Comodo Threat Intelligence Labs has uncovered a fourth wave of IKARUSdilapidated Locky ransomware attacks. Like previous waves, it is driven by botnets and uses an unknown file extension to bypass security software. The botnets are using a social engineering-based phishing attack targeting both businesses and individuals.
The email uses the title Supplement Payment. It appears to be coming from a legitimate source which increases the likelihood of users opening it. Whether the attackers are using sources they know are relevant to the individual is not clear. It could be they are using spoofed email addresses from large organisations. Alternatively they could be targeting the emails using data stolen in one of the recent large breaches.
According to the authors of the report: “The social engineering aspect involves the botnet sending emails to busy workers appearing to be about a “Supplement payment” from a legitimate source. As with the other IKARUSdilapidated attacks, clicking the attachment ultimately encrypts the victims’ computers and leads to a bitcoin ransom demand.”
Asasin is yet another short sharp attack
In line with the other attacks that Comodo has spotted this attack lasted for just a couple of days. It started on October 11 and ended on October 13. This use of short sharp attacks is likely to be an attempt to reduce detection by web-based security software. It is also possible that the attackers have a limited budget for renting the botnet.
Interestingly there is about a 7% reuse rate of IP addresses across the four waves of attack. This could be because some computers are enrolled in different botnets. More likely is that the attackers are renting just part of a much larger botnet. This suggests two things. The first is that they have limited funds. The second is that their success rate is low which, in turn, reduces the funds available to them.
This time around the attackers managed to mess up the attack. According to the report: “.. the person or team distributing these emails was not adding the attachments correctly, causing the attachments to not be visible to the recipient when opened. Instead, they appeared as a blob of base64 encoded text as shown in the image above.”
Why this happened is not clear. The pattern and design of the attacks suggest that this is the same team each time. This view is also reinforced by the way the code is changed to defeat security teams and software. Importantly the changes are also defeating machine learning algorithms making these attacks more serious than might be thought.
There is still an attachment for users to click on and, like previous versions, it uses VB Script and unpacks a number of different files.
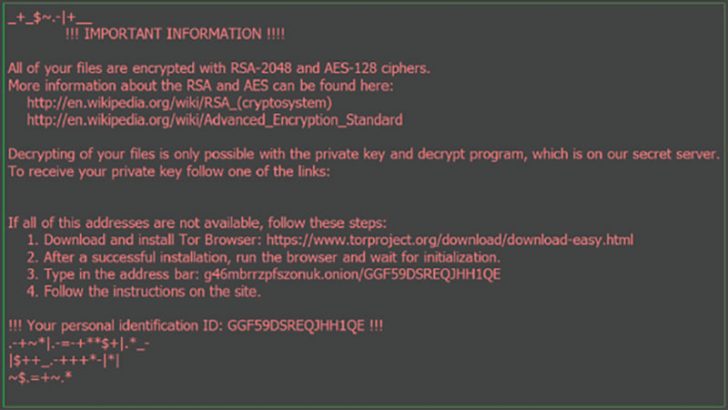
Educating users about encryption
In a strange move, the ransom screen appears to redirect users to Wikipedia to learn about encryption ciphers. It provides two links to pages on Wikipedia which are valid. Neither page appears to have been modified or tampered with. This is not, therefore, an attempt to create a secondary attack but just an infomercial.
Below that is the details of how to pay the ransom itself.
Who is targeted and where are the emails coming from?
The heat map of this attack shows the same global range as the other IKARUSdilapidated attacks with minor variations. This current attack shows India as the most common starting point with Vietnam second.
The attack also shows that ISPs continue to be co-opted as part of the attack. This raises a serious question as to why they are unable to deal with attacks across their networks.
What does this mean
Short sharp attacks are harder to spot and can be destructive. In the case of IKARUSdilapidated, security companies, including Comodo, are watching for it. The fact that the attackers appear to be using portions of a large botnet to launch their attacks from is interesting. It does imply either careful planning or restricted access to the botnet.
The success rate of the attacks is not known. Comodo has given no indication of the number of users it believes have been infected or who have paid. There is a growing difference between the two as organisations develop anti-ransomware defences. Individuals are more likely to pay as they often do not have copies of their data. However, the high cost of bitcoin is also doing its bit in reducing payment.
This is an attack that seems unlikely to go away until either the authors get caught or the botnet is shut down.

























