
The US Navy has announced its five year strategic plan for cyberspace. This should come as no surprise as the US looks to retaliate against hacktivists, cyber terrorists and state sponsored hacking.
What should interest businesses, Chief Information Security Officers (CISO), Chief Information Officers (CIO) and security teams is that much of what it intends to do can be transplanted to the commercial sector.
In the opening remarks of the document US Fleet Cyber Command/TENTH Fleet Strategic Plan 2015-2020, Vice Admiral Jan E Tinge, Commander, U.S. Fleet Cyber Command and Commander, U.S. TENTH Fleet said:
“New warfighting platforms do not spring full-grown from their technical roots. They may appear initially as interesting oddities, such as the first submarines. They may even start as “enablers,” such as aviation’s early reconnaissance balloons.
“Eventually… they turn a corner to realize their full potential: they become formidable warfighting platforms… The military that grasps this turning point soonest is the one that seizes the advantage. ..Today our whole force is coming to understand these two truths: our mastery of cyberspace puts a hefty weapon in our hands; and our reliance on cyberspace places a weighty vulnerability in our path.
“Recent world events have underscored this two-edged quality of cyberspace. Our adversaries are flexing their muscles and have proven the vulnerability of our assets – governmental, commercial, academic, and military – posing serious risks to our nation’s security and missions that we as a navy are executing around the globe every day.”
What’s good for the military is good for the enterprise
What is interesting about these remarks is that in broad terms they can be seen as much as a corporate IT security mission statement as a military statement. The reliance on cyberspace and the vulnerability of corporate assets is only too evident on a daily basis as company after company admits to being hacked and losing data.
Two years ago, this would have only been seen as an IT problem and something that the marketing department would need to respond to. However, since the attack on Target we have seen a significant shift in the attitude of company directors. Several senior members of the board have lost their jobs as a direct result of the attack. According to Art Wong, senior VP, HP Enterprise Security Services: “This has brought a new focus on risk and cybersecurity at a board level.”
5 goals to improve security
The US Navy has five strategic goals for cybersecurity that can be easily adapted to enterprise needs:
- Operate the network as a warfighting platform
- Conduct tailored signals intelligence
- Deliver warfighting effects through cyberspace
- Create shared cyber situational awareness
- Establish and mature Navy’s cyber mission forces
Look beyond the militaristic nature of the headings for a moment and at the detail and the ability to adapt to the enterprise quickly becomes clear. For example substitute warfighting platform for defence platform. Similarly warfighting effects becomes defensive effects. Finally replace Navy’s cyber mission forces for IT security and security partners.
To understand how this works lets look at each of these goals in more detail.
Operate the network as a warfighting (defensive) platform
The report states: “Cyberspace, in particular, poses significant challenges. Current network architecture has inherent vulnerabilities. In addition, our users don’t yet fully appreciate how their online behaviour can compromise network security if they’re not careful. Meanwhile, our adversaries are rapidly acquiring sophisticated tools, plus the knowhow to use them.”
One of the problems for many IT security teams is that the emphasis on security is still focused on preventing access to the network rather than protecting the data and changing corporate culture. In this section the report talks about the need for real-time awareness of network status and improving real-time awareness of adversary activity on the networks.
Over the last year there has been a significant increase in the talk about security intelligence and the use of big data and analytics systems to provide real-time information. Part of the problem here is the sheer volume of data that has to be gathered and sorted. Automation is essential to reducing the volume of noise to a clear set of data. There is also a need to do more analysis at the edge of the network, something that vendors are only just beginning to recognise.
IBM, HP, Symantec, Dell and other a number of other vendors are all delivering solutions to make it easier to pull data from multiple locations and look for patterns. The emergence of Managed Security Services (MSS) makes some of this possible as vendors build cloud-based platforms to automate much of the analysis.
This goes hand in hand with the need to profile activity on the system. That means understanding what individual users normally do and when their behaviour changes. The same is true of application behaviour such as unexpected connections to outside systems. Another challenge is understanding what traffic is moving across the network and with the increasing use of encryption by hackers exfiltrating data, companies are having to upgrade their systems to do packet analysis of encrypted data.
One of the most pressing steps for most companies is the encryption of all data whether that be at rest or in transit. At the very least it raises the bar and makes it harder for an attacker to easily find and exploit stolen data. It is also becoming a requirement in order to prove that a company has taken all reasonable approaches to prevent data loss.
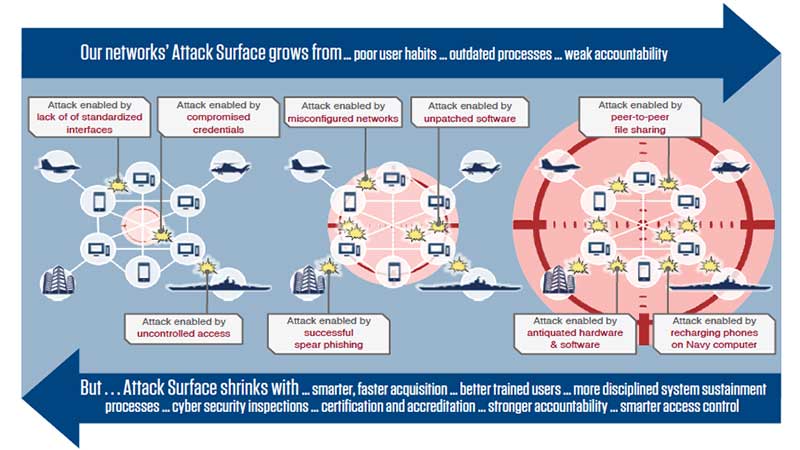
One of the key elements that the US Navy wants to do is reduce its intrusion attack surface (see image below). All of these steps are applicable to the enterprise and this image is a useful starting point for understanding the maturity of existing cybersecurity processes inside the enterprise.
Conduct tailored signals intelligence
While the US Navy talks about partnering with other parts of the US Military and intelligence services for its signal intelligence there are equally well established enterprise alternatives. The UK has recently launched its own equivalent of the US CERT website. This publishes bulletins listing vulnerabilities that IT security teams should check and then remediate if necessary. The same is true of a number of other sites and especially all of the main security vendors.
The problem is that this is often too little to late. As a result several vendors are now launching their own community solutions around threat intelligence. The idea is that customers can share information on attacks that they are seeing and the vendor backs this up with significant data from its own global monitoring services. At the moment, this is being done on a vendor by vendor basis and is reminiscent of the early days of anti-virus.
The solution is a greater emphasis on sharing between vendors and not just a vendor and its chosen partners. There are two industry initiatives in place that can help with this, STIX and TAXII. At present, IBM has committed to both with its recent launch of the IBM X-Force Threat Exchange. HP is working towards support for TAXII but is yet to publically announce its support for STIX. While both initiatives have support from other vendors, there is a lot of work to do before we see either of these as highly effective platforms.
There is also an increased demand from regulators for companies to be more open when they discover cyber attacks. Reporting requirements are being tightened across the world but many companies are concerned about the impact on their business of making attacks public before they have had a chance to remediate them.
Deliver warfighting (defensive) effects through cyberspace
The big enterprise issue here is institutionalising cyber delivery capability. Enterprises cannot respond the same way the military can but it can do much more in terms of education of users. While it is reasonable to try and automate much of the cyber protection of users, there is still a need for ongoing education of users around common attacks.
The use of passive information systems that provide details and examples of attack vectors such as spear phishing attacks and emails that look to take users to site loaded with malware is a start. The challenge is how to make this a more proactive solution and this is something that is hard to solve. Requiring users to attend regular cybersecurity classes is unlikely to work based on cost and the simple fact that too few users understand or are interested in the issue.
In many enterprises incident response plans either do not exist or are wholly inadequate. They don’t cover key systems, fail to involve all the key personnel and often lack key legal and communication elements that are required to manage a cyber incident. Where companies operate in different jurisdictions they must have detailed local plans that cover notification to the relevant authorities. Fortunately there is an increase in the number of companies that provide incident response services.
Part of the incident response is the forensic acquisition of the attack. This is a highly specialised approach that is generally beyond most internal IT security teams. Without taking a forensic based evidence gathering approach when an attack is discovered, companies will struggle to provide the information required by law enforcement to track, capture and prosecute cybercriminals.
Create shared cyber situational awareness
While the US Navy sees this as an active response service, it relies heavily on Security Operations Centres (SOC). Security vendors are beginning to deploy their own SOC around the world. This allows them to provide in-country support for customers when an attack is discovered. They also share data across all their SOC in order to detect attacks on a global basis.
Inside an enterprise there is a need for greater communication across the IT department and the board level directors. The incident response team or at least a subset of the team should also be part of this process. By being aware of changes to the risk environment they would be able to put in place plans to increase security of data assets. Should a cyber breach be detected there would then be a process and team that can respond quickly and appropriately.
It is interesting that the US Navy highlights the need for a unified data strategy and the need for analytics to feed cyber situational awareness. Real-time monitoring of users, applications and the network tied to analytics along with profiling meets this need and should be part of any enterprise security plan.
One of the tools that the US Navy is targeting is visualisation and this is something that can only benefit IT security teams. Visualisation is beginning to mature in the big data and analytics market and tying this to real-time security information will make it easier for security teams to spot attacks and respond according.
Establish and mature Navy’s cyber mission forces
Of all the challenges facing enterprises this is likely to be the hardest to solve. There is a drastic shortage of skilled personnel available to companies today and this means that there is intense competition for staff. The result is that salaries are increasing at well over 10% per year for highly qualified security experts.
For the SME market this means that they need to look to their dealers or to cloud-based MSS solutions. Even large enterprises are finding that they are unable to attract and retain security staff in the face of stiff competition from security vendors and service providers.
This is likely to be the case for the foreseeable future and it could be that we see a return to companies offering training to some staff on the basis that they will repay the costs of training should they leave within an agreed period of time after completing their courses.
Putting it all into practice
There are a number of issues that cause problems for enterprises when it comes to designing cybersecurity plans. These range from the creation of a workable plan through the the execution and then the funding.
Unlike other areas of IT where servers and software can be replaced every few years for a given costs, security is an ongoing investment. Cybercriminals operate in a highly sophisticate environment. When an attacker buys an exploit from a hacker website it often comes with guarantees and a level of customer service that can only be described as a gold standard. If it doesn’t work money is refunded and alternatives offered.
This means that Finance Directors who look at a budget allocation for cybersecurity as a one-off item are part of the problem. Unfortunately, in the current fiscal environment nobody is going to give an open-ended commitment to security teams to keep updating skills, acquiring new staff and installing new solutions.
This is driving the growth of cloud-based MSS solutions from big vendors. The problem is that these are all aimed at enterprise customers and not the supply chain or SME market.
There is a significant need for enterprises to realise that as they increasingly use software to automate business processes across their supply chain it is the weak link in their security. Wong recently told analysts that: “less than 15% [of enterprise customers] have asked us to look at the ecosystem [supply chain].”
Conclusion
The US Navy has laid out how it intends to deal with cyber warfare over the next five years. Its goals and targets are something that organisations across the globe should take serious note of as they look to protect themselves from the increasing number of attacks that they are being subjected to.


























