
The report, which is remarkably short at just eight pages, pulls no punches. It says healthcare is underprepared to deal with the industry threats it faces. There is nothing new in that statement. Healthcare has and remains an easy target for cybercriminals for everything from data theft to ransomware.
The problem for healthcare is in how data is stored and managed. There have been many suggestions of ways to limit access to data, but all have their problems. One of those is the use of blockchain and a consent-based patient permission system. The challenge with this is that the patient often has little idea of who needs access to their data. As such, limiting access can have a detrimental impact on healthcare delivery.
Another major challenge for the sector is the industry’s disparate nature and the way public and private parts interconnect. GP surgeries, hospitals, dentists, physiotherapists and other services all need access to different levels of patient data. Restricting the data is a major challenge but one that is seemingly overdue.
The problem is global
The problem that Varonis is highlighting is not constrained to any one country or region. Larger healthcare organisations did better than smaller ones, presumably due to larger budgets and dedicated IT staff. It raises a question of where the private sector is in providing better security and advice for small to medium-sized organisations.
When it comes to personal health information (PHI), large organisations have up to 16% of files open to everyone. That compares to 23% for medium-sized organisations and 25% for small organisations. What is interesting is that Varonis compares this to another highly regulated industry, financial services. It says: “Compared to financial services companies, the average healthcare and biotech organization has about 75% less data. While healthcare entities have fewer files, they have a greater number of files open to every employee. Attackers that successfully compromise one authorized device could land and expand throughout the organization or encrypt massive amounts of data with ransomware.”
Given the attacks against healthcare and biotech companies over the last year, this comparison raises a question of where the regulators and the auditors are. It gives the impression that both are failing to do their job to improve patient data protection.
Healthcare insider threat a significant issue
The insider threat is ever-present for any organisation ranging from the careless to the malicious. Given the sums on offer from ransomware organisations seeking partners, there is significant scope in healthcare for insider attacks.
To establish how large a risk the insider threat poses, Varonis looked at the state of data by terabyte. It looked at the number of folders and files per terabyte and, more importantly, the amount of sensitive data per terabyte. It also looked at the number of exposed files and data saying: “On their first day, new employees at small companies have instant access to over 11,000 exposed files, and nearly half of them contain sensitive data. This creates a massive attack surface and increases the risk of noncompliance in the event of a data breach.”
However, a closer look at the data shows that large and medium-sized healthcare organisations have a bigger issue. With medium-sized organisations, that number soars to over 19,600 files. A more accurate representation is not exposed files but exposed sensitive files and stale sensitive files. Just because data is old does not mean it has no value. Using those criteria, the numbers look very different.
| Organisation size | Exposed files | Exposed sensitive files | Stale sensitive files |
| Large | 13,108 | 993 | 8,136 |
| Medium | 19,611 | 1,966 | 13,114 |
| Small | 11,888 | 5,107 | 6,425 |
| Average | 15,490 | 1,646 | 9,906 |
Password abuse overshadowed by appalling security policies
Password reuse, misuse and abuse are constant topics in the security business. But this report shows that the usual policy of making password issues all down to users is complete rot.
Varonis looked at two issues with passwords and accounts in Active Directory. Security experts should look away now or, at the very least, have a very strong drink in hand.
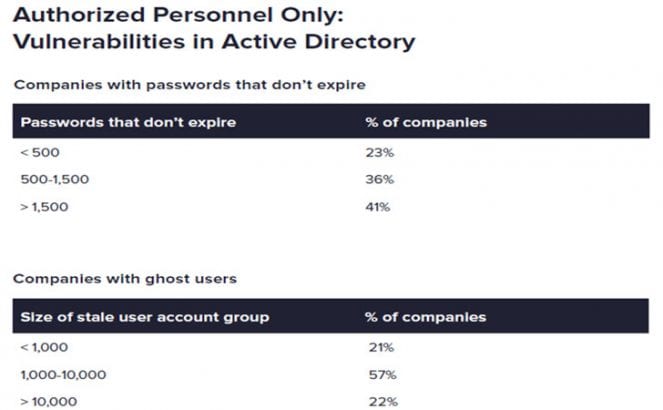
Having passwords that don’t expire makes it easy for attackers to get into a system. Having so many in an organisation means that any credential compromise is likely to go unnoticed for a long time. But it is not the dodgy password behaviour here that is the biggest issue. The number of ghost accounts for workers who have left or used as service accounts shows a real problem across many of these organisations.
That said, there might be some mitigation here. Varonis did not specify how many of those ghost users were service accounts for IoT devices. For older hardware, many were hardcoded and cannot be changed or, in some cases, secured. Despite that mitigation, the number is still shockingly high.
It is also another indicator that auditing is ineffective, and regulation needs to be both enforced and reviewed.
Enterprise Times: What does this mean?
This is a report that has no crumbs of comfort for healthcare. Any CIO, CISO or IT security professional in the industry should look at this and then check their systems. Any IT auditor and compliance officer should take a deep breath and start to see just how bad things are at their organisation. It is hard to see any real positive in this report at all.
What will worry patients is that the wave of ransomware attacks and data breaches at healthcare facilities is at plague levels. From the outside, it seems that the attackers are devoting huge resources to attacking these facilities. However, what this report shows is a level of incompetence or complacency, call it what you will, that enables attackers to be successful.
The question now, is will 2021 be the year healthcare cleans its act up, or will next year’s report be just as damning?
























