The rise of cryptomining has been fairly meteoric and shows no sign of slowing. Check Point reports that it is seeing a battle between Coinhive and Cryptoloot for top spot. Each is targeting the Monero cryptocurrency with the difference between them being performance and fees. Cryptoloot is the newcomer, it appeared in late 2017, is charging lower fees than Coinhive. It also promises faster hashrates which translates to more Monero, faster.
Maya Horowitz, Threat Intelligence Group Manager at Check Point commented: “Over the past four months, cryptomining malware has continued growing in prevalence. This persistent threat not only slows down PCs and servers, but once those agents have penetrated networks, they can also be used to carry out other malicious acts. Therefore, it is more important than ever for enterprises to employ a multi-layered cybersecurity strategy that protects against both established malware families and brand new threats”
Why is Coinhive popular?

Advertising on the Internet is a mess. There is a lot of fraud, rates are a race to the bottom and many sites are struggling to survive. Cryptominers offer website owners a chance to make money from visitors by using their CPU/GPU when they visit their site.
This is not a new approach. There have been many scientific and other programmes that have used permissive access to remote resources. Unfortunately, greed and the lure of easy money means that cybercriminals and unscrupulous website owners are infecting machines rather than get user permission.
What has made Coinhive popular is the ease with which it can be adapted by developers. There are a number of different Coinhive implementations available. This has allowed Coinhive to retain its place at the top of the index with a 20% infection rate. Close behind it is Cryptoloot which more than doubled its infection rate from 7% in January to 16 % in February. This moved it up from 8th in January. It will be interesting to see if it overtakes Coinhive next month.
The Rig exploit kit held its place as third closely followed by another cryptominer, JSEcoin. It was 5th in January and has now overtaken malvertising king Roughted for fourth spot.
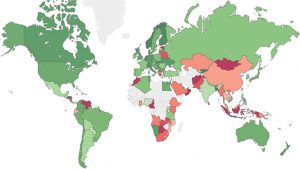
The heat map from Check Point also shows that cybercriminals are targeting Africa and Asia rather than the US and Western Europe.
What does this mean?
Cryptominers do not attract the same level of attention from law enforcement as malware. They can often sit undetected on machines and make money silently. Enterprises and those infected with the malware are picking up the tab for these attacks. It is not just the power consumed by CPUs and GPUs. It takes away processing cycles from apps that run slower as a result.
One thing that isn’t clear from the index, and ET has emailed Check Point for clarification, is how it differentiates between permissive use of cryptominers and malware attacks. Users have shown their willingness to allow their resources to be used for things they believe to be a good cause. As a result, some cryptominer installations have been permitted by users. Without separating out the permissive from the illegal, these numbers could be significantly distorted.
This distortion also does nothing to help a wider discussion of the problem of funding the wider Internet. If we get a response from Check Point we will update this article.


























