Centrify has released the findings from a survey conducted in April that shows up to a third of ex-employees still have access to data. While some will feel this number is smaller than expected, it is still big enough to show that corporate access policies have failed.
The 63 page document titled “Centrify State of the Corporate Perimeter Survey”, can be downloaded from the Centrify website. It is based on the responses from more than 400 IT decision makers (ITDM) in the UK and US, the survey makes for interesting and at times, eyebrow raising reading.
The headline from the survey is the number of users with elevated and often excessive privilege, the willingness to share credentials and the ease with which former employees can connect back into a system.
According to Barry Scott, CTO EMEA at Centrify: “Giving employees elevated access to privileged accounts and the organisation’s most critical data, applications systems and network devices is essentially giving them the ‘keys to the kingdom’. It’s the equivalent of providing the front door key to your house – and you’d be very, very careful who you gave that to.
”Privileged accounts are a very attractive target for hackers. It’s surprising that experienced IT decision makers like this are admitting that their organisations need to do a better job of monitoring who has access to their data, despite high profile incidents like Sony, JP Morgan and Target and the knowledge that breaches can potentially cost them millions of pounds.”
UK putting security ahead of the US
ITDM on both sides of the Atlantic put security at the top of their list of IT challenges. In the US 48% had this as their number one challenge but in the UK it was 25% higher at 60%. It’s hard to see why this figure should be so large especially given the publicity around high profile breaches in the US compared to the UK.
One thing that might explain the difference is age and experience. The survey shows that those with more than 10 years in IT were much more likely to put security higher up the agenda. It is possible that this is a generational difference as seen around other forms of technology such as social media.
Surprisingly, the survey suggests that experience and longevity in the job do not necessarily translate into confidence around security. When the ITDM were asked how confident they are in their company IT security, software and protocols 56% of US and just 35% of UK ITDM said they were very confident.
For those with more than 10 years experience the numbers dropped to 45% in the US and 32% in the UK. There is no explanation offered in the survey as to why this might be. Looking at other surveys and the security landscape in particular, it might well be related to issues around mobile security but we will have to wait and see if Centrify revisit the survey to ask more detailed questions.
Excess permissions and sharing are a serious security no no!
One of the challenges for many organisations is managing user permissions and risk. This is nothing new and has been going on for decades. The longer a user is with a company and the more roles they hold, the more permissions and accesses they tend to accrue. Part of this problem is that people rarely bother to revoke permissions once they have been granted.
A major problem with having too many permissions is that should a user get breached, attackers can gain access to a much wider set of data than might be expected. A more serious challenge is that users end up with too much power through the allocation of higher levels of privilege than they require to do their job.
75% of US ITDM admitted that more than 10% of users have privileged access. In the UK only 44% admitted to that level of access. Both levels are excessive and should fail any serious security audit and it suggests that the risk of excess access control is still not fully understand.
Compounding the risk is the sharing of login details. Although it is relatively trivial to allow secretary’s and PA’s access to their bosses computer, it is still commonplace for them to also have the username and password data. Yet the survey suggests that sharing is done on a much wider basis.
28% (US) and 10% (UK) admit to very often sharing their privileged access with other users. On a sliding scale of very, somewhat, not too often and rarely only 11% (US) and 19% (UK) said they never shared privileged access with other people. These numbers should shock Chief Information Security Officers (CISO) as they should contravene access policy in every company.
What the survey doesn’t disclose is how this relates to specific industries. If these numbers are the same across highly regulated industries such as finance, healthcare and pharmaceuticals, to name just three, then there are serious compliance issues here that must be addressed.
The survey went on to look at how common sharing access with contractors or third parties was in both countries. The results are frighteningly similar to sharing with colleagues. 24% (US) and 8% (UK) did this very often while at the other end of the scale just 11% (US) and 18% (UK) said that they never did this.
Applications that demand administrative privilege are just as much a problem as users. Too many developers and QA testers have administrator rights over their own systems. Scott says: “Many apps are written, built, developed and testing and work great but then fail in deployment. This leads to them getting elevated privileges to run. Things have tightened up here but there is much more that can be done. If the app requires elevated privileges then that should be approved by and attributed to the user so that it can be audited.”
Another part of the problem for companies in managing privilege is that it is not easy to visualise what access a user has or where it is necessary for their role. 20 years ago, HR departments were looking at getting involved in dealing with this but there was a lot of resistance from IT departments. Ironically, with Windows Server 2000, Microsoft introduce the concept of a departmental administrator who could manage the rights of their department but 15 years on it is still rarely used.
Scott doesn’t see this changing at all. “We don’t talk to HR and we don’t see or hear anything from IT departments about the involvement of HR at all.”
A significant concern for Scott is the level of access for contractors and partners. “Many people we speak to admit giving privileged access to partners. Some companies do have concerns over the amount of third-party access privileged access they allow.” It will be interesting to see when Centrify next conduct this survey if Scott reports that companies have reduced third-party privileges.
Failure to revoke access makes a breach easier for ex employees
One of the major challenges for all companies is blocking user accounts when they leave. Despite calls over 20 years ago for this to be part of the HR function it is still part of the IT remit. As a result, poor processes and time lags often mean users are left with access to systems after they have left.
On 16th June the news broke that the FBI was investigating US baseball team the St Louis Cardinals as suspects in hacking a rival club the Houston Astros. It is believed that what facilitated the attack was the fact that user accounts and passwords belonging to ex employees were still active on the Houston Astros system and were used to access the data that was alleged to have been stolen.
This is far from an isolated case and many instances of industrial espionage, let alone hackers and cybercriminals are believed to use this approach to get into systems.
On a positive note, 52% (US) and 50% (UK) ITDM said that users were blocked from the system the day that they left. A further 38% (US) and 30% (UK) said this happened with the same week that they left. It isn’t clear if this was about deletion of accounts or just accounts being suspended.
Unfortunately that leaves 10% (US) and 15% (UK) where it took more than a month and in 4% of instances in the UK ITDM admitted it could take a year or more to revoke access. This looks like a significant process failure and even waiting up to a week opens a company up to serious risk.
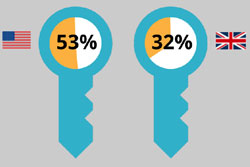
When asked if a former employee could use old passwords or credentials to access systems, the numbers were alarming. 53% (US) and 32% (UK) said if would be either very easy or somewhat easy for this to happen. Shockingly, when contractors are taken into account, the ability to access systems easily after leaving a company skyrockets to 82% (US) and 68% (UK).
These figures show a disturbing failure to manage access controls inside companies. One reason for this could be that IT is often overstretched and managing user access, beyond password resets is too easily ignored. There is a serious case here for the CISO and CIO to get control of their systems before a company suffers a major data loss.
As with allocating privilege, HR has a role to play here. They are responsible for managing the hiring and firing of staff and contractors which means that they are in the best place to suspend accounts when someone leaves. Final deletion could still be left with IT as long as HR gets a report to show how long an account has been suspended.
Conclusion
This survey touched on a lot of other issues in terms of access, data protection, IT security leadership and the threat of data breaches. None of the numbers there made for any better reading than those already highlighted.
What this survey does show, and admittedly 400 ITDM is a very small sample from which to extrapolate wider industry failings, is a need for IT departments to overhaul their processes around system access. The number of users sharing credentials, the numbers with privileged access and the ease with which former staff and employees can still access systems highlights systemic failure.
The European General Data Protection Regulation (GDPR) is due to be implemented in 2016 and regulators on both sides of the Atlantic are looking at more draconian compliance measures. For the 400 companies that the ITDM in this survey represent, the future looks like one full of data breaches and very large corporate fines.


























