

Anton Shipulin, Solution Business Lead, Kaspersky Industrial CyberSecurity at Kaspersky said: “The activities of any company, especially an industrial one, affect many aspects of society. Sustainable development initiatives aim to ensure that this impact is either neutral or positive.
“From this perspective, organisations being reliably protected from cyberthreats is not just an individual goal – it is part of an overall sustainability trend. Adopting a corresponding concept means thinking about the role cybersecurity has in a business’s agenda and how it should be improved to cover both corporate and industrial infrastructure, as well as ensure all employees follow proper cyber-hygiene practices.”
Work from home has increased the threats
COVID-19 and employees working from home (WFH) have stretched cybersecurity. Administrators are seeing an increase in unwanted network scans from WFH employees. One reason given is that this is due to employees using personal technology, not company-managed devices. Many cybersecurity teams say they lack visibility into the devices connecting to their networks and how secure they are.
The report highlights a number of changes to cybersecurity that the pandemic is causing, as shown in the graph below.
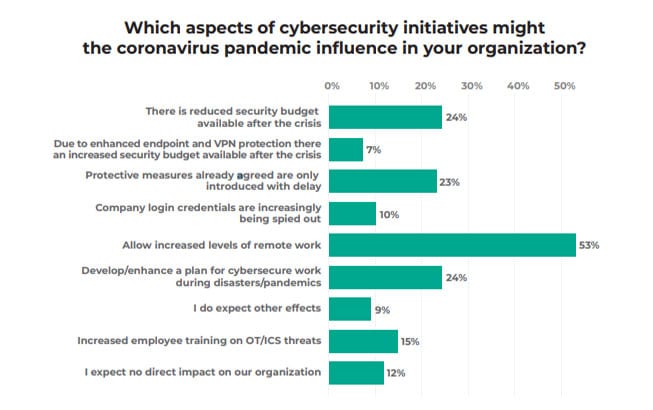
The reduction in the security budget (24%) is of particular concern. It is almost as if management believes that not having employees in the office makes it more and not less secure. Similarly, only 24% seem to want to change their process due to increased WFH.
A recent NTT Ltd report showed there has been a significant increase in the number of Business Email Compromise (BEC) attacks during the pandemic. This is believed to be caused by poor business policies that are being exploited by cybercriminals.
Changing attitudes around ICS security
Industrial Control Systems (ICS) have become a popular target for state-sponsored cybercrime groups. They see cybersecurity around ICS systems as being weak and easily broken. Few ICS systems were designed and implemented by IT departments which means cybersecurity was not factored in. These weaknesses allow attackers to steal intellectual property, install malware such as ransomware, and disrupt businesses.
It has led to a change in how ICS solutions are deployed. 67% say that a multidisciplinary team now carries out the deployment of ICS. Teams now include people from IT, ICS, safety and production. This has increased cybersecurity at installation time, but there are still ongoing issues. Those issues affected the speed with which vulnerabilities are dealt with.
The reasons for delays in applying patching and updating include:
- 34% – undesired production stoppages
- 31% – approvals taking too long
- 23% – too many decision-makers involved
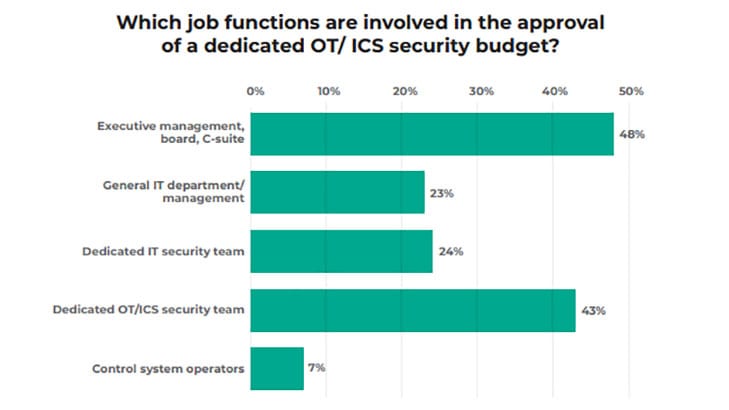
The solution, claims Kaspersky, is to have a single individual with responsibility for the entire process. This is where the CSO comes in. The image below shows how many different job functions are involved in OT/ICS security budget approval. It demonstrates the challenge of getting things approved
The impact of COVID-19 on Operational Technology (OT)
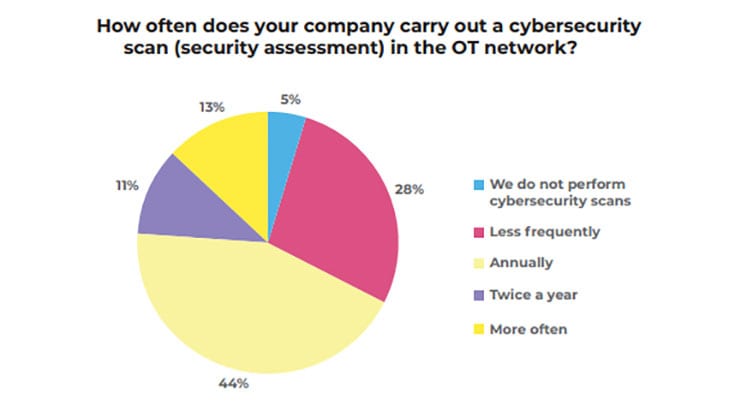
There has been a significant shift in attitudes towards security assessments on OT networks. Scanning of the OT network has improved. Only 5% do not do a cybersecurity scan of their OT networks, and 44% do it more than twice a year. This is still not comparable with how IT networks are treated but is has improved markedly from 2019.
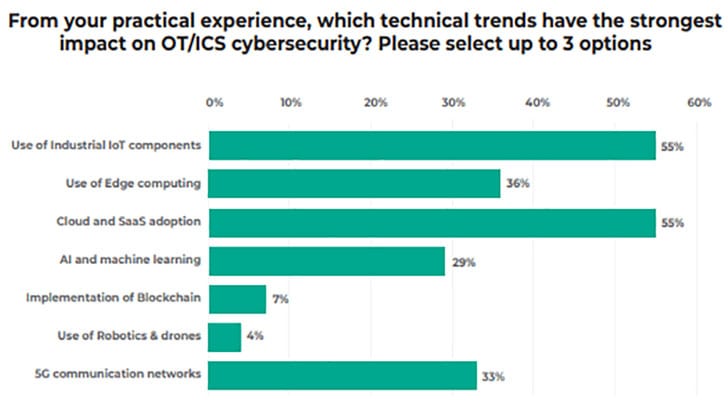
Unsurprisingly, many of the respondents (55%) see digitisation as increasing the risk to their IT environments. Those threats come from the cloud and edge computing as well as connecting OT networks to the internet. All of these are seen as creating a wider attack surface for OT networks.
How can a Chief Sustainability Officer solve this?
Despite 98% saying a CSO would improve cybersecurity around ICS systems, only 44% actually have one. The remainder of companies said they wouldn’t create a CSO role. To understand more about this, Kaspersky did a series of interviews as part of the report.
It says: “During the qualitative discussion, companies stated that under control of the CSO, they redesigned processes to handle customer and employee data as well as business partner information. Obviously, the CSO manages personal data protection, but it remains crucial for companies to safeguard other business-related information to prevent damage to its competitive position in its market, as well as its brand and reputation. Cybersecurity is a vital part of data protection, and with CSOs’ help, the importance of cybersecurity will be elevated in companies.”
Enterprise Times: What does this mean?
Many ICS systems were never thought to be a security threat. They were designed and implemented by engineers without reference to IT. IT, in turn, never expected to have a hand in managing ICS and OT systems. That has now all changed and continues to change as attackers exploit vulnerabilities in these systems.
There is now an increased awareness of the need to improve cybersecurity in these systems. To ensure that it is consistent, ARC has developed a cybersecurity maturity model for ICS systems. It can be layered into existing models for cybersecurity maturity to improve the protection for systems.
As organisations renew and update their industrial environments, there is a need to look at how they are secured. While the maturity models provide a pathway, there is still a need for a single voice to manage security. The CSO might just be the person organisations need to solve this problem.
























