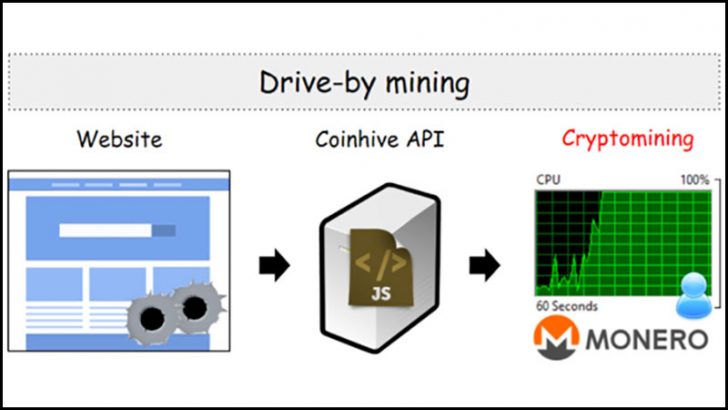
Malwarebytes has been tracking the recent outbreak of illegal drive-by mining for cryptocurrencies. This comes as no surprise. Most of the mining that has been taken place has done so without the permission of the user. As a result, security vendors are marking the software concerned as malware. At the heart of the outbreak is a service launched by Coinhive which runs in a browser.
Running code in a browser to take advantage of unused computer time is nothing new. There have been many applications that have taken advantage of this approach. Perhaps the most famous of these was SETI@HOME. Launched in 1999 it allowed people to donate spare computer time to analyse radio data from telescopes. It was followed by many others such as BOINC, Atlas and POEM. All of these took advantage of users to help process data.
Coin mining is different. The users get nothing back for the use of their spare CPU power. They pick up the bill for the Internet connection and for the electricity used by their computer. Those who control the programme get to make money off of the backs of other people. If those doing this were a charity, many users would have no problem.
Given that this is an established approach what went wrong?
Mining cryptocurrencies without permission

In a blog and report, Malwarebytes has described what it has found. According to Jerome Segura, Malwarebytes: “..many web portals started to run the Coinhive API in non-throttled mode, resulting in cases of cryptojacking—utilizing 100 percent of the victims’ CPU to mine for cryptocurrency with no knowledge or consent given by the user.”
It is this non-throttled approach that has caused the problem. Users have found their devices have been running out of power causing them problems. For those users on limited Internet connections they have faced the problem of their data allowances being used up. The user also gets to pay for the electricity used on home computers. While this is a relatively low amount, <$10 per month, it is still money that a lot of households cannot afford to waste.
There is another important issue here. The mining software is being delivered to computers using exactly the approach as malware. Users visit a website, the Coinhive API is installed on their computer and the cryptomining begins. Replace the Coinhive API with Exploit Kit and you have a drive by attack.
Segura commented: “We decided to call this new phenomenon drive-by mining, due to the way the code is delivered onto unsuspecting users, very much like drive-by downloads. There’s one important caveat, though: There is no malware infection at the end of the chain. This is why Malwarebytes is calling these attacks Drive-By Mining.“
Drive-By attacks and malvertising delivering the Coinhive API
Security vendors are aware of the risks of drive-by attacks. Most have active programmes trying to spot these attacks. Across the security industry there has been a lot of effort to share data about sites used for these attacks. Many of them are sites compromised by malware and used by criminals to distribute malware or in this case the Coinhive API.
The criminals use sites where users are least likely to be acting safely. Torrent sites, illegal software sites, music download sites, gambling and porn sites are all magnets for this type of activity. What also makes these attacks different from malware is permissions. Malware requires user permissions to install and run. The Coinhive API has been written to run without user approval. As such, users don’t know they are infected and a lot of security software fails to detect the attacks.
Another attack vector is malvertising. This is where hackers replace legitimate ads with their own. They look the same and even act the same. However, when the user clicks on the ad they are redirected to one or more sites controlled by the hackers. This then installs malware, or in this case the Coinhive API, onto the local machine. By breaching the major ad distribution networks, hackers have enrolled high profile sites into their malvertising campaigns.
It’s all about the money?
The question often asked is “what do hackers make off of each machine they infect? ” Malwarebytes cited numbers from TorrentFreak who has carried out their own research. That research was based on The Pirate Bay’s use of the Coinhive API.
It determined that a user with a mid-range laptop could generate 30 hashes per second. If they were on TPB website for five minutes per month, that comes to 9,000 hashes per user per month (30*60*5). It’s a tiny amount especially as Coinhive only pays out 0.00015 XMR per 1M hashes. The money comes when you scale that by many millions of users. At this point, for a relatively small amount of time, you can generate enough XMR to many thousands of dollars per month.
This is what makes the use of the Coinhive API attractive to some sites. Social media sites and those of very popular news, sport and other websites get far more than 5 minutes per user per month. This means that they can make money to pay for the content they deliver. For those companies who have previously considered paywalls to replace advertising revenue this makes Coinhive attractive.
It is also why hackers like it . Many hackers are not targeting the users of a single site nor are they targeting just 5 minutes per user per month. They are, instead, after multiple sites and hours of users time per month. This allows them to generate a substantial income from cryptojacking..
What does this mean?
The issue here is one of ethics and honesty. If users were sharing in the revenue they might be persuaded to willingly give up their machines and spare CPU capability. Charities in particular would be likely to benefit. However, this is neither of those instances. It is being carried out without the open consent of the user which is at best unethical, at worst illegal.
Coinhive has released an improved API to bring this problem to a halt. Unfortunately it will take a while for this to filter through and the abuse to stop. Coinhive sees this type of mining as an alternative to serving adverts to users. However, it needs to do more to convince users and particularly the security industry that it can do so responsibly.