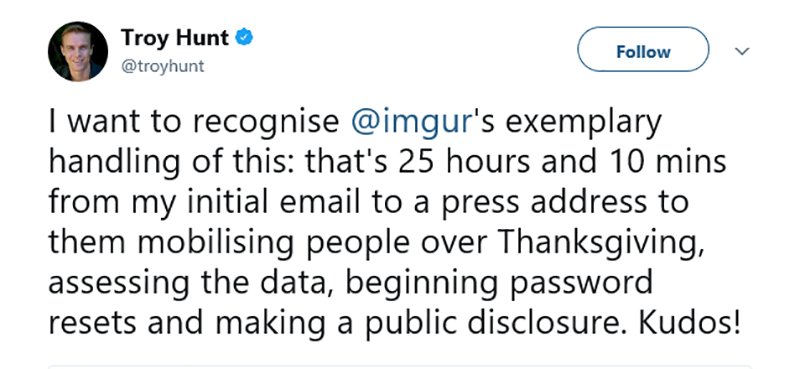
Image site Imgur has been praised for its response to a data breach covering 1.7 million user records. The breach occurred in 2014 but the data only surfaced last week. It was spotted by security researcher Troy Hunt. Hunt emailed the press address at Imgur to tell them what he had found. 25 hours 10 minutes later the company had made a full public disclosure and was dealing with the breach.
The response drew praise from Hunt via his Twitter account where he said:
What has Imgur said about this?
The response from Imgur has been swift and clear. Roy Sehgal, Chief Operating Officer, Imgur posted a blog outlining what they have done. In that blog Sehgal said: “On the afternoon of November 23rd, an email was sent to Imgur by a security researcher who frequently deals with data breaches. He believed he was sent data that included information of Imgur users.

“Our Chief Operating Officer received the email late night on November 23rd and immediately corresponded with the researcher to learn more about the potential breach. He simultaneously notified Imgur’s Founder/CEO and Vice President of Engineering. Our Vice President of Engineering then arranged to securely receive the data from the researcher and began working to validate that the data belonged to Imgur users.
“Early morning on November 24th, we confirmed that approximately 1.7 million Imgur user accounts were compromised in 2014. The compromised account information included only email addresses and passwords. Imgur has never asked for real names, addresses, phone numbers, or other personally-identifying information (“PII”), so the information that was compromised did NOT include such PII.”
While the company is still investigating how the breach happened, it has told users that passwords are encrypted. However, like many companies, in 2014 Imgur used an older hashing algorithm known as SHA-256. It now uses the bcrypt algorithm but only where users have changed their password since it was first encrypted with SHA-256.
What can users do?
Imgur is emailing all affected users. It has also initiated a forced password change for all users. What is not clear is how long it will wait to reset passwords that are not changed. Some users may no longer be using their account or log in irregularly. In these cases the company should change the password and then force users to update when they next connect.
Users should also think about where else they might have used that username/password combination. If there is any chance they reused the password then they should immediately begin changing it on other systems.
What does this mean?
The length of time between the breach and the public disclosure will cause some concern for people. However, unlike many data breaches, the data stolen was limited. The company records a username and password but does not hold other personal data on individuals. This means that breached accounts were only of use to hackers if users reused the username/password combination elsewhere.
Hunt noted that at least 60% of the usernames were already in the Have I Been Pwned database. It would be interesting to see if the cracked passwords from the Imgur breach matched any of the usernames already listed.
There are two things that stand out here. The first is that Imgur keeps the data it gathers to the bare minimum. Too many sites harvest user data without a clear idea of what they need it for. They then protect it poorly so that when a breach occurs there are serious consequences for users.
The second is the speed with which it reacted. Compare this to the current debacle by Uber and before that Equifax. Both have far more personal data and both failed their customers with a poorly thought out response.
How long before cybersecurity presentations cite Imgur as an example of what to hold and how to react?