
Stu Sjouwerman, CEO, KnowBe4, said: “With COVID-19 being around for over a year now and employees becoming more aware of the types of scams that have come out related to the pandemic, cyber criminals are having less success with related phishing attacks
“While users are becoming more savvy regarding COVID-19 phishing attacks, there is a steady increase of those falling for security-related email scams. The bad guys go with what works and in Q1, nearly a third of the users who fell for a phishing email clicked on one related to a password check. Always check with your IT department through a known good phone number, email address or internal system before clicking on an email related to checking or changing a password because it only takes one wrong click to cause monumental damage.”
What are the top phishing email attacks?
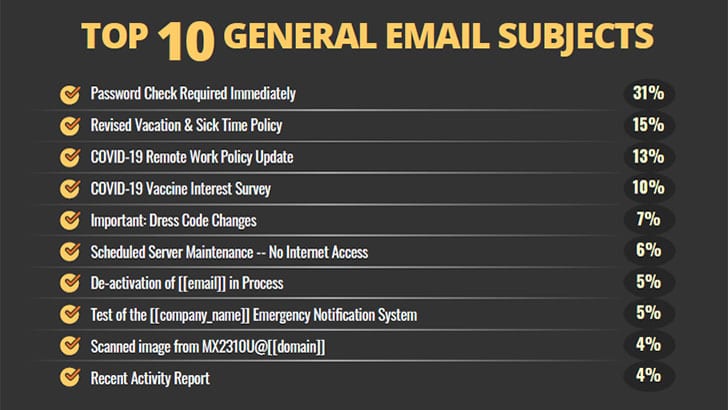
KnowBe4 has published a list of the top 10 general email subjects that users report to their IT departments. Some of these are from real phishing attacks, and others are part of phishing simulation exercises.
The most-reported emails are “Password Check Required Immediately” (31%). Although used often in simulations, in the real world, a common variation requires users to reauthenticate to continue accessing email. Another real-world attack around passwords reads: “Google: Take action to secure your compromised passwords.”
Another credential slurping attack uses the subject line “HR: Your payroll details need updating.”
Notification of winning prizes, credit cards declined by Amazon Prime, missed Zoom meetings, and messages around Facebook profiles are also commonplace. In almost every case, users are required to login to see more information or fix the problem.
What about social media?
Social media is a lucrative hunting ground for cybercriminals. Users tend to be more susceptible to phishing and other attacks across social media. In the last year, LinkedIn has overtaken many of the more popular social media sites for phishing attacks. KnowBe4 says that 42% of email attacks using social media are related to the business platform.
There are currently multiple campaigns targeting LinkedIn users. Just a week ago, eSentire reported how job offers on LinkedIn were being used to install the more-eggs backdoors on victim’s computers.
Email attacks using LinkedIn as the lure focus on your appearance in searches, new connections, and password resets. People fall for these by clicking the links, often obfuscated, in the phishing email.
Being tagged in photos on Facebook accounted for 20% of the attack, while login alerts for Chrome on Moto X (12%) is a surprise third place.
Enterprise Times: What does this mean?
Phishing emails are an increasing annoyance and threat. Importantly, this latest report from KnowBe4 shows that users are getting savvier around the common subject areas. However, that won’t stop the phishing emails from arriving. The key is making it easy for users to report suspicious emails and letting them know you are aware of it.
When it comes to LinkedIn, in fact, all social media attacks, don’t click on the link in the email. The links will almost always send you to a dummy site where your credentials are harvested. The cybercriminals will then quickly change your password, delete your phone number and change your email address. This will make it extremely hard to gain access to your account. Instead, log in normally to the social media platform to check if your password needs to be reset or someone has sent you a message.
When it comes to email for work or eCommerce sites, the same actions apply. Ignore the “click to reset” links. Login normally and check to see if the message is real. If in doubt, delete the message.


























