Trustwave SpiderLabs has published details on a new banking attack it believes is set to go worldwide soon. Entitled Post-Soviet Bank Heists, the 11 page report can be downloaded from their website (registration required).
In the introduction to the report it says: “…each bank compromise resulted in a significant amount of stolen funds. The actual amount of money stolen was different in each case, with the average amount around USD$5 million (in cash), ranging from USD$3 to USD$10 million.” The total losses have been estimated at around $40 million.
What is important about this attack is that the attacks took place outside of any country where the bank had a branch. In addition, Trustwave SpiderLabs claim that each attack, once initiated, took just a few hours from start to finish. In effect, it is a high-tech game of smash and grab.
The Trustwave SpiderLabs attack analysis
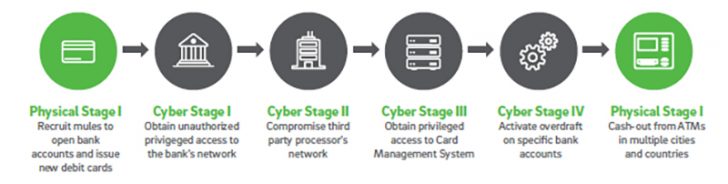
There is a clearly defined process for these attacks. Trustwave SpiderLabs has identified 6 primary steps. Of these two rely on physical attacks while four are cyber-attacks. Interestingly, they all show the potential for failure in both governance and the way the system operates. Banks are required to Know Your Customer. To do this they have made it harder to open new accounts. However, it seems that this was no impediment to the attackers.
The six stages are:
The paper goes into more detail about each step. There are several key steps that are of particular interest.
- The ease with which banks accepted fake identity documents
- The speed with which debit cards were issued
- Poor cybersecurity that allowed staff to fall victim to phishing emails that allowed systems to be compromised
- The ease of exploitation of the underlying Windows-based networks
- How easy it was to increase the withdrawal limits on accounts and create overdrafts
- Knowledge by the attackers of which ATMs had no camera security and would allow large sums to be withdrawn
Attackers used forensic countermeasures
There are several examples of forensic countermeasures used by the attackers. They avoided using tools that would have indicated an attack was in progress. By using standard Windows tools, they were able to avoid automatic detection by security tools. There are questions to be answered as to why the scripts they used were not spotted. This could be down to the use of stolen credentials although this is not called out in the report.
The attackers also took the step of destroying one of the systems that they used. This meant that the bank were unable to investigate themselves. However, the destruction was just the Master Boot Record and Trustwave SpiderLabs were able to restore the system. This provided a lot of detailed information.
There was evidence that the attackers had a deep knowledge of the banks systems. This allowed them to not only get in but also to know which systems needed to be compromised. It will be interesting to see if there are any links between these attacks and those on the Swift network from last year. The same depth of knowledge of banking systems is evident in both attacks. It could be that with Swift introducing tighter security controls, the attackers have evolved their methods.
Alternatively, this could be an entirely unconnected attack. If this is the case then there is serious cause for alarm. It shows that cybercriminals are getting detailed insider details about specific banking systems. Some of those will be common across multiple banks. Others will be unique to each bank. The concern here is that once that information is known, it is quickly shared with other hackers.
What does this mean
Trustwave SpiderLabs say that his is just the tip of the iceberg. They believe that Eastern Europe and former Soviet states are where these attacks are rehearsed. There is nothing to stop the attackers now deploying these attacks across the rest of the world.
To help banks out, there is a page of recommendations and a small set of indicators of compromise (IoC). These should be used by any financial institution immediately to check their internal systems. The initial phases of this attack take several months. Once in place, however, the extraction phase takes just hours. The quicker banks start to check their systems, the better.