
Stagefright has been described as the worst vulnerability in Android’s history but despite a patch being issued by Google, it is claimed that the problem has still not gone away.

This claim comes in a blog written by Aaron Portnoy, Vice President, Exodus Intelligence titled Stagefright: Mission Accomplished? The blog identifies Google’s failure to deal with Stagefright starting with when Zimperium Research Labs originally reported Stagefright to Google in April. When Google failed to act Zimperium decided to go public about Stagefright in July which finally forced Google to act.
What makes Stagefright especially dangerous is that it only requires an MMS to be delivered to a users phone. That’s right, delivered not opened. The reason for this is that many vendors messaging apps process an MMS as soon as it arrives on the device and that triggers the code embedded in the MMS.
In their initial disclosure Zimperium claimed that around 95% of Android devices were susceptible to Stagefright which accounts for around 950m devices. This is not something that only affects the latest version of Android. All versions from Android 2.2 onwards are affected with older versions especially vulnerable to Stagefright as they lack some of the technology introduced into Jelly Bean or Android 4.3.
What is the problem with the Stagefright patch?
There are a number of problems with the Stagefright patch issued by Google.
- Exodus reports that the patch issued by Google is incomplete. They have already tested against a device that has been patched and proven that it doesn’t work. Google has told the original researcher that they had accepted all the patches required to fix Stagefright but has clearly not applied them.
- Exodus claims that they told Google about the failure of the patch on 7th August but have not yet had any acknowledgement from Google.
- Google has not withdrawn the faulty patch and is still distributing it to Android device manufacturers.
- Users who have already received the patch and who then run the Stagefright Detector application written by Zimperium will, according to Exodus, be told that they are not protected with they are not. Exodus claims this will lead to a false sense of security where users and even the companies they work for, believing the problem to be solved.
- Any patch issued by Google has to be accepted and then redistributed by all of the Google Android licensees. With every one of them running their own update service in order to support their devices and the software that comes on them, this can take from days to weeks.
- Many Android devices running older versions of the OS are unsupported by device manufacturers. This means that there are a number of users who will not get any patch, faulty or otherwise.
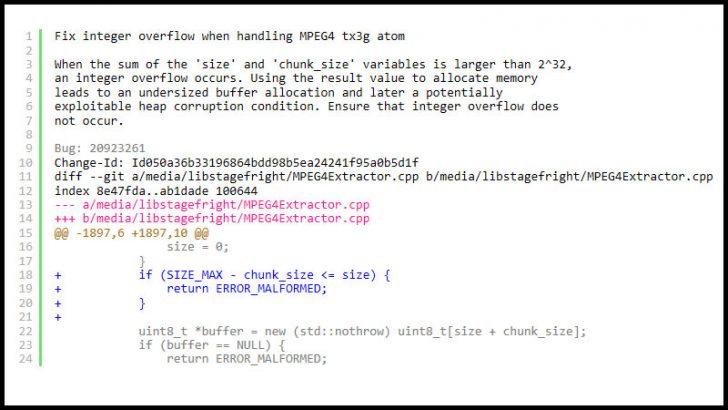
What has surprised many is not just that Google had to be shamed into issuing a patch but that it then chose not to check that the patch works. While we cannot be sure that they received the four lines of code that would have fixed the CVE shown above, the fact that this is now in the public domain and still being ignored by Google is creating a lot of concern for security teams.
Google has spent the last two years working hard to prove that it can tighten up Android. It has split Android so that businesses can protect corporate data stored in Android devices owned by their users. This has enabled it to drive into the enterprise market assisted by its major partners such as Samsung.
The problem with this whole Stagefright debacle is that it makes Google look like a partner that cannot be trusted inside the enterprise. It will not just be security teams that are concerned by Google’s behaviour. CIOs and CISOs will worry that Google has taken so long to act and this latest blog from Exodus will only deepen concern.
Conclusion

Google has to make some serious decisions around Android. It already enjoys the unenviable reputation among hackers for being easy to attack. Security companies regularly publish lists of vulnerabilities by OS and in the mobile world Android is the leader by a long way.
Stagefright has the potential to undermine two years of good work by Google to make Android more secure. It has tightened up on how apps are tested and approved to reduce the amount of malware being distributed through Google Play.
It now needs to take a hard line around patching Android. This is not just about issuing bounties to researchers who report vulnerabilities. It must be seen to patch them quickly and deal with the problem of its licensees allowing devices to get security patches direct from Google.


























