IBM has announced the IBM Cloud Security Enforcer, a product designed to reduce the risk for users buying into cloud and help IT know where corporate data is going.
In a survey across the Fortune 1,000 companies, IBM Security discovered that 1 in 3 employees spoken to admits to regularly saving and sharing company data to external cloud-based services. The younger the employee, the more likely they are to see cloud as an extension of their existing technology world. Many of those services are outside of the control of the IT department being paid for either by the user themselves or the Business Unit in which they work.
The term that has evolved to refer to this use of external cloud services outside of IT control is Shadow IT and it comes with a range of problems. Among those are the fact that users often use their corporate security credentials (username/password) to save them having to remember multiple logon details. There is no control on what data is stored, where it is stored and how it is stored. This means that data is being moved out of the company with scant or no regard for compliance and other security requirements.
How bad is the problem
IBM has not provided any details on the number of cloud services it believes are being used inside the Fortune 1,000 but US company Skyhigh Networks has. It’s recent Cloud Adoption and Risk Report for Q2/2015 (registration required) looked at data from over 21 million corporate users globally.
It found that the average number of cloud services used by companies is 1,083 up 46.7% than the same period last year. That equates to an average increase per week of 6.6 new cloud services per company. The issue here is not the uptake of cloud services but the security challenges that Skyhigh calls out.
Of the 12,000 services Skyhigh tracks in its registry:
- 7.0% are deemed enterprise secure
- 15.4% offer multi-factor authentication
- 9.4% encrypt data at rest
- 2.8% have ISO 2001 certification
IBM will have its own detailed numbers gathered by the X-Force team but at time of writing these were not available.
What is clear is that the use of cloud services while it is attractive to users is a major risk to users and businesses. For ANY company doing business inside the EU the provisions of the General Data Protection Regulation (GDPR) means that they will have to know where data is stored and ensure it is protected. Any failure could cost up to 5% of global turnover.
Enter the IBM Cloud Security Enforcer
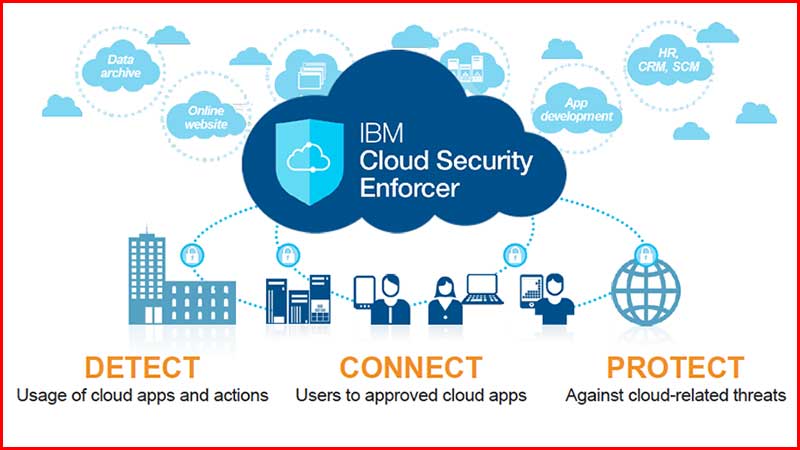
The challenge to IT getting involved in sorting out this mess is that the majority of users see them as a blocker not an enabler when it comes to cloud. What IBM is offering with the Cloud Enforcer is the ability for IT to detect, connect and protect users and data. The goal is to use a light touch which is ironic with a product using the word enforcer in the name.
IBM Cloud Security Enforcer is a Software as a Service (SaaS) solution that is linked to IBM X-Force and delivers the following:
- Detect: Identify the cloud apps that are being used and provide analytics as to how often they are used, who is using them and what data is being sent/received. Using information from IBM X-Force it creates a risk assessment around the cloud app or service. It will also gather a lot of usage data that will enable IT to relate activity and behaviour to the user. This is essential in being able to identify any suspicious activities and spot potential security issues. Much of this data can also be exported to the IBM Security Intelligence tools .
- Connect: Using the risk assessment profile of the cloud app, IT can decide whether to allow, restrict or block access. It can also apply policies to the cloud app in terms of the type of data that can be shared or consumed by the user. IBM also wants to use this data to populate a corporate app catalog from which users can select the app they want to use.
- Protect: This is where the detail in terms of cloud app reputation and risk is provided. It will allow IT to not only make its own assessment but also provide users with an explanation of why an app is being blocked or restricted. Risky behaviour is not just about the app. The information gathered here will allow IT to identify when a user is sending too much data out and/or to too many apps. This could indicate suspicious or even criminal behaviour.
Implemented properly and with a process than helps educate users, there are significant benefits for the enterprise and IT. It should remove the ‘blocker’ tag that is often applied to IT while raising the security awareness around the enterprise. Not everyone will get it but with the right analytics, any blocking of an app or even restriction placed on a user will be easily justifiable.
Making cloud a safer place to operate
The overall goal here is to make the cloud a safer place to work and store data. But relying on cloud app vendors to do all the work themselves is unrealistic. Many are small companies who might be on platforms that deliver data encryption at rest but don’t have secure or enterprise grade connectors.
As part of IBM Cloud Security Enforcer there will be a range of connectors to popular cloud apps that IBM has built itself. These will be easily deployed by the IT department and should help to integrate cloud apps with existing on-premises applications.
The integration with IBM X-Force for Threat Intelligence and Security Intelligence will also be welcomed by many companies who struggle with the amount of data they have to sift through to make this work. With IBM providing the basic data for risk assessment and helping to interpret network and app usage to identify suspicious behaviour, this should help strengthen existing security systems.
Cost and on-premises deployment
IBM is going to be making this available through its own App Marketplace. It has told analysts that the target price will be $6 per user per month which is likely to come down for very large enterprise customers. At that price, it is very attractive to a much wider market and it will be interesting to see how quickly IBM can get traction outside of its traditional large and medium sized customer base.
The other thing that we don’t yet know is if IBM will make this available as an on-premises cloud solution for private cloud customers. There is no reason why it can’t as it can still gather usage and behavioural statistics for cloud apps anonymously. It will certainly meet the demand of a lot of very large enterprises and even IBM’s growing service provider customer base.
Conclusion
Since Brendan Hannigan announced at IBM Edge in March that he had complete control over the IBM Security Division including all of the tools that it included, the IBM security business has been in overdrive. This is the first really interesting cloud application to come out of the new IBM Security Division and it will hopefully not be the last.
Helping IT departments track the risk and usage of cloud applications and then apply controls without being seen as a blocker is a major step forward in resolving the Shadow IT challenge that cloud presents. It will be interesting to see just how well IBM does over the next six months and what it delivers next.

























[…] More Detail from Ian Murphy at Enterprise Times […]