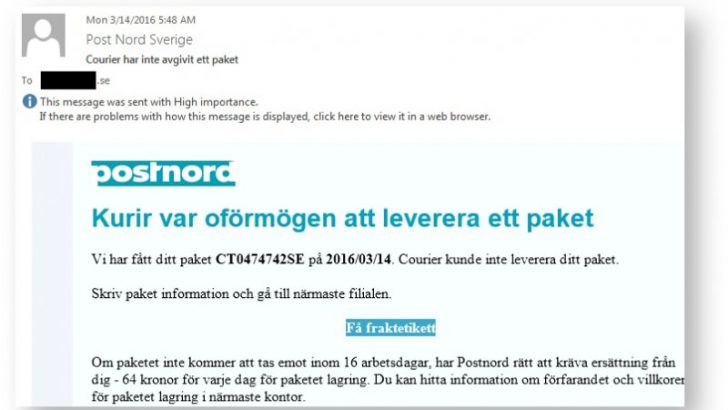
Forcepoint has reported that they have seen a resurgence of crypto ransomware TorrentLocker targeting users in Sweden and Italy. Initial reports suggest that users are being asked to pay up to $500 to have their computers released.
The announcement of the resurgence came in a blog from Nicholas Griffin at Forcepoint. In it he says: “Since 14/FEB/16 we have been tracking a new TorrentLocker e-mail campaign which has been using PostNord and Enel themed lures.” Griffin has posted examples of the emails that have been sent to users and describes the process of infection. This involves the user clicking on a link in the email where they are taken to a website which then downloads the malware.
The attacks are professionally done but will only affect people in country. Click on a link from outside of Sweden and Italy and Griffin reports that you are directed to Google. Inside the two countries users are directed to a website that is hard to distinguish from the official website. Griffin says that this is because: “the fake sites are being hosted directly on the compromised websites themselves.”
Even when the user visits the fake site they are still not infected. According to Griffin they still need to complete several other steps before finally being redirected to a site, hosted on Yandex, from where the malware is finally installed. The number of steps involved is interesting. Most malware relies on keeping it simple and using targeted phishing attacks for the best results. This move by TorrentLocker suggests that the organisers behind this scam are deliberately making this more complex in order to convince people it is genuine and not a malware attack.
Forcepoint advice to avoid infection
In Griffin’s blog Forcepoint give four ways that users can avoid being infected:
- Not clicking on a link inside the e-mail lure and instead deleting the e-mail
- Identifying that the site they are taken to is fake and not entering the captcha code
- Identifying that the ZIP file downloaded is suspicious and not opening it
- Not opening the executable inside the ZIP file
In the blog, Griffin not only lists compromised sites from which the TorrentLocker infection starts but also the two locations and command and control sites that it uses. This information should provide network administrators with the opportunity to block those sites and provide protection to their users.
Conclusion
This is an interesting change of approach by malware writers. They have decided to keep the target audience small and have linked it to business processes that require several steps with the malware only getting installed at the end.
The fact that the PostNord and Enel websites have been compromised and are serving up malware will be embarrassing to the two companies. Webmasters need to constantly check pages that are serviced by their websites and do more to keep them secure.
What isn’t clear from the blog is if this is a Windows only attack or whether the attackers are now targeting mobile devices, Linux and Mac users.
























