
It appears that it is not just endpoint security software that is unable to protect users. AdGuard has discovered that its own software, and that from other ad blocking companies, is being bypassed by cybercriminals. It has discovered a project called CoinHive Stratum Proxy that provides a method for bypassing ad blocking.
The company reports that there are around 2,500 downloads of this code per day. This is likely to be for more than just cryptojacking. Downloads are also likely to be used by other cybercriminals for malvertising. It is also entirely possible that some websites are using the code to boost the number of ads that they serve. With many advertisers paying per impression of an ad, there is a lot of interest in improving ad serving.
Countering cryptojacking with new rules
To deal with this threat, AdGuard has improved the security rules in its software. It now claims it can detect cryptojacking even if the site tries to hide it. Users are presented with a warning (see below). They can then stop the malware from running.
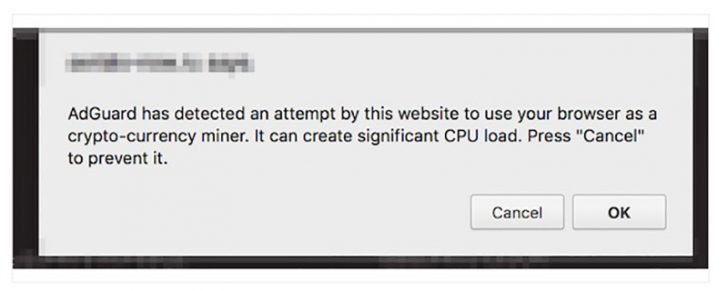
The downside is that this only works with some browsers. It cannot be used with Firefox. AdGuard also says that limitations in iOS prevent it from protecting iPhones and iPads.
Outing four sites with 992 million visits per month
To get the most out of their code, cybercriminals need to capture lots of machines. AdGuard has discovered cryptojacking code on four sites with a collective 992 million visits per month. It believes that this would allow those sites to earn over $326,000 per month if they were mining Monero.
Three of the sites are media streaming sites. AdGuard has said that it does not believe that the sites are actually complicit in delivering the code. All this means is that they have poor security controls. The code is being delivered through the media players that the sites use. If they are not checking the code then they could also be delivering other malware to users machines.
The four sites named are:
- Openload: AdGuard detected cryptojacking code on openload.co and oload.stream. The latter hosts adult videos. Between them the two sites have 330 million visits per month. Of more concern is the fact that the Openload player is used by a lot of other sites to play embedded video. This substantially widens the number of users that could be affected. The cryptojacking code is loaded from a number of .bid domains.
- Streamango.com: The same code that affected openload.co is present here. It has 42 million visits per month. As with openload.co, code is downloaded from several .bid domains.
- Rapidvideo.com: Mainly used in Germany it has around 60 million visits per month. In this case the code was identified as being a CoinHive clone known as Coin-Have. AdGuard even identified the purse where coins are delivered and estimated it makes around $25,000 per month.
- OnlineVideoConverter.com: Ranked 119 in the world for popularity it gets 490 million visits per month. As soon as a user converts some content the cryptojacking code runs. It continues to run while the video is being downloaded to the user. The slower the connection, the longer it runs. It is using another CoinHive clone – Crypto-Loot. This site is capable of earning $200,000 per month.
What does this mean?
Users need to pay increasing amounts of care as to the sites they visit. Keeping their ad blocking and endpoint security software up to date is critical. But this goes beyond just a few sites. The use of media players means that the cybercriminals can reach out long after the user has disconnected from the first point of contact.
AdGuard suggests that the ultimate solution lies with the browser owners rather than the users. It says that Chrome developers are looking at a solution but so far nothing from the likes of Microsoft, Apple, Firefox or others. Meanwhile, as the surge in demand for cryptocurrencies grows the problem will only continue to get worse.


























