
The latest IBM X-Force quarterly report suggests reported attacks could fall to 2011 levels although it issues a severe warning around the risks of the Dark Web and Ransomware.
Ransomware becoming a serious concern
Ransomware attacks are nothing new. They have been around for a number of years now and are a lucrative source of income for cybercriminals. Quoting a number of articles the X-Force Quarterly puts some numbers on the success of ransomware.
For example it quotes an FBI estimate that appeared in Security Week in June 2015 as saying “one variant of ransomware, CryptoWall has so far netted its operators around $18 million.” Another quote, this time from a ThreatPost report in August 2014 alleged that CryptoLocker, perhaps the best known ransomware, netted $1 million in its first six months.
One of the benefits of using ransomware for attackers is that it helps them keep a relatively low profile, requires little infrastructure and can be bought as a pre-packaged attack. More importantly, for those who are interested in the money rather than the notoriety, it doesn’t get the media or law enforcement attention that a major data breach does. The result is that it is also seen as a low risk issue by many organisations.
Backup, backup, backup
One of the big issues raised in the report is that even when users pay up the data may not be unlocked. There has to be a degree of trust that once you pay, the cybercriminal will honour their side of the deal and unlock your data. This is not always the case and as IBM reports, this is not always about malicious intent but also about incompetence. It points out that the encryption key may never get to the command and control server which means data cannot be unlocked.
The solution, as for many types of attack, is to backup data. Unfortunately, many people see copying their data to the cloud or onto an external hard disk as being enough. IT IS NOT!. Data must not only be backed up but the backup device disconnected from the computer. This prevents the ransomware locating the backup and encrypting that as well.
Ransomware getting nasty
As with the evolution of all attacks, ransomware isn’t standing still. Attackers are looking for the data which is most likely to persuade people to pay up. The online game community has found itself targeted with key game data being encrypted locking people out of their games. With gamers investing a lot of money in equipment, characters and status, they are likely to pay up.
The same is true inside companies. Lock the accounts data and companies will pay up or they cannot operate. One evolution highlighted in the report is the locking of web applications. This targets the software company and service provider running the web application rather than their users. As this affects their core business they will often pay up without quibbling.
Like other forms of cyberattack, ransomware has entered the cloud computing age. IBM X-Force cites a discovery by the Intel Security team of Tox. This is a Ransomware as a Service kit which lowers the entry level for cybercriminals looking to get into the ransomware market. As with other types of attack, this lowering of the bar is likely to lead initially to an increase in the number of attacks and eventually to a much more sophisticated set of software.
The Dark Web
The second focus of this report is the Dark Web. Since the Snowden revelations about governments spying on computers there has been a significant increase in the number of people using the Dark Web to hide their Internet usage. Despite what law enforcement and governments would like people to believe, this is not just about criminality.

The Onion Router (Tor) was developed by the US Government, is still funded in part by the US government and is used by numerous government agencies around the world. There is a paper from IBM Managed Security Services (MSS) that takes a deep dive into the Dark Web.
What IBM X-Force are reporting on is that the Dark Web is now becoming an increasingly popular place from which to launch attacks on companies. This might seem self-evident but the advantage of using the Dark Web is that attackers can make themselves appear as if they are in different parts of the world and therefore get through some of the cyber defences that companies use.
For example, a series of attempts to connect to a machine from China would have most security teams on high alert. Those same attempts coming from a location which appears to be in the same town as the company head office are likely to be seen as users having trouble connecting. This simple act of deception creates an opportunity for attack and exposes the problems that cybersecurity teams face in deploying their resources.
In the MSS paper they highlight that the majority of the malicious events they identified as coming from the Dark Web originated in the US. China was 7th on the list with less than a quarter of the number of events from the US. With a number of governments, including the US, talking about a cyber war with China, this data shows the danger of focusing on the geography of an attack.
Tor just a launch point for known attacks and data exfiltration
One of the interesting things about the attacks being seen originating from Tor is that there is nothing new here. SQL Injection, port and vulnerability scanning and Distributed Denial of Service (DDoS) are part of the daily set of attacks seen by security teams. The fact that they are being launched from with Tor is no surprise and suggests that the hacker community sees Tor as just another network to exploit.
Look a little deeper and there is one explanation that IBM offers for why these attacks, especially scanning and DDoS are now coming from Tor and that is bandwidth. While some countries in the world are still moving to 20MB/s, others are now looking at providing home users and businesses with broadband speeds in excess of 50MB/s, 100MB/s and in a few cases even high speeds.
This means that attackers who launch their attacks from Tor sites in those countries have access to large amounts of bandwidth with which to amplify their attacks. For DDoS in particular, this allows for very large attacks to be mounted and for many businesses, from small to large enterprises, finding themselves suddenly overwhelmed by the burst of traffic.
Higher network speeds also make it possible to exfiltrate larger sets of data, faster than every before. This means that cybercriminals can steal data often before companies realise the attack is taking place.
IBM X-Force say that companies can relatively easily protect themselves against many Tor attacks by blocking Tor nodes. It points out that there are a number of directories that publish lists of known Tor nodes that can be used to help block those IP addresses. While this isn’t a perfect solution is does reduce the risk of an attack from an established Tor node.
Blocking Tor from the corporate network
If this starts to become a standard approach to blocking Tor it will be interesting to see how the Dark Net responds. The recent case of the Terracotta VPN utilising compromised servers inside enterprises could lead to hackers trying to turn those servers into Tor exit servers. This would allow them to attack from inside companies. Wishful thinking? Not by a long way.
The IBM X-Force report looks at how easy it would be for a user to deploy a Tor server inside the enterprise. While it focuses on the actions of an employee, the fact that Terracotta required no direct employee assistance shows that once a hacker has control of a corporate server, they can easily make it a Tor server.
Of more concern to companies is the fact that a Tor server can be created on a USB stick and then executed by plugging that stick into a computer. The worrying issue here for security teams is that once the USB device has been removed, discovering that a machine has been compromised in this way and then proving it would require an expensive examination of the local machine.
In the IBM X-Force report it calls out a case where a Tor circuit inside an enterprise led to a successful attack against that company. With the shortage of skilled IT workers on the rise leading to more contractors inside companies, there is a real need to tighten processes and network monitoring to ensure that nobody comes in to the company and creates their own server.
There is a whole series of recommendations on how to prevent the use of Tor inside the enterprise:
- Prohibiting the use of unapproved encrypted proxy services
- Prohibiting the use of personally subscribed proxy services
- Prohibiting the downloading and installation of unapproved software
- Prohibiting the use of personally owned removable devices such as USB, optical media and Secure Digital (SD) cards
- If the use of removable media is required, mandating the use of only company-approved devices
- Prohibiting the booting of corporate computers to any other media than the hard drive
- Altering the BIOS of computers to boot only to the hard drive
- Disabling autorun for removable devices
- Using publicly available lists of proxy nodes to block network traffic to and from those sites
- Implementing a comprehensive desk audit program to ensure compliance
Vulnerability disclosures decline for the first time in four years
Finally some good news from the IBM X-Force team. There was just 4,000 vulnerability disclosures in the first half of 2015 leading IBM to predict a full year value of 8,000. This is a significant decline from 2014 when numbers broke through the 9,200 barrier and suggests we are on target for the lowest number since 2011.
But with any good news there is some bad news. According to the report: “2014 reflected a similar pattern, right up to the moment when the CERT Coordination Center of the Software Engineering Institute at Carnegie Mellon University disclosed the results of their Tapioca testing for which there seem to remain unanswered questions.”
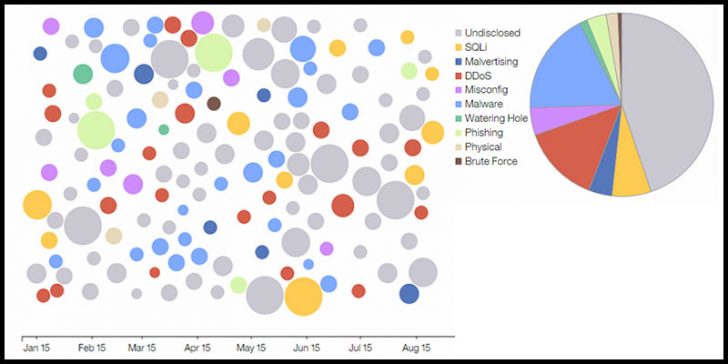
On the IBM X-Force Interactive Security Incident website it gives a near-time view on the types of attacks that are taking place. Disappointingly the cause of 45% of attacks is undisclosed making it hard to get a really good picture of what is actually happening. However there is enough information left to see where the current attacks are coming from.
The diagram on the IBM site shows that malvertising is now the biggest single problem in 2015. This mirrors a July report from web security experts Bromium. The next most common attack is from DDoS and this year has seen a number of companies from Huawei to Sharktech announce new DDoS appliances.
The rest of the identified attacks are really “business as usual”, and it should worry any CISO that security teams are still struggling to deal with attacks, such as SQL Injection that have been around for well over a decade.
This points to a significant lack of delivery by security teams. A major part of this will be down to underinvestment in both tooling and, more importantly, training.
Conclusion
The good news in this report is overshadowed by the spectre of the Dark Net and ransomware. The fact that IBM X-Force is seeing the installation of Tor servers inside enterprises is a significant shift in the security war. To date, much of the emphasis on security has been around protecting devices, networks and dealing with known types of attacks.
The emergence of security intelligence tools is relatively new and few companies have the right infrastructure to enable them to identify attacks on their network. In addition, the focus of security intelligence to date has been to spot Advanced Persistent Threats (APT) and to do service, application, user and network profiling to spot potential attacks.
The installation of a Tor server inside the enterprise is outside the current visibility of security teams. There is a distinct need for companies to adopt the recommendations in this report in order to close this loophole.


























