
The report draws on 1,650 infrastructure insights and assessment with NTT Ltd customers around the world. Between them have a combined total of 808,428 network devices. It also analysed over 200,000 support incidents covering over 17 million assets. The data set has been built over the last five years. That breadth of customers and incidents over five years makes the findings from this report worrying.

Commenting on the data, Rob Lopez, Executive Vice President, Intelligent Infrastructure, NTT Ltd, says: “In this ‘new normal’ many businesses will need, if not be forced, to review their network and security architecture strategies, operating and support models to better manage operational risk. We expect to see strategy shift from a focus on business continuity to preparation for the future as lockdown begins to ease.
“Network infrastructure needs to be appropriately architected and managed to deal with unplanned surges, which will require a relook at cloud and on-premises infrastructure to reduce the impact and frequency of business-critical outages.”
What findings should we be worried about?
There are plenty of findings in this report that show a lack of investment in IT infrastructure. The question it raises is, why? How many organisations lack visibility into their networking assets? Do they have an accurate asset register? Which industries have the biggest problem?
Some of the key findings from the report are:
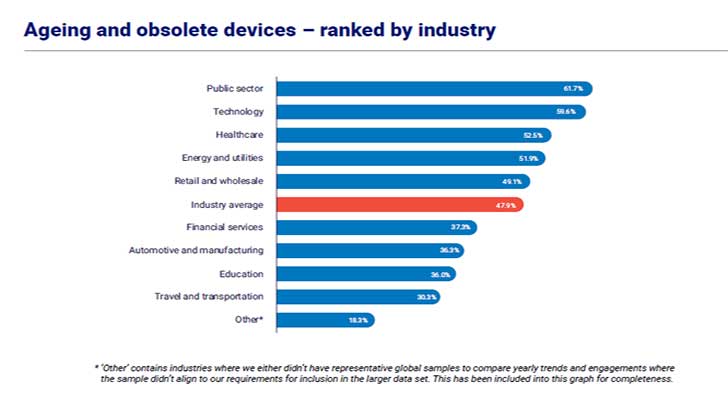
- In 2019, 47.9% of businesses’ network infrastructure assets were ageing or obsolete, compared to only 13.1% in 2017.
- Vulnerabilities per device rise rapidly as the device ages. Obsolete devices have an average of 42.2 security advisories per device. Ageing devices have fewer at 26.8, and current devices have around 19.4 vulnerabilities per device.
- The worst sector is technology. 59.6% of network assets are ageing or obsolete. Two years ago it was just 19.9%. Given that the GTIR report showed technology as the most attacked sector at present, it needs addressing.
- Healthcare has seen a significant rise in ageing or obsolete network assets in the last year from 15.7% to 52.5%. Despite being under constant attack from cybercriminals, it is struggling to cope with the current pandemic. It is unlikely that it will see any significant asset replacement programme in the near future.
- Configuration errors have increased by 5.2% compared to 2017. Cloud breaches are often caused by configuration, so organisations need to increase skill levels.
Some good news among the gloom
Among the worrying figures, there are signs that organisations are moving to alternative network approaches.
- Deployed software-defined ready infrastructure is increasing by 13.0% year-on-year.
- Software-defined WAN (SD-WAN) adoption is increasing with an 84.7% year-on-year growth rate. Over 58% of survey participants are either considering or undergoing SD-WAN transformation.
- New wireless infrastructures are on the rise. Deployed wireless access points are up 13.2% year-on-year.
- Software bugs have decreased by 17.7% compared to 2017.
What does all this mean?

To get more details on what these numbers mean, Enterprise Times talked with both Lopez and Andre Van Schalkwyk, Group Network Advisory Director, NTT Ltd, about the report. ET started by asking for more clarity around the data.
Commenting on the data sets, Van Schalkwyk said: “The assessment data is natural data that we find on clients environments. That’s non-biased through us because some of those are existing clients, some are new clients, some of them have been clients for many, many years. None of that data is influenced by us actively selling to somebody in the client that’s making a decision to purchase something at some point in time.”
How do you define the categories of device?
Van Schalkwyk: “We have three categories and multiple vendors represented in this data set. That meant we had to normalise the data set, the lifecycle milestones, into specific buckets.
- “Current: These devices are sold by a vendor, and we can actively maintain it. The vendors provide some software patches and updates, and there’s a maintenance contract that can be attached to it.
- “Ageing: Those are devices that the vendor no longer sells, but still actively support. We can attach some form of maintenance contract to it. If there’s a vulnerability, they’ll release a software patch for it. It there are new features or specific bugs that need to be addressed, they’ll actively push out software updates for those.
- “Obsolete: These are devices that are no longer sold and no longer supported by the vendor. So there is no software updates released for it, no security, vulnerabilities fixed etc.
“Obsolete is quite clear. There are also certain risks associated with ageing equipment as well, and that is related more to cost management. As devices get older, vendor maintenance becomes more expensive. As you get to the end of that lifecycle stage, getting parts and replacements becomes harder. Typically, once a device is no longer sold, it still has a lifetime could be five years, 10 years, 15 years, but it also functions fine.”
Are companies moving from owned infrastructure to cloud-based infrastructure?
Lopez: “We released a survey in March around managed services, trends and sourcing trends. That did come up as a trend. It’s important to note that it’s not linked to this dataset. A lot of these clients, by definition, are clients who are under a support contract with us. Some of them are managed services as well. By definition, they tend to be more insourced focus.
“The tech industry had a higher percentage of ageing and obsolete equipment. The biggest trend that we can attribute to that is more of a move towards cloud-based consumption. A lot of the clients perhaps perceive their on-premises infrastructure to be less critical. A lot of the critical stuff is now in the cloud and purchased as a managed service.”
Van Schalkwyk believes that this is also about the way budgets are changing. He sees IT budgets increasing by low single digits year on year. However, cloud budgets are running at 20-25% year on year. To support cloud expansion, IT budgets, especially hardware refresh, is getting cut.
Should the CISO be worried about ageing devices?
Van Schalkwyk: “As devices age, there are more and more vulnerabilities within the software on those devices. It is something that we’ve been calling out for multiple years now. If you ask clients whether or not they have a patch management process in place, the majority will say, yes. When you ask for evidence of patch management processes in production, that’s where the wheels start coming off.”
Problems with patch management processes are pretty standard. High profile outages and breaches of systems are generally caused by old, unpatched, software. In this case, with the lifecycle of devices being extended, it is more than just poor patch management to worry about. Once devices are out of support, there are no patches, but the vulnerabilities keep coming.
Van Schalkwyk commented: “If that device is 5, 6, 8 or even 10 years old, the number of vulnerabilities on the device increase. It is very counterproductive. If you look at the technology sector with a high percentage of ageing and obsolete devices, and they’re being attacked quite heavily, one would think that they’re doing patch management of on-premises infrastructure. That would be false.”
Many vendors have moved to automated patch management, but Van Schalkwyk says that is not applicable in network devices. The reason is that patches for these devices often means resetting the device. It creates disruption, and businesses often have no patch window to make this happen. It also assumes that the devices are capable of automatic patch management, something Van Schalkwyk says is not the case.
Will this impact the move to more remote working?
COVID-19 has changed the networking landscape. There are more workers at home than at any previous point in time. When offices were first closed, organisations scrambled to help them connect. IT security teams were re-tasked to general IT support as help desks were overwhelmed. Organisations also discovered that they lacked VPNs, managed end-user devices, endpoint protection software, load balancers and software licences. How much of this did NTT see?
Unfortunately, getting a fuller view of the impact on the network is not part of this data set. That’s because it was gathered before the full hit of COVID-19 became apparent. However, the report does show some of the early impacts.
Lopez said: “There is absolutely no doubt the first response to of COVID was about a response. They were getting VPN capacity to the right applications. We ended up doing a lot of load balancing solutions because the traffic patterns just totally changed. A few clients are now looking at this as an opportunity to relook and redo network provision.”
Van Schalkwyk says that it has prompted some customers to accelerate projects: “Projects earmarked for later on in the year, September, October time-frame have been brought forward. It is mainly around things that are disruptive to users such as access, switch deployments, wireless deployments, etc. We’ve got several clients across Australia, Europe, US Asia, who’ve pushed projects forward. “
Is SD-WAN the future solution clients want?
SD-WAN has been around for a while and has yet to really take off. Even now, Gartner and others predict its market share by 2023 to be under US$5 billion. Compare that to the enterprise networking market which ResearchAndMarkets say will be worth in excess of US$100 billion by 2026
Is NTT Ltd seeing customers wanting to move to SD_WAN?
Van Schalkwyk: “We are seeing clients deploy SD-WAN on top of MPLS, and it increases and enhances the security posture. As you start decentralising your network a little bit, your perimeter becomes a bit fuzzier. You have multiple Internet breakouts, which means your attack surface increases. It also means that you need to start looking at distributing your controls a little bit more, which means lots of small firewalls instead of one big firewall.
“SD-WAN fits right into that model where you have one policy, you push everywhere, and everything is defined. Clients that are typically still trying to do things by CLI there’s not much that’s policy-driven. That’s really a significant benefit that they get in moving towards SDN. It’s an architectural approach.”
Lopez commented: “In the Managed Services report we did, there was a big trend around clients looking at adopting SD-WAN. At the moment, I think something like 40% of those clients will partner probably predominantly with their existing telco in terms of where they’re at. Only 25% are looking at what we would call an overlay service to SD-WAN. We think you need a hybrid of the two.”
Enterprise Times: What does this mean?
The report and the conversation with both Lopez and Van Schalkwyk reveal an uncomfortable truth about technology refresh. Focus too much on the new and shiny, and you forget what you are still reliant upon.
For the technology industry, which is rushing to launch new cloud-based products to meet customer demand, that has meant losing site of the state of their network infrastructure. In turn, that has made them more susceptible to attack, as the NTT GTIR shows.
Technology is not alone in this sense. Healthcare has its own problems with vulnerabilities caused by ageing and obsolete equipment. While it is stretched to the limit both physically and financially in dealing with COVID-19, it is also under sustained cyberattack. Those attacks are exploiting that ageing equipment to gain a footprint into healthcare sites and launch attacks.
Other industries, such as manufacturing, need to pay attention. The amount of equipment that is vulnerable is growing. As the world returns to work, attackers have been using those security gaps to plant malware for exploitation later.
Perhaps the more worrying part of this report is that it shows, over five years, that this is not a one-off problem. Some industries are slow to respond to the challenge while others appear to have mass replacement programmes. The issue for the next few years is that there won’t be money to fix this. The global lockdown is likely to leave many organisations, public and private, scrambling to stay afloat.


























