Skyhigh Networks ask “What’s in a name?”
Perhaps the biggest issue identified by Skyhigh Networks is the rather unimaginative names given to files which mean hackers don’t even have to search for data. The image below shows the average number of uses of key words in different types of files per organisation.
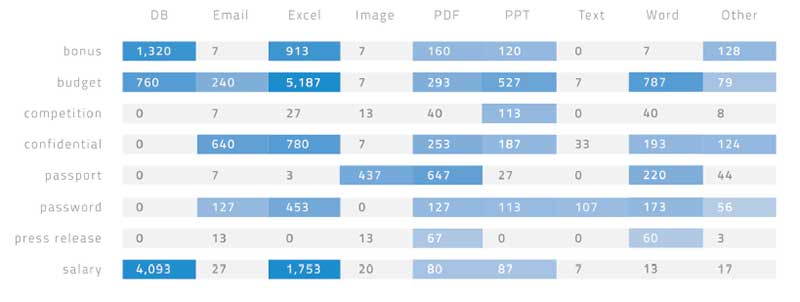
Looking at the image, it is easy to see how quickly hackers can begin to monetise the data they have stolen. Spreadsheets with salary in the title or as a table or field name in a database. Another word used is Bonus which will also point to personal financial data. A third word is Budget which is key for competitors to acquire and we know that not all hacking is about cybercriminals with cases of commercial and government hacking just as common.
Passwords are stored in Excel, Word, PDF, txt and PowerPoint files as well as being regularly emailed to users. The report cites the Hacking Team breach where among the files that were posted online by the hackers where it turned out that the IT security team stored passwords in unencrypted files that were stolen by the hackers. This is not an unusual issue in IT where the team often believe that as the guardians of the rules, they don’t apply to them.
Users are also accused of uploading images and PDF copies of passports. This one is more tricky. Sometimes it is required by a company in order to issue a visa or security pass and they require you to scan and email a copy of the relevant page. The problem is that users then save that image, forget about it and when the backup or copy their data to the cloud, the image goes with it.
All in all the number of files with filenames that identified sensitive data were:
- 248 – Competition
- 1,156 – Password
- 1,384 – Passport
- 2,217 – Confidential
- 2,681 – Bonus
- 6,097 – Salary
- 7,886 – Budget
To be clear, these are not personal files but company files stored on primarily unencrypted public cloud servers.
The question is what can be done to prevent this? Hawthorn believes a mix of education and coaching is required saying: “One thing IT often fails to do is adequately educate users. It needs to do this rather than block or delete. When it detects an issue it should coach a user and send then messages to help them understand what they’ve done wrong.
“Data Loss Prevention (DLP) could look for anything with the word Password inside the doc or in the filename. You could then quarantine that file and not give back until they talk to you. Unfortunately IT tends to block rather than implement coaching rules. It is never going to be easy but that doesn’t mean don’t try.
“Users must also take some responsibility to not leave big glowing neon signs to the data. You could argue filenames is a minor issue. If data gets lost you have a bigger issue.”
As we move towards an API enabled world and application vendors expose more and more of the code in their applications, one solution would be to take the same path as passwords. We now have the ability to set strong password requirements or reject a password. It should be relatively easy to do the same for filenames when a user is saving data whether that be locally or to a cloud service. Using a dictionary with a list of banned words, this would at least make it harder for hackers to find the sensitive data.
Another solution suggested by Hawthorn is multi-factor authentication. It is not enough to use a username and password to access files but to also require a phone or device to which a secondary security token can be sent. This is something that companies are moving towards deploying but there are hurdles to overcome.
Twitter, for example, offers the option to use a phone to add additional security. The problem is you can only use a phone against a single account. This means that people managing multiple accounts inside a corporate or who provide services to multiple customers are unable to use two-factor authentication. Despite being aware of this Twitter appears to have no interest in solving the problem.
(More…So what is to be done about it?)


























