

Rob McLeod, Sr. Director of the Threat Response Unit (TRU) for eSentire, said: “What is particularly worrisome about the more_eggs activity is that it has three elements which make it a formidable threat to businesses and business professionals.” They are:
- It uses normal Windows processes to run so it is not going to typically be picked up by anti-virus and automated security solutions so it is quite stealthy.
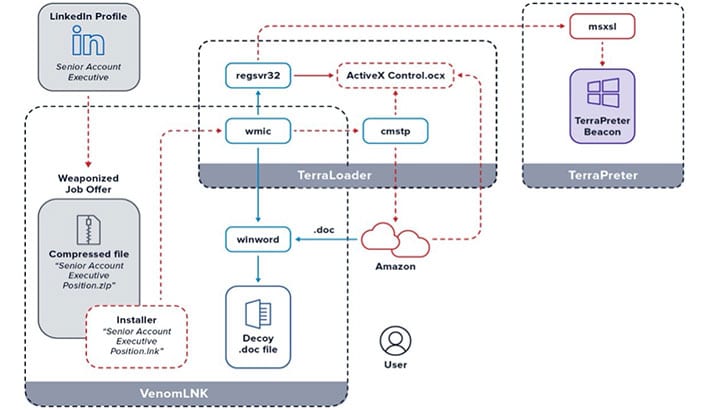
2.Including the target’s job position from LinkedIn in the weaponized job offer increases the odds that the recipient will detonate the malware.
3.Since the COVID pandemic, unemployment rates have risen dramatically. It is a perfect time to take advantage of job seekers who are desperate to find employment. Thus, a customized job lure is even more enticing during these troubled times.
Golden Chicken building out its MaaS infrastructure
Several things are interesting about this attack. The first is that Golden Chicken does not appear to be exploiting the backdoor itself. Instead, it rents out access to compromised devices through Malware as a Service (MaaS). It allows Golden Chicken to focus on increasing the number of compromised devices while earning money from other malicious actors.
Secondly, it is careful not to encourage the overuse of the more_eggs foothold on devices. eSentire says that: “The MaaS offering appears to be spare and selective in comparison to typical malspam distribution networks.” Such selectivity appears to be paying off with eSentire claiming: “The Golden Chickens threat group enjoys patronage from notable advanced threat groups, such as FIN6, Cobalt Group and Evilnum.”
The blog also goes on to detail the connections between more_eggs and the cybercrime groups named above.
Who is being targeted?
The current spearphishing campaign is targeting those working in the healthcare sector in the US. It will be interesting to see if it expands beyond that to other countries. There have been numerous attacks in the last 18 months against healthcare companies and workers as malicious actors have sought to exploit the pandemic. Some are simply looking to cause mayhem, and others are about stealing data.
It is not yet clear what malicious campaigns are currently being run by those using the Golden Chicken MaaS.
Enterprise Times: What does this mean?
Spearphishing is a tried and proven way of getting people to click on malicious links. In this case, Golden Chicken is hoping that people for new jobs as economies start to recovery. Of concern here is the use of the fileless backdoor more_eggs, which is hard to detect and block. However, the fact that it only installs when people open a malicious zip file should be some protection.
Using LinkedIn will have increased the success of this campaign. While some choose to block recruiters, many LinkedIn users are open to new work opportunities. The ability to select by position and location will also have helped the attackers choose their targets carefully.
At present, it is hard to know what future campaigns victims will be subjected to. eSentire doesn’t offer any evidence of current campaigns affecting those who have fallen for this current attack. What is also missing is some context on how bit the MaaS pool of infected devices is. This is an attack that we will hear more of over the next few months and even beyond.


























