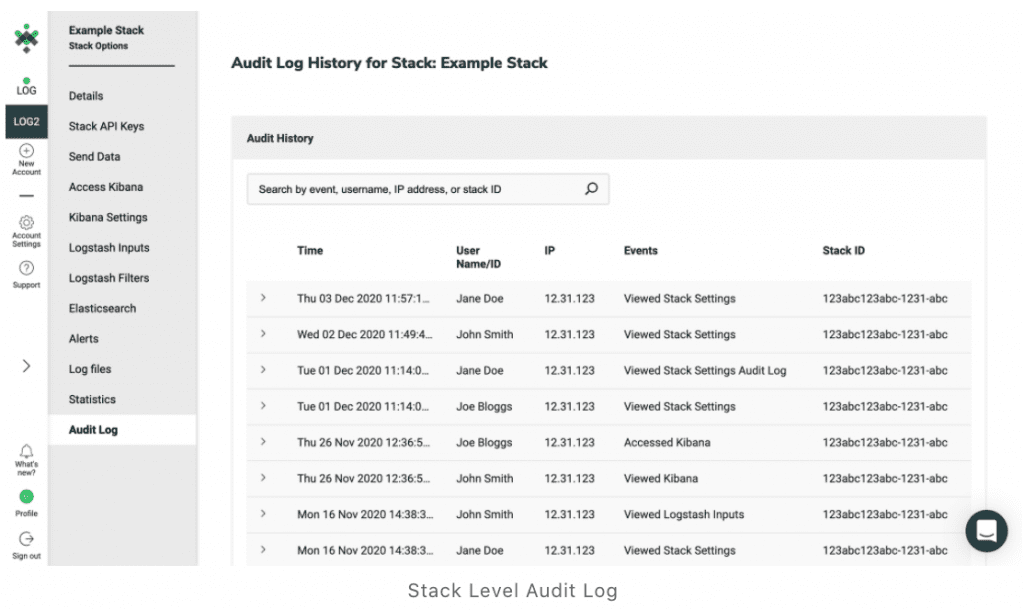
Logit.io has launched an advanced audit log feature which is now available to all customers. This is an update of its audit log which captures event logs and enables analysts to search and filter entries by IP address, the user account name, their event type and their Stack ID. Users can access events from on Audit.io activities or the ELK (Elasticsearch, Logstash & Kibana) Stack.
Besides the new filtering and search capabilities, the advanced audit log also has an export feature that allows users to export internal activity events as either CSV or JSON files for long term external storage. The audit log now includes Kibana access events, which enables the analyst to see when a new user has accepted an invitation to join their Logit.io account.
Logit.io offers a free 14-day trial for its solution. Pricing is calculated from a base of $29/month (for an annual contract) or $59/month. This seems a huge difference but helps push users towards an annual contract. Costs increase based on the storage requirements of data ingested for each day and for how long organisations need to retain the data. The solution is not user-based and a single purchase supports multiple users
Enterprise Times: What does this mean
Audit logs often just collect data and are left unused. This is often because the volume of data often deters any analysis until a user has to look at it. These new features enable users to leverage the audit log more efficiently. The Advanced Audit log provides a valuable tool for data protection officer and security analysts to ensure compliance. The periodic reviews become short and more valuable with better visibility of the data.


























