
It is not just Android exploits that Zerodium is targeting. The company has also increased its pricing for WhatsApp and iMessage (zero click) attacks.
Zerodium promises to evaluate and verify submissions within one week or less. It also gives the option of being paid in cash or cryptocurrency. The latter, of course, is likely to appeal to many researchers who will want to stay off the radar of governments or other organisations.
Who are Zerodium?
If you haven’t heard of Zerodium before, you are not alone. They are one of several businesses who buy up exploits, verify them and then sell them on to institutional clients. Most, if not all of those clients tend to be government agencies.
In an FAQ, Zerodium says that its customers are: “mainly government organizations in need of specific and tailored cybersecurity capabilities and/or protective solutions to defend against zero-day attacks.” Of course, these are also the same organisations that want access to these exploits for offensive purposes.
What is Zerodium offering?
In its latest changelog (dated 3rd September 2019), the company lists what it is looking for and what it is willing to pay. Top of the agenda appears to be exploits that are zero click, in others words, require no user interaction. These exploits are hard to defend against, hence their popularity.
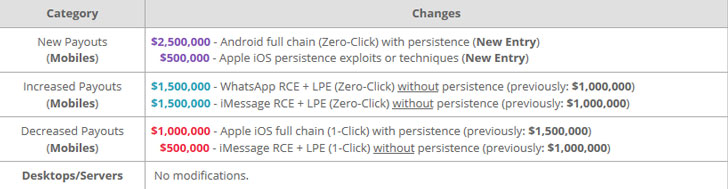
Interestingly, only payouts for mobile exploits have changed. It shows how much emphasis is being put on the changing use of technology. There are 6 different types of attacks against mobile apps, iOS and Android that could earn between $1m and $2.5m. Compare that to exploits against servers or desktops where just one – Win RCE Zero Click – is worth up to $1m.
This is not a bug program
For security researchers looking for a big payday, this is NOT a bug bounty programme. That should be evident from the sums on offer. Very few bug bounty programmes make it to $100,000 let alone $1m or higher.
Apple, for example, is rumoured to have once paid out $200,000 for details of firmware bugs. However, on the software side it pays far less. Microsoft has previously said it will go to $250,000, far less than the $1m that Zerodium has on offer for the Win RCE Zero Click.
Google, Facebook, Twitter, SAP, IBM, Intel and others are often loathed to say what their maximum is. However, the majority are under $100,000 with smaller software vendors paying out much smaller sums.
Importantly, Zerodium is paying above some of the prices being quoted on the dark web. However, getting reliable prices from such sources is tricky. It would not be a surprise to see some nation state backed groups with significant budgets to buy exploits that they could then weaponise.
Enterprise Times: What does this mean?
There will always be a place for security researchers to earn money on the side. Zerodium is not the only player in the shadowy world of exploit acquisition. For some security researchers, the size of the payouts is likely to be very tempting. Some will justify taking the money as a business transaction. The challenge is how to get software vendors to improve their bug bounty programmes to compete with these payouts.
























