

“Today’s action publicly exposes the ongoing connections between North Korea’s cyber-hacking program and a Chinese cryptocurrency money laundering network,” said Acting Assistant Attorney General Brian C. Rabbitt of the Justice Department’s Criminal Division.
“This case underscores the department’s ongoing commitment to counter the threat presented by North Korean cyber hackers by exposing their criminal networks and tracing and seizing their ill-gotten gains.”
What cryptocurrencies were stolen and from whom?
The court filing details the size and scale of the thefts but doesn’t name the exchanges that were affected. Two of the exchanges that lost almost $300 million in cryptocurrencies are located in South Korea. The third called Exchange 3, lost more than $272 million, including 4000 million Proton Tokens (PTT).
This latter theft of PTT points to Singapore-based CoinTiger. In July 2019, it admitted that cybercriminals had stolen a cold wallet, an offline store, that contained over 400 million Proton Tokens (PTT). It was subsequently able to lock the wallet that contained the stolen PTT. Unfortunately, by the time it located the wallet, 120 million PTT had already been traded out. It was not the only loss that day. The transfer record for July 1st 2019 from PeckShield shows the other currencies being moved.
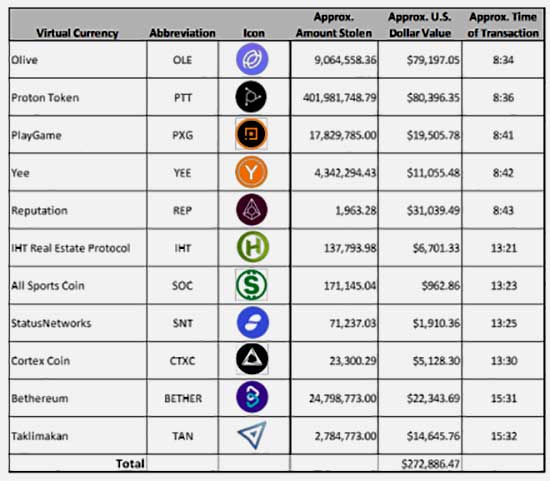
The court filing also shows the movements of cryptocurrencies from CoinTiger. More importantly, it shows how the money was then moved between accounts by the cybercriminals involved. By tracking those movements, the US has established a list of accounts at different virtual currency exchanges.
In all, there are over 10 Exchanges implicated either through having cryptocurrencies stolen or being used to launder the stolen tokens. At least one of those, Exchange 10 (Algo Capital), is based in the US. It lost Algorand (ALGO) tokens and Tether (USDT) stablecoins when its CTO, Pablo Yabo had his phone hacked.
There is also a full list of all the crypto wallets and accounts at the end of the document.
What will happen to the cryptocurrencies once recovered?
That’s a very good question. As the US has identified a number of victims of the crime, they or their insurers will have a claim on anything recovered. For some of the victims, the value of what is recovered will be far less than it was worth when stolen. Some tokens have seen significant volatility in the market, while others have been relatively stable.
If the original owners cannot be traced and the coins returned, the US may choose to sell them. It, like governments in other countries, has done this in the past. When the US shut down the dark web marketplace Silk Road in 2013, it seized 144,336 bitcoins. The US Marshals Service later sold those coins in 2017, for just over $48 million ($334 each). The bitcoin price at the time was around $4,000, so the sale should have realised over $577 million. In Feb 2020, it did much better when it sold 4,040 Bitcoins for $37.7 million
Any sale of the forfeited cryptocurrencies will attract the attention of large US companies. On August 11th, MicroStrategy announced it had adopted Bitcoin as a primary treasury asset. It spent $250 million to acquired 21,454 Bitcoins. While the purchase caused a small surge in the price of Bitcoin, it is now trading at roughly the purchase price. However, should other large US companies decide to follow suit, they would need to spread their purchases over a broader range of cryptocurrencies to prevent market distortion.
This is where government asset auctions could become lucrative. The US Marshals Service is currently outsourcing sales of forfeited cryptocurrencies to maximise its revenue. After the move by MicroStrategy, it might find there is a lucrative corporate market waiting to be tapped.
Enterprise Times: What does this mean?
There is a belief among many cybercriminals that cryptocurrencies are untraceable. As this court filing shows, it is a misplaced belief. It sends the message that current techniques such as mixing and tumbling cryptocurrencies to launder them, it not as effective as it might seem. The ability to track movements across crypto wallets means that authorities can follow the flow of the stolen funds and then block them from being used.
Importantly, it doesn’t break the anonymity of a wallet. However, the use of forensic analysis means that mistakes by cybercriminals will make it easier to identify the owner of a crypto wallet.
Cybercriminals are quick to adapt to threats to their livelihood. Mixing and tumbling through multiple exchanges is no longer enough. What will we see next? Importantly, where data has been stolen in a ransomware attack and then paid, will criminals continue to hold onto copies to hedge against their accounts being traced and locked?
This also raises a flag for corporate buyers getting into the market. They will need to show that they have done due diligence to ensure they are not buying stolen or tainted cryptocurrency. If not, they run the risk of having their corporate accounts locked and having to prove they are also victims here.


























