Industrial Control Systems (ICS) and Supervisory Control and Data Acquisition (SCADA) systems are being increasingly targeted by attackers involved in terrorism and cyber warfare. Besides factories, these systems run critical infrastructure like power plants, water treatment systems, and traffic control systems. At stake is not just financial loss and brand reputation. These attacks can result in national security threats and even death.
Based on our experience when evaluating ICS and SCADA systems, we almost always find security weaknesses that can be easily taken advantage of. These weaknesses allow the ICS components to be manipulated and controlled beyond intended parameters. The root of the problem can be traced to:
- Patching: Unable to install the latest patch because it is not approved by Original Equipment Manufacturer (OEM).
- No or weak authentication: Any device that is connected to the network can change value and configuration of PLCs. Authentication can be easily bypass.
- Backdoors: Use of undocumented and unrestricted access to critical functions.
- Buffer overflow: Poorly written software that allows restrictions to be bypassed or manipulated.
- No encryption: Data and information can be read easily for manipulation.
The previous best-practice for ICS systems was to keep them segregated (air-gapped) from IT networks and to prevent outside interference. However, we are seeing ICS networks increasingly being connected to the IT network. This convergence event is exposing ICS systems to threats and vulnerabilities that was previously protected through isolation.
Identifying the industry’s security needs
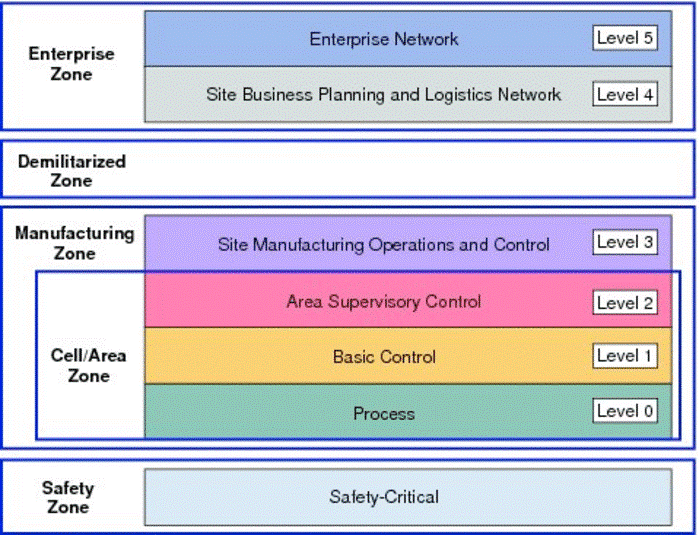
One way of managing this convergence is to group devices based on functionality and manage the access at each level. The Purdue Model for Control Hierarchy uses the concept of zones to divide enterprise IT and ICS devices into logical segment based on functions. It provides a model to identify five zones as shown in diagram below.
Let’s take the example below. We have an IT network and an Operational Technology (OT) network with two ICS environments.
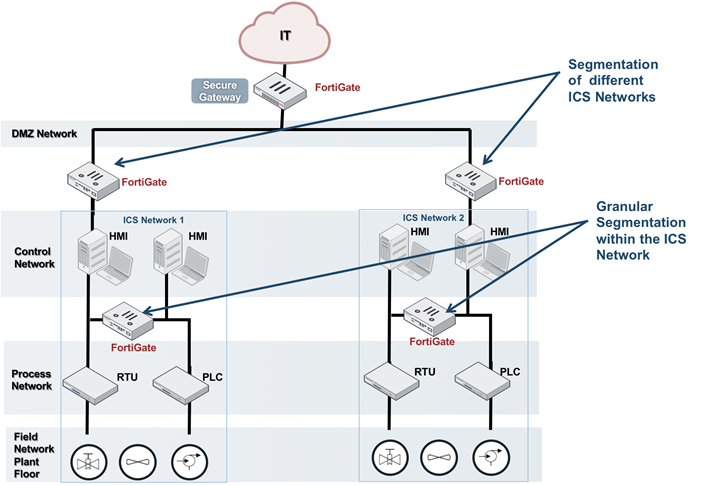
- Demilitarized Zone (Level 3.5). This first line of defense in isolating the OT network from IT network. This is a critical segmentation because IT network are generally targeted before OT network.
- Manufacturing Zone (Level 3). This segmentation protects each ICS system / remote sites / factories. The purpose of this segmentation is to keep these sites operational even if other ICS systems / sites come under attack.
- Cell Zone (Level 2). To further increase resiliency of each ICS environment, each functional cell or production line within the ICS network is further segmented. This ensures that if a functional cell is attacked, other adjacent functional cells are still functioning.
By placing Fortinet’s FortiGate Nextgen Firewall at strategic points within the ICS network, we can granularly segment different zones. This creates an extra layer of protection for the devices, and protects the data flow and communications between them. In addition, FortiGate has specific ICS / SCADA-aware functionality. This functionality allows FortiGate to identify most ICS / SCADA traffics, and stop bad traffic.
Examples of how FortiGate can improve resiliency on ICS network are:
- Allowing only Workstation_A to write to HMI_A
- Block HMI_1 from communication with PLC_2
- Identify and alert if a Modbus protocol has been modified maliciously
- Alert on all write command
Finally, FortiGate comes in an industrial grade and compliance ready. It meets EMI, Thermal, and Vibration standards as outlined by IEC61850. It is also available in rugged physical appliance that can withstand the harshest environmental conditions.
FortiGate’s functionality is further enhanced when it integrates with other Fortinet Fabric Ready technology like OT-IDS, SIEM, and Risk Management software. By integrating into Fortinet Fabric Ready technology, FortiGate achieves even higher enforcement granularity, perform earlier threat detection, and faster threat remediation.
NTT Security, as a global leader in security services, understands these challenges. Our aim is to assist clients in operationalize security solutions, and also to prepare for the eventual IT/OT convergence.
NTT Security is the specialized security company and the center of excellence in cybersecurity for NTT Group. With embedded security we enable NTT Group companies to deliver resilient business solutions for clients’ digital transformation needs.
Poh Chang Chew, Fortinet’s Consulting System Engineer in Asia Pacific.
Poh Chang has over 19 years IT experience with 13 years Info Security and 6 years in Virtualization & Cloud. He has been working in a regional role within Asia Pacific for the last 11 years. Poh Chang is currently with Fortinet as a Principal Consultant for Industrial Cyber Security/Critical Infrastructure & Global Alliances APAC. He also has experience in Cyber Security Management, ISO 27001, PCI and BC/DR. Poh Chang also shares best practices, governance and compliance with Critical Infrastructure industries and in regional conferences.