The importance of data-at-rest security
Globally, data breaches continue to grow in sophistication, scale, and size as technological innovations continue to develop. It places significant pressure on security solutions that can keep storage systems within data centers safe and secure.
The consequences of such breaches can be high. Not only is personal data of an immeasurable value, but the financial impact on businesses can often be devastating both on its future finances and reputation too. Security Intelligence reports that the average cost of a data breach for large enterprises is around USD 3.92 million.
Additionally, it is estimated that 25,575 individual records were stolen on average between July 2018 and April 2019. It shows exactly what enterprises are up against when protecting data and preventing any breaches.
In response to this, governments worldwide have developed new regulations such as the European Union’s General Data Protection Regulation (GDPR) legislation and Lot 9 requirements. Provisions within these new pieces of law focus on end-user rights when it comes to the retention of their data, access control, and knowledge of who has what access to which pieces of data.
These developments have created a real demand for security innovations to protect integral pieces of information held within data centers and enterprises. To ensure complete data protection, GDPR mentions encryption as a possible form of mitigation to prevent data breaches. Meanwhile, Lot 9 requires Secure Data Deletion.
All data must be encrypted
For the most secure storage systems, all user data must be encrypted when first put onto a drive. This is regardless of wear levelling, a way of extending the life of storage devices. There should also be data erasure as a feature. It allows users to delete data from the storage system using specific commands. It also ensures that any information stored on the device is deleted safely and securely.
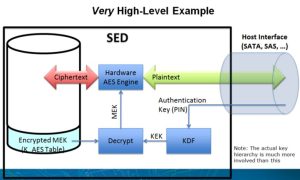
Software Full Drive Encryption (SW-FDE) is not always able to provide these guarantees. It results in Self Encrypting Drives (SEDs) being increasingly deployed to guarantee this “last mile” compliance to ensure that data is kept safe and secure to avoid a data breach.
The current foundation of storage security
Encryption can be done on a variety of different levels to ensure security. However, there are several factors to consider. What protection is provided against threats? What is the impact on overall performance? Does it meet the regulations previously mentioned in this article? What is the impact on other processes, for instance, being unable to reduce the amount of space that encrypted data takes up?
A SED is a great way of providing the necessary protection by encrypting all data accessible by the user on the storage device at high speed. The data is then decrypted as it is read with Media Encryption Keys (MEKs) generated and held by the storage device.
A need for innovation
There is more data than ever, and network volumes are only set to grow. It is essential that there is a more efficient way of securing storage systems and their data within data centers.
Imagine that it was possible to select an encryption key for each Input and Output (I/O) to a storage device. It would make it easier to support the EU’s GDPR’s “Right to be forgotten” rule by deleting individual higher-level objects. It might also be possible to externally manage MEKs and ensure that a storage device with no power has no encryption keys.
All of these abilities mean files, information, and keys can be accessed faster, and the whole process becomes far more efficient and secure.
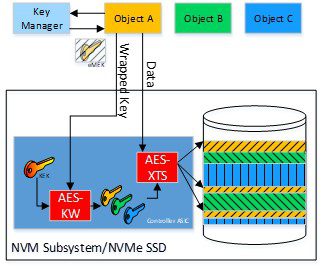
- This has driven Trusted Computing Group’s (TCG) Storage Work Group to develop the new Key Per I/O Specification. It allows enterprise servers to manage the cryptographic keys. It also allows millions of drives on storage devices to be used in the enterprise systems. This helps to support the key management needs of a diverse customer base. It generates centralized keys and effectively manages the storage device externally. The use of centralised key management is particularly useful for virtualising the VM system, user, account, and files.
- Key Per I/O will also leverage high-speed encryption. It can deliver encrypted keys to the device to improve security. It also ensures the device clears MEKs when power is removed for added protection.
The big picture
At a high level, the new Key Per I/O Specification is designed to provide protection and security that is completely managed by the enterprise system. It eliminates any potential data leaks from the increased vulnerabilities of satellite management. In addition, the centralized key management infrastructure fits into today’s enterprise server system architecture to provide much higher security and faster performance.
This allows keys to be provided to different users, storage devices and virtual machines. It also makes it easier for external management to eradicate data or initiate encryption. It also offers reliability when needing to rebuild or replace hardware devices. Performance can also be greatly improved by using the hardware real-time encryption assisted by the distributed device, thus eliminating any software delay.
This new concept also supports existing worldwide legislation which aims to improve the overall protection of data. Therefore, enterprises that adopt this solution within their storage systems will be one step ahead of competitors with a far more efficient and secure system.
Data centers and enterprises continue to grow in size to meet increasing customer demands. The Key Per I/O innovation will play a huge role in keeping data-at-rest safe from attack. It will also save companies thousands of dollars in breaches.
Collaboration between TCG, NVM Express, and OASIS KMIP ensures that Key Per I/O offers the best protection possible for storage systems globally and for a range of devices. TCG welcomes collaboration from companies worldwide to further enhance security solutions for data at rest.