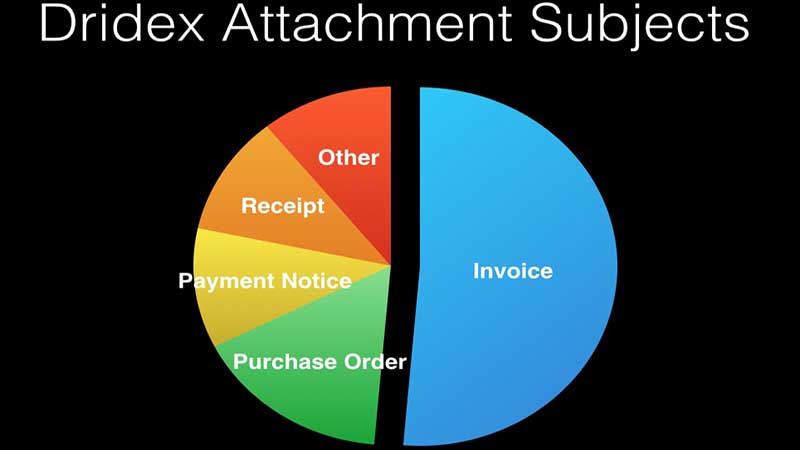

The malware known as Bugat, Cridex or Dridex has been in the news this week after the UK National Crime Agency issued a warning around a new strain of Dridex. It is believed that the Botnet that the US DoJ has taken down is not the only one distributing the Dridex software. According to Carl Leonard, Principal Security Analyst, Raytheon/Websense:
“Dridex has also been delivered by other bots such as Andromeda, one of the highly configurable malware tools available for sale in the underground community. Malware authors will likely replace that payload with another malware of their choosing and will not just stop at the UK but will aim to target internationally.”
What are Bugat, Feodo, Cridex and Dridex
They represent four variations of the same malware that has been distributed across different botnets. Each generation has carried a different payload, had a different email and been targeted at different groups of people. It’s main goal is to steal banking details and it works by attacking social media sites.
The files attached to the emails have varied from a PDF to a Microsoft Word document. Both rely on macros being enabled on the target computer. When the attachment is opened it executes the macros which then enable it to download the malware. The malware has been spotted on over 20 different servers making it hard to shutdown and stop.
Bugat is believed to use a variety of methods to disguise itself in order to avoid detection by anti-virus software. One potential sign of an infection is where the local anti-virus software appears to have turned itself off or repeatedly fails to complete a virus scan of the local computer.
The easiest way to prevent infection is to only open emails from known sources and make sure that macros are turned off. Even this is not a fool proof method as this malware appears to also steal contact data from user machines and use that to create a list of targets. This is often more effective than a random email purporting to contain an invoice as people are more likely to open an email from a known source.
The DoJ takedown of the Bugat botnet and arrest of the administrator
This takedown adds to the growing list of botnets that the FBI and DoJ have been successful in taking down in recent years. The announcement was made jointly by Assistant Attorney General Leslie R. Caldwell of the Justice Department’s Criminal Division, U.S. Attorney David J. Hickton of the Western District of Pennsylvania and Special Agent in Charge Scott S. Smith of the FBI’s Pittsburgh Division.

They named the administrator of the Bugat botnet as 30 year old Moldova national Andrey Ghinkul, aka Andrei Ghincul and Smilex. He was arrested on August 28th in Cyprus based on information provided to Interpol and the local police and is current awaiting extradition to the United States. He has been charged with nine counts of criminal conspiracy, unauthorized computer access with intent to defraud, damaging a computer, wire fraud and bank fraud.
In the statement issued by the DoJ Assistant Attorney General Caldwell said: “The steps announced today are another example of our global and innovative approach to combatting cybercrime. Our relationships with counterparts all around the world are helping us go after both malicious hackers and their malware. The Bugat/Dridex botnet, run by criminals in Moldova and elsewhere, harmed American citizens and entities. With our partners here and overseas, we will shut down these cross-border criminal schemes.”
A very lucrative malware
The success of the software is believed to have netted the owners more than $10 million inside the US. Meanwhile the UK NCA has said that over £20 million was stolen by the malware from UK banking accounts. Other governments have yet to provide details of how much they believe has been stolen by this malware.
The DoJ announcement says:
“The indictment alleges that Ghinkul and his co-conspirators used the malware to steal banking credentials and then, using the stolen credentials, to initiate fraudulent electronic funds transfers of millions of dollars from the victims’ bank accounts into the accounts of money mules, who further transferred the stolen funds to other members of the conspiracy.
“Specifically, according to the indictment, on Dec. 16, 2011, Ghinkul and others allegedly attempted to cause the electronic transfer of $999,000 from the Sharon, Pennsylvania, City School District’s account at First National Bank to an account in Kiev, Ukraine, using account information obtained through a phishing email.
“In addition, Ghinkul and others allegedly caused the international transfer on Aug. 31, 2012, of $2,158,600 from a Penneco Oil account at First Commonwealth Bank to an account in Krasnodar, Russia, and the international transfer on Sept. 4, 2012, of $1,350,000 from a Penneco Oil account at First Commonwealth Bank to an account in Minsk, Belarus.
“Finally, the indictment alleges that on Sept. 4, 2012, Ghinkul attempted to cause the electronic transfer of $76,520 from a Penneco Oil account at First Commonwealth Bank to an account in Philadelphia. In all three instances, the company’s account information was allegedly obtained through a phishing email sent to a Penneco Oil employee.”
As can be seen from the indictment above this is not just about consumers. If the computer of someone in the accounts department of a company is infected and they have access to the company online banking account, the hackers will go after the companies money. While this is something that should be caught by IT and anti-virus software, with the increase in Bring Your Own Devices (BYOD) there is a distinct possibility that a machine not under the control of IT will get infected.
CISOs need to ensure that they regularly send out advice to all members of staff to protect their own computers as well as take care with any computer that they use for work. They also need to put in place policies that make it possible for IT to provide anti-virus software to employees for their personal machines.
At present this is only believed to affect Windows computers and tablets running Windows as opposed to devices running Windows Phone.
Removing the malware
There are instructions for removing the malware on a page specially created by US-CERT which can be accessed by following this link or typing https://www.us-cert.gov/dridex into your browser.
As always when there is a major alert over malware, the advice is:
- Ensure that anti-virus and anti-malware software is up to date and that machines are checked on a regular basis.
- Do not open suspicious files or unexpected files irrespective of who they are from without checking with the owner first.
- Most of the emails sent out by this family of malware contain out of service telephone numbers which should always spark concern.
- As soon as the malware is detected delete it and run another anti-virus scan to make sure that it has been completely removed.
Conclusion
This isn’t the last we will hear about this particular malware. It has been one of if not the most successful piece of banking malware to date. While this botnet has been shutdown there are plenty more botnet herders who will happily allow it to be distributed from their botnets in exchange for a share of the spoils.
As reported by Leonard at the beginning of this piece, Dridex is already being served by the Andromeda botnet and industry experts expect to see it appear from other botnets soon.


























