
The malware was used to target diplomats and members of NGOs from Africa, Asia and Europe. Kaspersky has said that there are several possible ways an attack could have been launched. One of these is the use of an infected USB key to boot the machine and install the bootkit.
However, the majority of infections are believed to have come via spear-phishing emails. Kaspersky has already detected some of these and says they were written in Russian. The attacks loaded malware that downloaded components to build an updater that wrote code to the UEFI.

Mark Lechtik, senior security researcher at Global Research and Analysis Team (GReAT) at Kaspersky said: “Although UEFI attacks present wide opportunities to the threat actors, MosaicRegressor is the first publicly known case where a threat actor used a custom made, malicious UEFI firmware in the wild.
“Previously known attacks observed in the wild simply repurposed legitimate software (for instance, LoJax), making this the first in the wild attack leveraging a custom made UEFI bootkit.”
Why is a UEFI bootkit a serious problem?
When a computer is turned on, it needs to know about the hardware that is installed so that the right software drivers can be loaded. The Unified Extensible Firmware Interface (UEFI) sits on its own flash chip on a motherboard. It provides information about the firmware to the operating system. Importantly, it also ensures that only drivers and OS loaders digitally signed by vendors are allowed to load.
One of the reasons why malware writers want to be in the UEFI is that it runs before the operating system and any other software. It also makes it persistent. No matter how many times you turn the computer on, the UEFI will always load. It means that even if parts of the bootkit are detected during runtime and blocked, rebooting the machine will just reload them.
The MosaicRegressor framework
In a blog on Securelist, written by Mark Lechtik, Igor Kuznetsov, and Yury Parshin, there is a detailed look at MosaicRegressor. What it shows is that this is not a one-off piece of malware. Instead, the researchers identified several suspicious firmware images, each containing four components. It was also able to determine that these were based on the leaked HackingTeam’s VectorEDK bootkit
During the deeper investigation into the malware dropped by this attack, the researchers discovered that MosaicRegressor is, in fact, a framework for espionage and data gathering. Multiple downloaders will install different pieces of malware on victims machines. Of concern, is that the framework design meant that the researchers were limited on what payload components they could recover.
In the image below, the researchers show the connections they were able to establish between the modules. It also shows what they were able to get copies of (in colour) and what they were unable to obtain (grey).
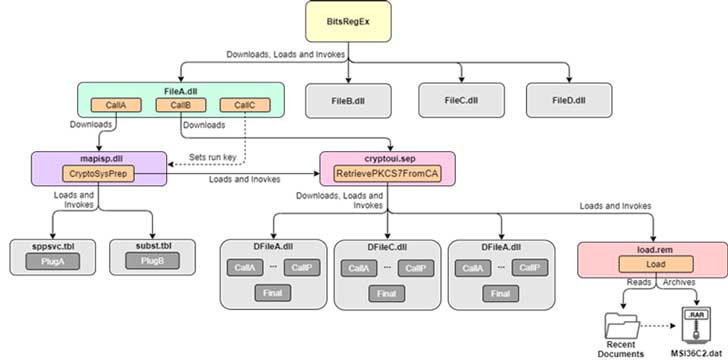
Another trick that MosaicRegressor employs is the use of several communication channels when contacting the C&C. It means that blocking one route would not stop it from working and downloading new payload modules.
Who is responsible?
Kaspersky is giving mixed messages as to who the attackers are. In its press release, it states: “The campaign has not been linked with confidence to any known advanced persistent threat actors.”
However, in the blog on Securelist, it refined its position. While still avoiding openly pointing at a specific APT, the blog states: “Code artefacts in some of the framework’s components and overlaps in C&C infrastructure used during the campaign suggest that a Chinese-speaking actor is behind these attacks, possibly having connections to groups using the Winnti backdoor.”
Enterprise Times: What does this mean?
Attacks against the UEFI are rare but do exist. Once inside the UEFI, they are not only hard to detect, but for many users, completely invisible. The persistence of the attack and, in this case, the development of a framework to support future malware, is also of major concern.
As Lechtik points out: “This attack demonstrates that, albeit rarely, in exceptional cases actors are willing to go to great lengths in order to gain the highest level of persistence on a victim’s machine. Threat actors continue to diversify their toolsets and become more and more creative with the ways they target victims – and so should security vendors, in order to stay ahead of the perpetrators.”
That MosaicRegressor is based on HackingTeam’s VectorEDK code is also unwelcome news. The researchers point out this is the first time they have seen an attack using that code. They also say: “The leaked code most likely allowed perpetrators to build their own software with little development effort and diminished risk of exposure.”
It highlights, once again, how the amount of leaked code related to vulnerabilities makes it easy for attackers to create new malware.

Igor Kuznetsov, principal security researcher at Kaspersky’s GReAT, commented: “The use of leaked third-party source code and its customisation into a new advanced malware once again raises yet another reminder of the importance of data security.
“Once software – be it a bootkit, malware or something else — is leaked, threat actors gain a significant advantage. Freely available tools provide them with an opportunity to advance and customise their toolsets with less effort and lower chances of being detected.”
For now, Kaspersky is recommending that users scan their machines using security software that will check the UEFI code.


























