
The attack shows how Turla is evolving its techniques to stay ahead of security software. As part of the attack, Turla is exploiting Adobe in order to trick users. In the past, Turla has used fake Adobe Flash downloads. Now it is using a legitimate Flash Player installer and several pieces of backdoor malware.

According to Foltyn: “Not only does the gang now bundle its backdoors together with a legitimate Flash Player installer but, compounding things further, it ensures that URLs and the IP addresses it uses appear to correspond to Adobe’s legitimate infrastructure. In so doing, the attackers essentially misuse the Adobe brand to trick users into downloading malware.”
In the full report, ESET makes it clear that it has not seen any evidence that Adobe’s distribution network has been compromised. Instead it says that: “These attackers merely use the Adobe brand to trick users into downloading the malware.”
How are users infected?
Foltyn says that ESET researchers have identified several possible attack vectors. Interestingly they are unable to narrow this down to a single most common vector. Among the options are:
Man in the middle (MitM) attack: This relies on a machine inside the organisation being infected and then used to infect other machines. Vendors such as Microsoft are already looking at using peer-to-peer update approaches. This means that local machines are accepted as an update source. Taking control of this mechanism will increase the opportunity for large scale infection.
Border Gateway Protocol (BGP) hijack: This is where the attackers reroute all traffic to a compromised server controlled by Turla. Many security solutions actively scan for this type of attack.
ISP intercept: In September 2017, ESET warned of surveillance software such as FinFisher being used to intercept traffic at ISPs. Researchers think that attackers could attack ISPs and then use a similar tool to then monitor and attack key organisations.
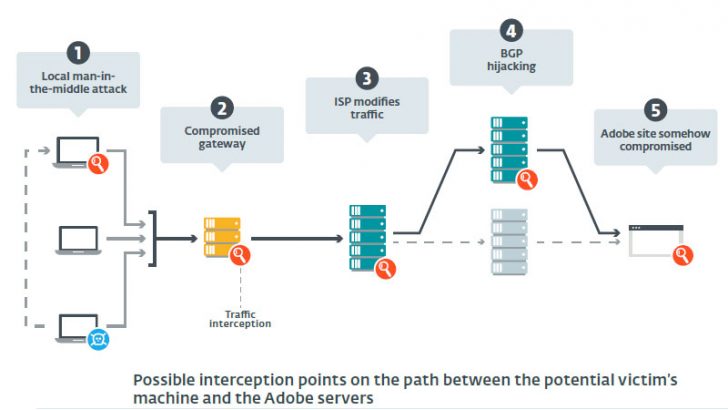
Whichever route is used the goal is to get the fake Flash installer downloaded and launched. That, in turn, downloads any of several backdoors that Turla is known to use. Once the machine is compromised data is exfiltrated. Among the data spotted being stolen by ESET is machine ID, username and the installed security products. This looks more like a reconnaissance attack than a data theft at the moment.
Advanced backdoors evading detection
Turla uses a number of different backdoors to gain access to computers such as Mosquito, Gazer and Carbon. In this attack ESET has seen the Mosquito backdoor used in the majority of cases. It also reports a smaller number of infections using the ComRAT and Gazer malware.
In Foltyn’s blog he calls out the evolution of Mosquito in this attack. He says: “The more recent iterations are more heavily obfuscated with what appears to be a custom crypter, to make analysis more difficult both for malware researchers and for security software’s code.”
One of the ways the code makes it hard is the use of arithmetic functions. These are designed to defeat the emulators used by researchers and security software. They force the emulator to take increasing amounts of time to work. From a security software perspective this can result in the code not being scanned due to time constraints. The backdoor code also checks to see if it is running on the main machine or in a sandbox.
The backdoor used in this attack also modifies the Windows registry. Among those values are details of the command and control (C&C) servers that it is using. To make it hard to identify the data, all the entries in the registry are encrypted.
One surprise to ESET is the log file that is created. It creates a timestamp for each log entry. This allows forensic investigators to backtrack and see exactly what happened and when.
What does this mean?
ESET reports that while some commercial targets have been caught in this attack it is primarily a political campaign. What is not clear is what intelligence the attackers are seeking to gather. Turla is regarded as being sponsored by Russia. Attacks on its former colonies such as Ukraine, Estonia and Georgia are not surprising. However, this attack seems to be widespread and targeting all the former East European countries that made up the USSR. This could be a distraction designed to obfuscate the real target. However, ESET has not identified any one state that has been subjected to more attacks than any other.
For commercial organisations the evolution of Mosquito and other techniques that ESET has highlighted will cause concern. Making it difficult for security software to scan files and therefore ignoring them is a real problem. It means that malicious code can live for some time inside an organisation before it is detected.
Another challenge is the way that Turla is misusing the Adobe name to distribute their malware. One thing that Adobe could do to make this harder for Turla and other attackers is to stop using HTTP and move to HTTPS. ESET says: “The usage of HTTPs would significantly reduce the effectiveness of these kinds of attacks, as it is harder to intercept and modify encrypted traffic on the path between a machine and a remote server. Similarly, a check of the file signature should quickly raise suspicion, as the files used in this campaign are not signed whereas installers from Adobe are.”

























