
Orkhan Mamedov and Fedor Sinitsyn, both researchers at Kaspersky Labs are the first to publish an analysis of KeyPass. What makes this of interest is that it does more than just encrypt files.
In the analysis, Mamedov and Sinitsyn say: “From our point of view, the most interesting feature of the KeyPass Trojan is the ability to take ‘manual control’. The Trojan contains a form that is hidden by default, but which can be shown after pressing a special button on the keyboard. This capability might be an indication that the criminals behind the Trojan intend to use it in manual attacks.”
How does KeyPass work?
Once installed on a target machine, KeyPass identifies all drives that it can get at. It is not limited to local drives in the target but will also look for network shares. This allows it to lock up parts of a corporate network. If the user synchronises to shared storage such as Box, Dropbox, Google Drive or OneNote, it will encrypt the local copies of the files and let the shared storage replicate the encrypted files to other users.
The initial analysis does not say if KeyPass will replicate itself to other machines that it finds on a network. That is, at least for now, a good thing.
Once it has created its target list of files, it encrypts them and sends the user ID and encryption key to its command & control (C&C server. Each encrypted file has its extension changed to KEYPASS and there is a ransom note placed in each directory (see below).
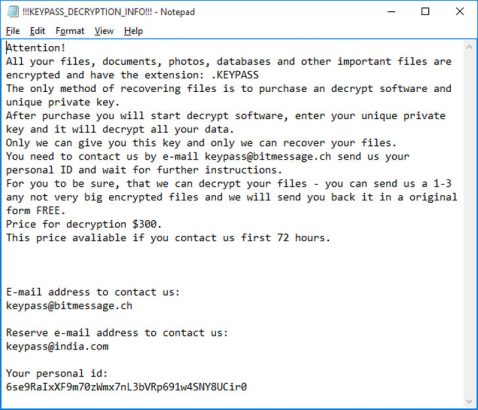
If the user pays the ransom, the attackers send an unlock code which hands the files back to the user. All of this mirrors the process used by the majority of ransomware attacks.
There is, however, a twist. The researchers discovered a hidden form and module. This allows the attacker to manually customise the parameters of the attack. That includes:
- encryption key
- name of ransom note
- text of ransom note
- victim ID
- extension of the encrypted files
- list of paths to be excluded from the encryption
This will allow the attackers to extract more money from some victims than the default $300 in Bitcoin that they are asking for. It would also allow them to customise the ransom note. This could be an indication that they are planning to license the ransomware. It would allow other attackers to customise the details.
What does this mean
Ransomware continues to proliferate. It is an easy cybercrime for attackers to get involved in. The rewards can be lucrative as the SamSam attacker has shown.
There is no known fix for KeyPass yet. If infected, users will have to decide if they are going to pay or lose their data. As the only infection route seems to be software installers, avoiding these would seem to make sense.


























