Ad fraud specialist White Ops have exposed Methbot, a Russian-based ad fraud operation. According to the White Ops press release the fraud was delivering around $3-5 million in profits per day. This is money taken from US brand advertisers and media companies. Alongside the press release there is a 30 page report detailing how Methbot worked.
According to Michael Tiffany, co-founder and CEO of White Ops: “Methbot elevates ad fraud to a whole new level of sophistication and scale. The most expensive advertising on the Internet is full-sized video ads, on name brand sites, shown to users who are logged into social media and who show signs of ‘engagement.’
“The Russian operators behind Methbot targeted the most profitable ad categories and publishers. They built their infrastructure and tools and compromised key pieces of architectural Internet systems to maximize their haul. Methbot is a game changer in ad fraud and further evidence that the issue of human verification is constantly evolving and innovating, not abating.”
Advertising fraud on the Internet is not new
There is nothing new about click fraud. It has existed almost since marketing teams realised there was money to be made from advertising on the Internet. At the heart of this fraud is the demand from marketing teams for better metrics around their ads. They moved from paying for generic exposure on a website to per impression or per click. Both of these are open to abuse with the former going on daily and heavily under reported. The latter takes a little more sophistication.
Ever visited a website where you get barely a screen of information before you have to click on a next button? This is deliberate. Ads are resent to the browser every time the page refreshes. For sites selling per impression it means that a article spread over 4 pages can claim 4 times the number of ad impressions as if it were printed as a single piece. It has now become common for many large and small sites to do this. Part of the reason is that the payment per impression is often very low.
Click fraud is slightly more sophisticated. It has evolved to make money out of pay-per-click or cost-per-click advertising. It requires that someone clicks on the advert. This drives traffic to the website behind the ad. Competition for clicks is intense and lots of money is spent on trying to get people to click on links. Early on some sites realised that they could use botnets to click on the link and make money. The success of this fraud has made it a very useful tool for hackers. They can get paid for the referrals and also use the click to install malware on target computers.
Enter Methbot
Methbot has taken this to a new level. It is focused on video content and is a combination of impression and click fraud. The idea is not just to push the video so that it can be seen (impressions fraud) but also generate clicks so that it is played (click fraud).
This is not an unsophisticated botnet driven fraud either. The attackers have created a complex infrastructure to mask the obvious signs of a botnet. White Ops reports that it is using servers in both the US and Amsterdam. The latter has one of the highest densities of data centres in the world and ranks in the top five cities for Internet traffic. To make the connections harder to spot than a traditional botnet there is a custom-written browser.
Taking advantage of the infrastructure in the data centres the number of servers are quickly scaled. In doing so they get new IP addresses which makes it hard for the targets to spot the fraud. The attack even simulated mouse movements to make it look like there were users behind each click.
This use of rapidly acquiring new IP addresses and then rotating them is used by several hacking groups. It helps to mask attacks and even harder to spot Indicators of compromise and block the IP addresses. This approach also meant not having to use botnets and compromised end-user devices which security teams might detect.
The scale of the operation
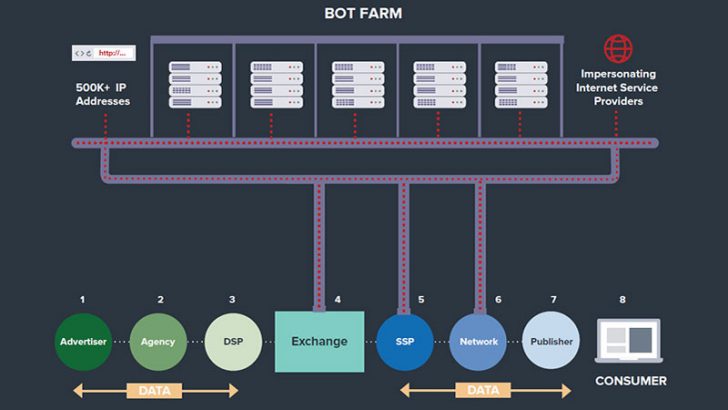
The White Ops report says that: “The operation has dramatic costs for both advertisers and publishers and abuses a variety of infrastructure providers by: Offering fraudulent web page visits and ad impressions by convincingly posing as more than 6,000 top Websites. Using a network of proxies running on 571,904 unique IP addresses, camouflaging the traffic to seem legitimate by falsifying IP registrations to impersonate large ISPs including Verizon, Comcast, AT&T, Cox, CenturyLink, TWC and others.

“For comparison, Facebook currently operates with approximately 270,000 IPv4 addresses. Feeding false information to geolocation information providers. Spoofing the data collected by viewability measurement providers, including video time watched and engagement actions like mouse movements.”
Ben Harknett – VP EMEA, RiskIQ said: “Methbot is interesting as it demonstrates cybercrime innovation, targeting businesses themselves by posing as active users to dupe advertisers and acquire premium advertising revenue. This is the first time we’ve seen cyber criminals game the system on such a scale, taking millions of dollars a day out of the ad ecosystem. It’s also one more example of why organisations need to expand their security programmes to incorporate digital defences that expedite the discovery, monitoring and mitigation of digital threats.”
Who is losing money?
Advertisers and website owners. This is not just about the relationship between the very large websites and key advertisers. A lot of smaller websites rely on income from advertising aggregators who can include video links in what they push to the page. White Ops has provided its own estimates of the volume of traffic and the estimated financial impact of Methbot.
- $3 to $5 million in revenue per day for its operators
- CPMs ranged from $3.27 to $36.72 with the average being $13.04
- 200 – 300 million video ad impressions generated per day on fabricated inventory
- 250,267 distinct URLs spoofed to falsely represent inventory
- 6,111 premium domains targeted and spoofed
- High value marketplaces targeted including PMPs (Private Market Places)
Conclusion
Methbot shows just how easy skilled hackers can make money from the Internet. In this case they went for a low risk approach. By targeting video advertising rather than end-user devices they reduced the likelihood of detection. They also made a lot of money very quickly. Their revenue is already 3 times more than that of the previously most successful attack.
The lessons from this attack for the advertising, cyber security and hacking communities will be far reaching. We now have code in place that shows it is possible to hit hard and fast and make a lot of money. Cyber criminals have been exploiting cloud infrastructure and data centres connected to high-speed links for a while. This attack will provide them with more information on how to effectively scale their attacks.
There is a lesson for enterprise IT departments. Many still struggle to effectively take advantage of cloud and scaling of infrastructure. This is an opportunity for system architects to see how to build a scalable solution for their business. Retailers in particular need to take a closer look at this as it would help them with peaks like Black Friday and Cyber Monday.