
Both warnings are seen as increasing pressure on cyber insurers and bankers to not help in the payment of ransoms. It places many businesses in a difficult position. The current generation of ransomware attacks is not just about locking up data. Cybercriminals exfiltrate data before locking down systems. It gives them additional leverage to threaten the release of sensitive information if the ransom is not paid.
Businesses have been taking out cyber insurance to protect themselves against such threats. Withdrawal of support from cyber insurers means that an organisation might not have the funds to pay a ransom. Even if it does, by warning banks, FinCEN is making it hard for banks to provide access to, or assist in the movement of, funds for payment.
For many businesses, the result could be catastrophic. If they can’t pay, they risk data being leaked. That brings other penalties such as class action lawsuits and regulatory fines. All of these are business threatening. It also risks companies looking for other ways to make payments which could be even more expensive.
Who is this aimed at?
Both documents talk about sanctions lists. They suggest that this is about cutting off the cash flow to organised cybercrime and state-sponsored attackers. The latter group includes those whom the US has already charged with cybercrimes and a number of state-sponsored groups.
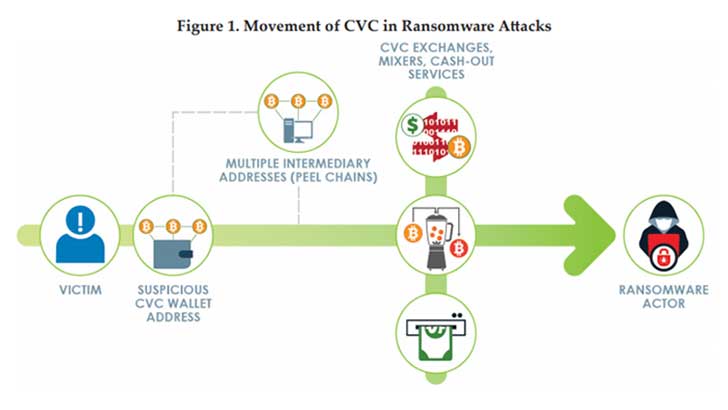
The challenge for banks, in particular, is relating cryptocurrency payments of a named individual or group to the various sanctions lists. Businesses are beginning to buy and hold cryptocurrencies as part of their currency operations. It is only right that they be able to buy, trade and even sell cryptocurrencies.
With banks being told that they should report concerns using a Suspicious Activity Report (SAR) this could cause chaos for businesses doing legal transactions. It will certainly erode trust between businesses and banks if banks report all cryptocurrency transactions as suspicious.
Financial Red Flag Indicators
To try and avoid misunderstanding, FinCEN has published ten red flag indicators of Ransomware and associated payments.
- IT enterprise activity is connected to cyber indicators that have been associated with possible ransomware activity or cyber threat actors known to perpetrate ransomware schemes. Malicious cyber activity may be evident in system log files, network traffic, or file information.
- When opening a new account or during other interactions with the financial institution, a customer provides information that a payment is in response to a ransomware incident.
- A customer’s CVC address, or an address with which a customer conducts transactions, appears on open sources, or commercial or government analyses have linked those addresses to ransomware strains, payments, or related activity
- A transaction occurs between an organization, especially an organization from a sector at high risk for targeting by ransomware (e.g., government, financial, educational, healthcare), and a DFIR or CIC, especially one known to facilitate ransomware payments.
- A DFIR or CIC customer receives funds from a customer company and shortly after receipt of funds sends equivalent amounts to a CVC exchange.
- A customer shows limited knowledge of CVC during onboarding or via other interactions with the financial institution, yet inquires about or purchases CVC (particularly if in a large amount or rush requests), which may indicate the customer is a victim of ransomware.
- A DFIR, CIC, or other company that has no or limited history of CVC transactions sends a large CVC transaction, particularly if outside a company’s normal business practices.
- A customer that has not identified itself to the CVC exchanger, or registered with FinCEN as a money transmitter, appears to be using the liquidity provided by the exchange to execute large numbers of offsetting transactions between various CVCs – which may indicate that the customer is acting as an unregistered MSB.
- A customer uses a CVC exchanger or foreign-located MSB in a high-risk jurisdiction lacking, or known to have inadequate, AML/CFT regulations for CVC entities.
- A customer initiates multiple rapid trades between multiple CVCs, especially AECs, with no apparent related purpose, which may be indicative of attempts to break the chain of custody on the respective blockchains or further obfuscate the transaction.
Interpretation will be the key
Interpretation of these red flags and creating processes and systems to deal with them won’t be simple.
In some cases, these red flags can be coded into the system. For example, the address of cryptocurrency wallets that the FBI or US Treasury has flagged as being used by cybercriminals. The same is true when talking about a wallet appearing on open sources. Presumably, there is a list of these that FinCEN or the US Treasury will provide. If not, this will add further costs and pressures on banks.
Another solution is better processes, for example detecting sudden large cryptocurrency payments. But this requires further clarification. What is a “large” payment? Is that judged in cryptocurrency or fiat currency? What requirements are there on a bank to check with the customer first before filing a SAR?
More process challenges exist around the knowledge of a customer. It is likely that most customers, the first time they buy cryptocurrency, have limited knowledge. How will a bank determine what a sufficient level of customer knowledge is? Who judges that a bank has sufficient knowledge?
Will banks and financial institution have to track crypto wallets?
What if a customer simply buys the cryptocurrency and puts it into a wallet held at a crypto exchange? The only obvious relationship here that the bank has is with the customer. What isn’t clear is if banks are to now track purchases of cryptocurrencies by customers and movement on customer wallets. If that is part of the intent here, how will banks do that? There are privacy and commercial confidentiality laws in place. Banks ostensibly spying on customers doesn’t seem like a healthy commercial relationship.
There is also the issue of the cryptocurrency exchanges themselves. How will they be policed? Who will police them when they are not located in the US? Is the US going to publicly announce a requirement for all cryptocurrency exchanges with US customers or attached to the US financial network to subject themselves to monitoring?
What does the cybersecurity industry think?

According to Jake Moore, Cybersecurity Specialist at ESET: “Using cyber insurance as a quick and easy get-out-of-jail-free-card to avoid ransomware is not the way we are going to win the fight against cybercrime. In fact, this sort of action actually encourages the criminal behaviour to continue and those at risk will never learn. If insurers continue to pay, demands will simply go up.
Insurance works well for a car or a home, but that’s because they are replaceable with no knock-on effect. Losing access to data can be damaging to everyone involved directly and indirectly. I cannot see cyber insurance working in the future in its current state. It indirectly funds cybercriminals to pursue their attacks further and it can leave companies feeling invincible.”
Vincent D’Agostino, Head of Cyber Forensics and Incident Response at cybersecurity company, BlueVoyant, says: “Recent articles on how paying ransomware hackers can violate US sanctions should serve to remind readers that casually wading into the ever-changing cyber threat landscape can carry dire consequences for the uninitiated and inexperienced.

“All breach events are serious but ransomware cases carry additional specific risk and exposure when handled improperly. Organizations facing such an event need to ensure that all reasonable steps are being taken to properly identify the threat actor/group they are facing in order to avoid potential costly regulatory fines on the back end of the breach.
“Although we agree that if ransomware payments were no longer made, this would serve to disincentivize ransomware attacks, we do not see this as a realistic strategy given the nature of what is at stake and how decentralized cryptocurrency such as Bitcoin operates.”
Enterprise Times: What does this mean?
In many countries around the world, it is illegal to pay any form of ransom. It doesn’t matter whether it is for a family member, an employee or a pet. That has not stopped the growth of Kidnap and Ransom insurance. In a similar vein, cyber insurance offers insurance against ransomware.
What is happening here is that the US is seeking to shut down this lucrative crime for cybercriminals, terrorists and state-sponsored groups. It is reminding people that there are anti-terror laws that prohibit the payment of funds to terrorists. It is also pointing to anti-money laundering laws. This is relevant because ransomware payments go through complex steps such as mixing, tumbling and smurfing. This is to hide where the money eventually ends up.
The problem is that it is using a blunt instrument to deal with a growing problem. For many commercial companies and increasing government organisations, this is about more than inaccessible data. The threat to release sensitive materials without payment is just as damaging to many organisations. Interestingly, some recent attacks have seen cybercriminals pitching the ransomware price fairly low to ensure they are paid. For a business owner, the payment becomes a cheaper and easier option.
D’Agostino commented: “If an organization takes reasonable steps to ensure that the threat actor they are dealing with is not specifically identified as a prohibited party, the decision to pay should ultimately be a business decision left to the victim.”


























