
Sectigo claims the SDK: “cost-effectively manages, seals and stores encryption keys, passwords and other data on the device.” It goes on to say that this: “removes the risk of exposing credentials of devices lacking a Trusted Platform Module (TPM) or other hardware-based secure storage mechanism.”
Alan Grau, Sectigo’s VP of IoT, commented: “Enhanced levels of security should be available for all IoT devices to help prevent non-compliance with ever-changing legislation, device cloning, and the introduction of counterfeit devices into the market. SKS-SDK enables IoT device manufacturers to protect private keys and critical information from hackers with special attention to affordability and compliance.”
How does the SKS-SDK work?
According to the product sheet, the SKS-SDK: “uses patent-pending obfuscation algorithms to protect embedded device keys.” The product sheet sets out the process, which is shown below.
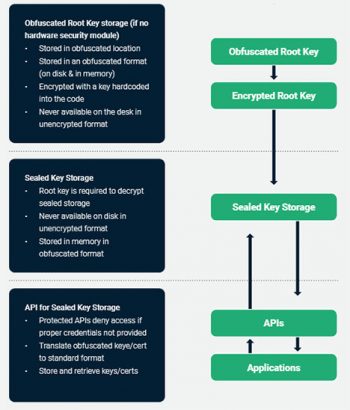
The one thing here that raises an initial question is that the process says the root key is encrypted with a key hardcoded into the code. What is not clear is how that key is then protected. Hardcoded keys are a nightmare to keep safe, and once discovered, they can lead to large breaches. It will require organisations to decide just how they will manage keys, key strength and the number of devices that share the same hardcoded key. It is unfeasible for a manufacturer, especially of low-code devices, to use a separate key for each device that they sell.
One answer to this is that SKS-SDK is a component of the Sectigo Security and IoT Identity Platform. It is a platform that Sectigo has been building out for a few years now. Both manufacturers and enterprises can deploy it to protect their sprawling IoT estates.
Enterprise Times: What does this mean?
Anything that hardens IoT devices is to be welcomed. What is most interesting here is that Sectigo is targeting device manufacturers. Unfortunately, the take up among some sections of the IoT manufacturing community is likely to be poor. Those delivering low-cost, price-sensitive devices will continue to use cost as a reason to not fix the lack of security in their devices. In the same way that they won’t spend money on an embedded solution, they are unlikely to invest in developers or software.
Where this may have a bigger impact is in areas such as industrial, manufacturing and healthcare. All have multiple generations of IoT devices, with many of the legacy devices at risk. Manufacturers of those devices are making efforts to get them secured. Rockwell Automation, Siemens, and Schneider Electric recently participated in Claroty’s US$140M Series D funding round. Like other vendors, they are also working with multiple companies to help secure their older IIoT devices.
It will be interesting to see how quickly the SKS-SDK gets adopted by companies. Sectigo has already gained traction with its Security and IoT Identity Platform. Will those using that quickly adopt the SKS-SDK as well?

























