
DeathRansom first surfaced at the beginning of November 2019. The first version simply changed the file extension of files and asked users for money. Decrypting files was as simple as changing the file extension (docx, exe, xlsx, pptx, pdf, etc) back to what they should be. The result was that security experts labelled it little more than a joke.
Undeterred, the author issued an update that Bleeping Computer says was first spotted on 20th November, At that point DeathRansom began to behave like any other ransomware. It was infecting users, encrypting files and demanding payment.
Fortinet analysis into DeathRansom reveals details of the encryption
The first blog looking at DeathRansom comes from Minh Tran, principal security researcher at Fortinet. In it according to Fortinet: “The new version of this ransomware uses a combination of Curve25519 algorithm for the Elliptic Curve Diffie-Hellman (ECDH) key exchange scheme, Salsa20, RSA-2048, AES-256 ECB, and a simple block XOR algorithm to encrypt files.”
Fortinet describes the 12 steps that DeathRansom takes to encrypt files. As can be seen in the diagram below (credit: Fortinet), the DeathRansom author is throwing the kitchen sink at the user.
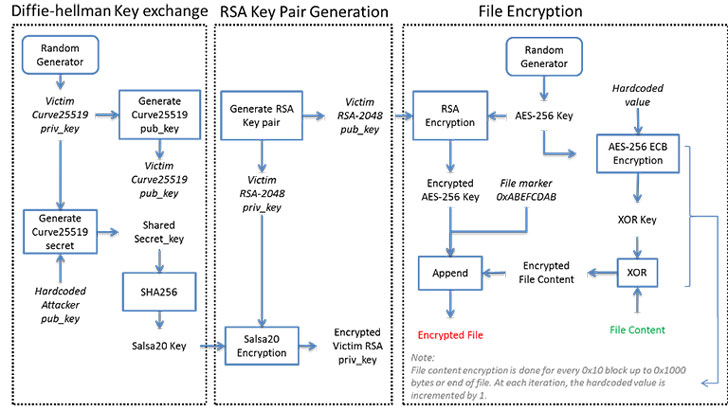
One of the steps taken by DeathRansom is to generate the victim’s Curve25519 public key. The key is included in the ransom note, a copy of which is placed in every directory where there are encrypted files. The user has 12 hours to buy the bitcoin required for the ransom and respond to the [email protected] email account. Failure to do so means results in the user losing access to their data.
A user with a long history of writing malware
In the second blog written by Artem Semenchencko and Evgeny Ananin, they attribute DeathRansom to a malicious actor called scat01. The authors suggest that scat01 is a Russian called Egor Nedugov. They list a number of different online accounts, both public and in underground forums, for the user under the monikers SoftEgorka and nedugov99.
The researchers detail how they tracked the user and identified other malware that he has been involved with. This includes Vidar, Azorult, 1ms0rryStealer, Evrial and Supreme Miner. Much of the information Fortinet uncovered comes from the gameshack[.]ru website.
The authors say: “the website “gameshack[.]ru” is controlled by attackers and they distribute malicious samples with scat01 attribution strings inside.”
The attribution data is supported by other posts and reviews written by Scat01 on numerous Russian underground forums.
In a bizarre twist it seems scat01 is just as likely to attack other malicious actors. The authors write: “We also found many other profiles of the same actor. According to information on underground forums, this person is responsible for account stealing, carding, malware distribution, and even the phishing and scamming of his forum mates. That is why nearly all his accounts on underground forums were eventually banned.”
What is most interesting about this is the amount of detail the researchers were able to uncover. Scat01 seems to have either made little effort to obfuscate who they are or they have created a long tail misdirection chain. The more realistic explanation is the former.
Enterprise Times: What does this mean?
DeathRansom is another piece of ransomware to add to the ever growing list. Most endpoint protection software providers will have updated their identification libraries. Users should ensure that their endpoint protection software is patched and up to date.
DeathRansom shows just how quickly malicious actors can escalate situations when called out for being a joke. In this case, scat01 decided to up the ante when it comes to encrypting files.


























