
That warning is based on a static IP address or a domain name that an organisation can register with the NCSC. While it will primarily focus on assets based in the UK, there will be some information for assets that are non-UK based.
The emphasis is then on organisations to resolve the information provided to secure their networks. What is not clear is how the NCSC will respond if an organisation fails to take the action suggested. Will it then contact the organisation to ascertain why nothing has been done?
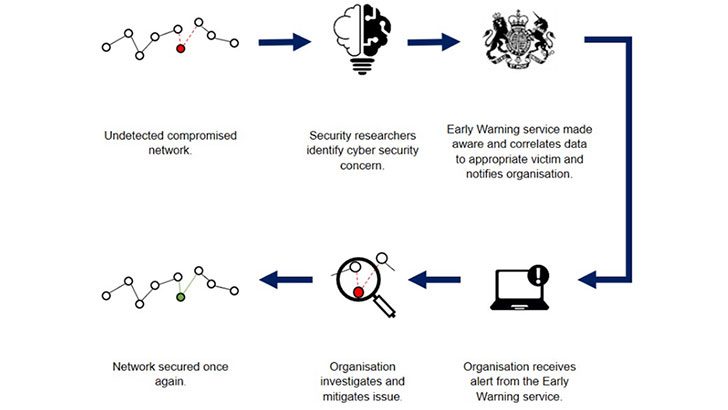
How will the Early Warning service work?
The Early Warning system is fairly simple. Issues are detected by security researchers and posted into threat feeds. This is analysed by the NCSC, which then sends an alert to an organisation. From there, it is down to the organisation to investigate and remediate.
The NCSC says it will provide two types of alert to organisations:
- Daily Threat Alert – this includes Incident Notifications and Network Abuse Reports
- Weekly Vulnerability Alert – this includes Vulnerability and Open Port Alerts
The NCSC has provided a little more detail on what those alerts contain:
- Incident Notifications – This is activity that suggests an active compromise of your system. For example, A host on your network has most likely been infected with a strain of malware.
- Network Abuse Events – These may be indicators that your assets have been associated with malicious or undesirable activity. For example, a client on your network has been detected scanning the internet.
- Vulnerability and Open Port Alerts – These are indications of vulnerable services running on your network, or potentially undesired applications are exposed to the internet. For example, you have a vulnerable application, or you have an exposed Elasticsearch service.
How do you use the service?
Organisations need four things to sign up for this service.
- An NCSC account which they can create on the website
- The name of the organisation
- The organisations static IP address or domain names. The former is not a given. For example, ISPs do not allocate static IP addresses by default. Most, like Virgin Media and BT, charge extra for a static IP address
- Who the alerts are to go to
In addition to this, an organisation will need someone capable of understanding the information provided by the NCSC. This is not a given for small businesses, so it will depend on whom it outsources support to. Many SMBs use MSPs to look after their cybersecurity. They will need to tell them that they have signed up for this service and register the MSPs contact email address.
Enterprise Times: What does this mean?
This is a good move by the NCSC and has the potential to improve security, especially for SMBs. However, there are also challenges. For example, the information must be easily actionable, especially for smaller organisations. It also has to have value. If there are too many false positives or the threat data is hard to interpret, it will not be used.
There is also the question of making sure organisations remediate the alerts. If they don’t, what will the NCSC do? There is no process for escalation listed in the service description. Will it just hope that constantly telling people they have an issue will eventually result in a fix? It is the inevitable flaw in this kind of service, and the NCSC needs to have a workable response.
























