
It is unusual to have two consecutive quarters where cyber attack numbers fall. That does not mean that the Internet is any safer. The report’s authors warn that: “What threat actors lacked in quantity they made up for in quality.” Several new variants of existing malware were seen. Some older attacks appear to be resurgent.
The headline points from this report are:
- Cryptomining is still hot, but starting to decline
- GandCrab remains the king ransomware variant
- Adware up 19% over last quarter for consumers
- VPNFilter debuts, with over 500,000 detections
- Exploits on the rise
- Scammers are increasingly targeting PII (Personally Identifiable Information)
Top attacks in Q2
Malwarebytes discusses, separately, attacks reported by its consumer and business software. This,inevitably, presents a slightly blurred picture given the continued use of Bring Your Own Device (BYOD) for business computing. It shows how easy it is for consumer malware to affect the enterprise, a threat security vendors have warned about for some time.
The table below shows the top attacks by type across both sets of consumers and bussiness, with a comparison between Q1 and Q2. The numbers, however, mask the impact of some attacks.
For example, the drop in banking Trojan attacks hides the significant risk in Emotet across the quarter. Malwarebytes claims to have seen infections highest in April and May. Check Point, by comparison, saw a significant increase in attacks in June. This difference confirms how difficult it is to compare attack reports from different vendors.
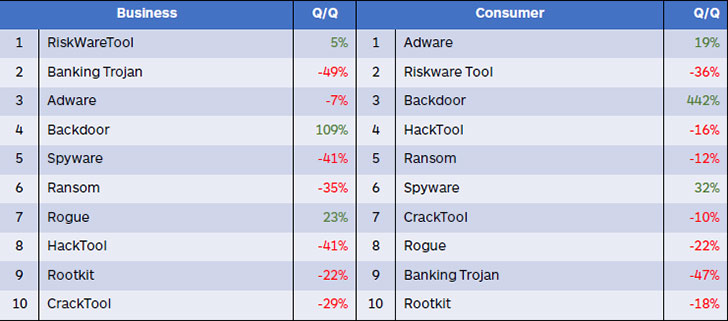
The big rise in both business and consumer attacks is the use of backdoor malware. This is attributable a single piece of malware called Backdoor,Vools. This is being used, at present, to undertake cryptomining attacks. It infects machines using the ETERNALBLUE exploit stolen from the NSA. Malwarebytes believes the drop in crypto valuations will see this malware redeployed for other forms of attack.
Ransomware attacks have shifted away from consumers and towards businesses. This is because businesses understand the value and are more likely to pay to recover their data. Malwarebytes calls out GandCrab as the ‘most popular’ ransomware it sees. During Q2 GrandCrab started to move away from email distribution to the use of the Magnitude exploit kit.
Is cryptomining losing its attraction?
Cryptomining continues to be one of the most popular attacks. The rewards are greater than for most other attacks. It is a multi-OS attack – with Windows, Mac and Android all targeted.
Browser-based attacks, using the Coinhive code, continue. Malwarebytes, like other security companies, does not separate out those sites openly using Coinhive as a revenue stream and those who are using it covertly.
There are two explanations for hy cryptomining attacks are declining. Malwarebytes sees a parallel between the value of cryptocurrencies and cryptomining attacks. If there is a sudden re-increase in cryptocurrency values then it expects infection rates to rise again. Cryptomining also requires copious resources. This may explain why attacks against businesses have grown, especially now that cryptomining malware is beginning to appear inside containers. This facilitiates cloud deployments.
CMS vulnerabilities such as Drupalgeddon have enabled browser-based cryptomining attacks to flourish. Most users of CMS systems do not update them regularly. They are also poor at securing and checking their code. The points to note are that hackers:
- make no material change to the website (so as to not alert the owners)
- they take over functions inside the CMS (and use them to push hacking code to visitors).
PII, Scams and Zero-day attacks
Now that GDPR has officially gone live, organisations are beginning to tighten up on where and how PII is stored. This is forcing attackers to find new ways to steal sensitive data.
Malwarebytes has seen an increase in scams targeting individuals to steal their PII. There is a risk that backdoor infections will see attackers deploy PII-stealing malware.
Social media continues to be used to spread scams. The use of fake accounts and shortened URLs makes it easy for attackers to target victims. There are numerous tools that will expand a shortened URL to make sure it does point to a trusted site and not a fake site.
Users need to:
- become more aware of fake stories and posts
- think before clicking on shortened URLs (even when they seem to be pointing to a legitimate website).
Q2 also saw an increase in zero-day attacks. This may be attributable to software vendors becoming better at responding to vulnerabilities. In turn this has driven up dark web bounties for new exploits – especially for Adobe Reader and MS Office.
Malwarebytes has seen an increase in zero-day attacks against both these products. Consumers and businesses must keep software patching current. Malwarebytes expects more attacks throughout 2018.
What does this mean
Q2 has seen fewer cyber attacks than Q1. At one level that is good news. It gives defenders some breathing room.
The downside is that Malwarebytes has spotted an increase in the quality of attacks. It reports on the significant rise in backdoor infections which enable attackers to install a range of different malware on a machine.
The concern here is that rise in backdoor infections. For now these appear to be confined to installed cryptomining malware. But, in the future, the risk is they could install anything on, and steal anything from, infected machines.
























