
The blog says: “The ‘encryption’ used by the Ransomware is a stream cipher using a key randomly chosen from a list of 1000 hard-coded keys in RansomWarrior’s binary code.
“The Check Point Research team has been able to extract those keys, and, as the key’s index is saved locally on the victim’s computer, provide the correct keys to the Ransomware itself in order to unlock the files.”
The result is a free decryption tool and usage guide that can be downloaded from the Check Point website.
What is RansomWarrior?
RansomWarrior is the latest in a string of ransomware products that seeks to infect users computers. According to Check Point Research, the developers of RansomWarrior are inexperienced. It is written in .NET and “the executable itself isn’t obfuscated, packed, or otherwise protected.” They also say that the hackers are likely based in India.
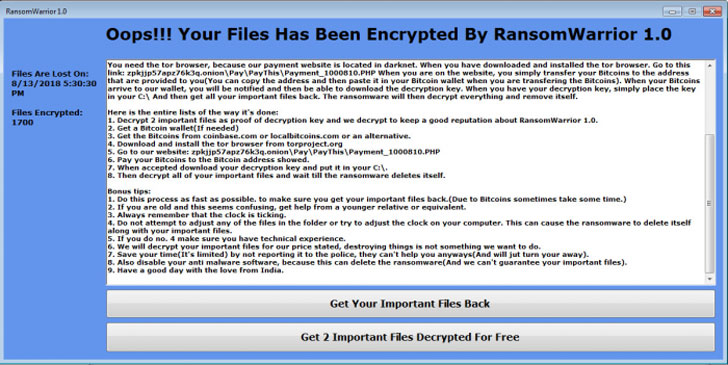
The researchers don’t say how the ransomware is spread. Those infected by it see a message on their screen instructing them to get the Tor browser. They are then directed to the Dark Web to make payment in order to decrypt their files (see image below).
The attackers do offer to decrypt 2 files just to prove that it can be done. This is intended to prove to the victims that they can get files back. However, the hackers also say that without payment, more files cannot be recovered. That is, until the Check Point Research team looked at the malware.
Check Point says that RansomWarrior was first detected on August 8th. The following day, a number of sites appeared claiming that to have anti-malware tools that could decrypt it. They all required users to download and run tools to scan their computer. Most promised to prevent any RansomWarrior infection. Some of these tools appear to have been created just to ‘protect’ users.
None of the sites explain how RansomWarrior worked or how they would decrypt files. The likelihood is that at least some of them were used to distribute the ransomware. Others would have ended up as Potentially Unwanted Programs (PUP) malware on machines. As they had been granted permissions to scan and change files by the users, they could also be used to install new malware onto victims machines.
What does this mean
Discovery of new malware is a daily process and there are a number of highly reputable security teams out there. Most will provide details of the malware, how it works, what it does and how it is being spread. There will then be a gap while they analyse the malware before offering solutions and registering the malware in their own detection database.
The emergence of ‘fixes’ a day after RansomWarrior was spotted is highly suspicious. It is possible that this was the infection route for some victims. The Check Point Research free tool does decrypt files and shows how poorly some ransomware is written.
However, it is important to realise that this is all about RansomWarrior 1.0. As has been seen with other malware, the hackers are likely to learn from this. Next time they are likely to make a better effort to obfuscate code. They are also likely to use remote servers to hold the unlock key for infected machines rather than hard code it into the ransomware.
For now, score one for the good guys.


























