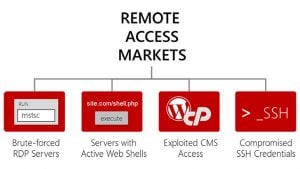
It is not just about saving attackers time. Not having to build phishing campaigns or work exploits to gain access, lowers the bar for attackers. Anyone willing to buy from a Remote Access Market can focus on the next stage of their attack. This could range from using a website to distribute malware to planting a card skimmer on an eCommerce site.

A blog from Raveed Laeb, Product Manager at KELA, looks at one specific Remote Access Market, MagBo. Laeb says: “This store is unique in a few different aspects, but mostly in volume of goods: over two years of operations, it featured access to nearly 150,000 compromised websites, mostly via selling access to web shell malware deployed on their servers.”
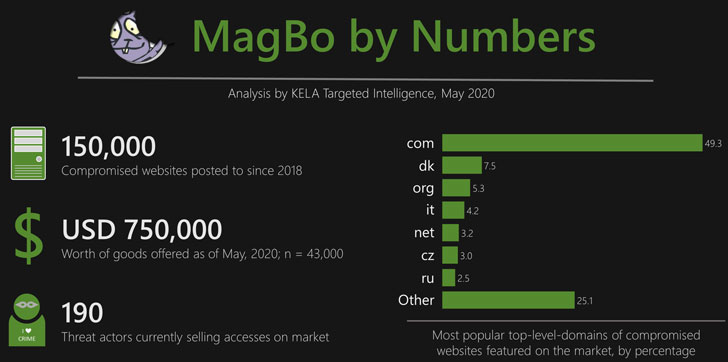
MagBo hosts details on over 43,000 unique hostnames
MagBo first appeared in early 2018. Within six months, it had already attracted the attention of the threat intelligence community. Flashpoint reported it was selling details of 3,000 breached websites. Its growth since then has been impressive, even by cybercrime standards.
Laeb reports that: “By late April 2020, it had over 28,000 servers totalling around $700,000 worth of goods. During our research, we were able to track 43,000 unique hostnames posted on MagBo for which we have full details; based on historical data, KELA is able to assess that over time MagBo has offered almost 150,000 distinct compromised websites for sale. These websites include anything from government offices and ministries sold for USD 10,000 a piece to small-business websites offered for a few cents.”
Although MagBo specialises in web shells (90% of listings), it also carries listings for CMS Panel Access (7%). The latter is especially important at the moment. Card skimming attacks aimed at online stores are on the increase. It is not just about those businesses who have had to move to the web as a result of the pandemic. British Airways, Ticketmaster, NutriBullet, and Forbes have all suffered card skimming attacks. Many of these attacks rely on access to the CMS to insert malicious Javascript onto webpages.
A constant stream of newly compromised sites
Laeb reports that MagBo has an active community looking to sell details of newly compromised attacks. He says: “Between 200, and 400 new compromised servers are added to the market on an average day – making it a fairly active market; the number of daily transactions is around 200, suggesting the market enjoys steady growth.” He goes on to say: “KELA’s data shows 190 different threat actors currently have active listings on the market.”
Why is MagBo getting such a steady stream of compromised sites? It’s simple. Like any business, it is all about the reviews. Laeb points out that MagBo: “Provides much more information that helps potential buyers evaluate the quality of product.” He compares it with other Remote Access Markets that provide almost no reputation data about what is for sale.

Ilia Kolochenko, Founder & CEO of web security company ImmuniWeb, Master of Legal Studies (WASHU) & MS Criminal Justice and Cybercrime Investigation (BU), comments:
“Wide-scale hacking campaigns are surging at the moment. Cybercriminals are using automation to monitor websites for outdated software, then breach vulnerable websites and even install security updates to prevent rival gangs from getting in. Once they have a sufficiently large bundle of backdoored websites, they sell it on the Dark Web to other cybercriminals focused in phishing, ransomware and other forms of digital blackmailing.”
It’s all about the platform
Platforms make cloud solutions attractive to developers and IT shops. It allows them to focus on writing code, not managing the infrastructure or application stack. Laeb says that MagBo is going down that same route. Attackers can now buy access from MagBo, write the code for their attack and then use MagBo Backdoor (MDB) to deploy the attack.
The use of servitisation to provide one-stop shops for attackers has been going on for some time. Malware as a Service and Ransomware as a Service are well-established services on the Darknet. MagBo is moving into that space with MDB but is not there yet. Laeb writes: “only around 6,000 web shells on the market utilized MBD in May 2020.”
Enterprise Times: What does this mean
Numerous sites sell compromised credentials on the Darknet. Remote Access Markets represent just some of these. What makes them dangerous is that they lower the barrier to entry for attackers. No longer do attackers need to build their own tools to gain access, sites like MagBo hand it to them on a plate.
Of more interest is the quality and verification of that data that MagBo offers. Its growth has not been impacted by the previous Flashpoint investigation. While MDB has yet to take off, the servitisation model plays to MagBo’s strengths.
Organisations are distracted due to the current pandemic. Work From Home has increased the attack surface and created problems for IT help desks. Rather than monitor core IT systems, cybersecurity teams are being pulled away to help IT and support users. It leaves opportunities for attackers to take advantage of MagBo to launch attacks.
Attackers are also looking at smaller organisations to embed themselves into future supply chains. Leaving malicious code on the partner portal of a website allows them to work their way through the supply chain. Kolochenko points out: “This is a serious problem for organizations because many suppliers and trusted third parties with privileged access to their data get silently hacked, and once exposed in underground marketplaces, the doors are wide open to their crown jewels. Worse, such attacks are virtually impossible to detect in a timely manner, given that no intrusion happens directly.”


























