Security solutions and digital certification vendor Comodo has reported yet another wave of ransomware attacks. This latest campaign uses the same Locky variant, IKARUSdilapidated, as in previous attacks reported by Comodo. The campaign started on the 18th September and stopped on the 21st September. That does not mean it is over. It is likely that there will be plenty of emails sitting and waiting to be discovered by unsuspecting users.
How does Locky get installed?
As with previous campaigns, the attack was carried out using a zombie botnet. It was used to send emails to users pretending to be from partners and printers. The use of emails pretending to be from printers is nothing new. In this attack, an email with an attachment from a Konica Minolta C224e printer is sent to a user. The subject line is “Message from KM_C224e” and it contains an attachment but no message body.
The second attack focuses on an invoice apparently from a business partner. It has a subject line of “Status of Invoice A2171771-07”. It is not clear if there are other invoice numbers in use.
Both emails rely on several points of user interaction to work. The emails have to be opened. The attachment needs to be clicked on. As the attachment is a compressed file, it then has to be unpacked. At this point it drops its payload and starts to encrypt the local machine.
All of these are points where users should be questioning if they need to do it. Unless the sender email address makes sense there is no need to open the email. It might seem unreasonable to expect the user to know the model of the printers in the office. However, if you haven’t scanned a document, why are you opening the email? Similarly for the invoice. If you do not recognise the name of the company who apparently sent the invoice, why are you opening it?
Once the attack is underway the ransom demand varies between .5 bitcoins and 1 bitcoin. In real money that can anywhere from $2,000 – $4,000 (£1,500 – £3,000). This is not a trivial attack and can have a significant impact on small businesses.
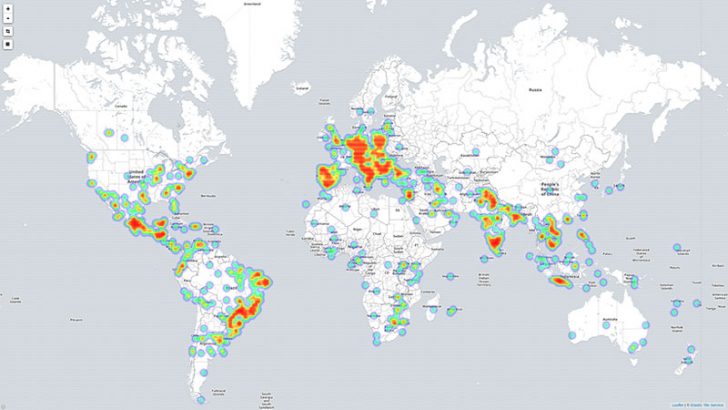
Which countries are being targeted and from where?
The heat maps for both attacks show a lot of overlap. The attacks show Europe, the US, South America, India and parts of Asia have all been heavily targeted. The similarities to other attacks in the spread of countries suggests that the attackers are reusing an existing list of email addresses. These might have been culled from the Internet but equally are likely to have come from one or more breaches.
Vietnam and Mexico account for the vast majority of the emails spreading the attacks. This is no surprise as both companies have been heavily implicated in botnet activity for some time. What is a surprise is that so many emails were not detected by email security systems. IT departments have to get better at detecting and remediating phishing emails before they reach users.
What is interesting is that Comodo reports the attackers are adapting to a new generation of security tools. They are modifying file extensions and using short campaigns. These both reduce the effectiveness of machine learning and pattern recognition systems.
What does this mean
Once again we have a ransomware attack relying on phishing emails. They are not very sophisticated emails and rely on users clicking on attachments and agreeing to unpack the malware. Simple security training should prevent this type of attack as should better security checking of emails as they come in.
The price of bitcoin is now stabilising around to $4,000 (£3,000) mark. That means that attacks like these can have a serious financial implication for companies. It also means that attackers will continue to keep coming as it is getting more and more lucrative to run a campaign.

























