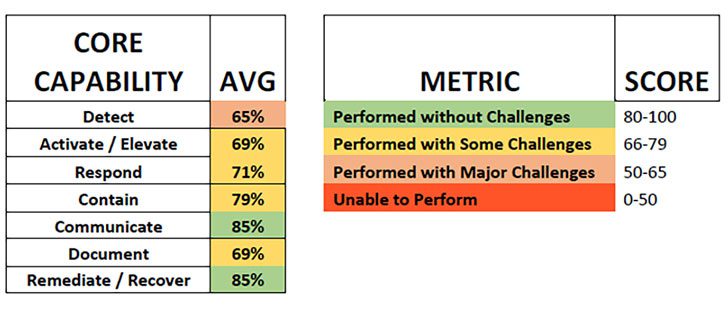
Perhaps the most interesting part of this report, to some degree, is that on cyber readiness findings. It brings together the findings from multiple cybersecurity tabletop exercises (TTXs) that Dragos has conducted on multiple industry verticals.
There are seven core capabilities that Dragos looked at. It ranked each one based on its aggregate score. The intent is to see where the gaps are in organisations capabilities. The results show some worrying gaps, not least in terms of the ability to detect risks to ICS/OT environments.
Enterprise Times: What does this mean?
This is a really interesting report that focuses on realities rather than just pushing out large volumes of statistics. There is also a lot for organisations to take away including indicators of compromise for the three new groups that Dragos has named. The report also provides organisations with a large number of talking points for their CISO and C-Suite.
Among those talking points are a set of five security controls that everyone should be using as part of their IT cybersecurity program. It would have been interesting to see an aggregated percentage of the number of organisations who do have these controls in place. Enterprise Times expectation is that it would not be high for any of the five controls.
Under normal circumstances, the focus would be on the next version of this report on 2022. However, the current situation in Ukraine and the massive number of cyberattacks resulting from that, change that. Organisations that do not take notice of the findings in this report will have to rely on the hope that they can stay off the radar of the attacks that are currently ramping up.
























