In a security blog post Microsoft has warned that: “Every month, at least three million users of various platforms and software encounter tech support scams.” The company has also warned of a change to the way that the tech support scams operate. Scammers are moving away from the scripted phone calls that have been widely publicised. They are now sending emails with links that redirect victims to tech support scam websites.
The data was captured by the anti-spam filters in Microsoft Exchange Online Protection (EOP) for Office 365 and Outlook.com. Microsoft says that the emails were blocked: “because they bore characteristics of phishing emails. The said spam emails use social engineering techniques—spoofing brands, pretending to be legitimate communications, disguising malicious URLs—employed by phishers to get recipients to click suspicious links.”
What is the tech support scam?
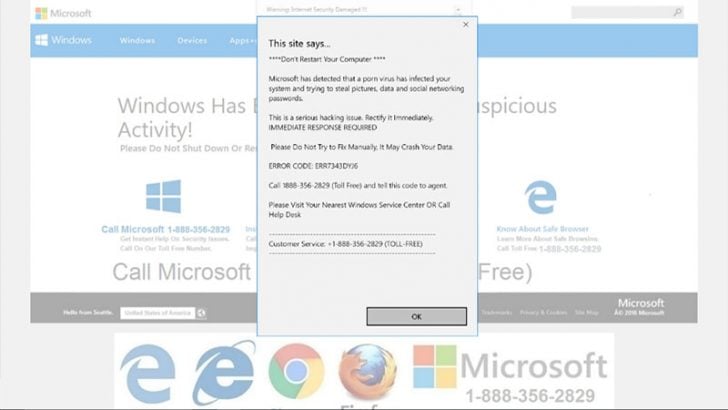
The tech support scam tricks users into believing that there is a problem with their computer. There are various routes to infect users. The scammers cold call pretending to be calling from vendors such as Microsoft or the victims ISP. Alternatively, they use a spam campaign or pop-ups to display system messages suggesting the machine has a serious problem. The latter form of communication often contains a phone number to get the problem solved. They can also use malvertising, fake adverts that install malware on computers when users visit the webpage on which they are hosted.
The victim is told that a problem has been detected and needs to be fixed. If it is not fixed they are told that they could be denied access to the Internet. It preys on those who are less computer savvy and relies on social engineering to get them to do what the operator tells them.
The tech support scam operator will attempt to get the victim to allow remote access to their computer. At that point the scammers use information on the local device along with jargon to make it look as if there is a serious problem. The victim is then asked for a one-off payment, often via a credit card, in order to resolve the issue.
What is Microsoft seeing?
The new email campaigns use reputable brands to trick users. Microsoft has published some of the emails it has captured. These appear to come from big brands such as Alibaba, Amazon and LinkedIn. They all contain links that if examined are not to the sites they claim to be from. The reason these emails succeed is that people often take the email at face value, trust the brand and just click on the link without thinking about it.
Once the user opens the infected link that redirect the user to the tech support scammers website. This then displays a pop-up message that looks like a real alert and asks the user to urgently call a number. The user cannot close their browser because the scammers have used a dialog box that keeps reloaded and preventing the browser being shutdown.
What can users do?
There are various steps the user can take to prevent being a victim of a tech support scam.
- Never give remote access to your computer.
- Do not call the telephone number in the dialog box. Software companies do not put telephone numbers in their error messages or alerts.
- Keep your anti-malware and anti-virus software constantly updated and have it scan all your emails.
- Always think before clicking links in emails. Did you really place that order? Do you know the person that LinkedIn says has sent you a message? To view the emails open a new browser window and go direct to the website. If the emails are real then they will also appear on the website as messages. If they are a scam you have just avoided being infected.
What does this mean?
While most tech support scam attacks are about just getting credit card details from a user, others are more serious. The user is giving the scammers access to their computer. That allows the scammer to install other malware on the device. If the computer is also used for work the scammer can steal security credentials or work email. They can also use it as their gateway to attack the enterprise network by connecting to it when it is in the office.
Like all scams and attacks this one is defeated by education. IT support teams should consider an internal website where they put examples of all sorts of security issues. This would allow users to self learn about risk and improve the overall security stance of the business.

























