PhishMe has identified a new ransomware charging a whopping $2,000 to remove. The ransomware is called Bart and the ransom is a substantial hike over other ransomware which may well drive prices up across the board.
To evade detection by anti-ransomware software Bart does not communicate with a Command & Control (C&C) server before encrypting files. This is a defence mechanism designed to reduce the risk of detection. Endpoint protection software often looks for network traffic to C&C servers in order to detect an infection.
How does Bart get into computers?
Like the vast majority of malware it starts with an email. Inside that email will be an attachment pretending to be an invoice or photos. Viewing the attachment installs the RockLoader installer on the local machine. This then downloads the Bart ransomware. If RockLoader sounds familiar that is because Locky and other malware use it.
So far it appears that this is about a one-to-one attack via email. No-one has yet reported the RockLoader installer using the infected users address book to target their contacts. There is also no evidence that Bart is able to move around a network. It is highly likely that will be the next move as the authors seek to improve their infection rate.
What happens once Bart is installed?
SecuritySpyware.com reports that Bart checks the local language on the infected computer. If it discovers Russian, Ukrainian or Belorussian it will not encrypt files on that computer. Instead, the focus seems to be on users in other European countries and the US. This is becoming common for a lot of malware originating in Russia. None of the major security vendors believe this is indicative of state sponsorship.
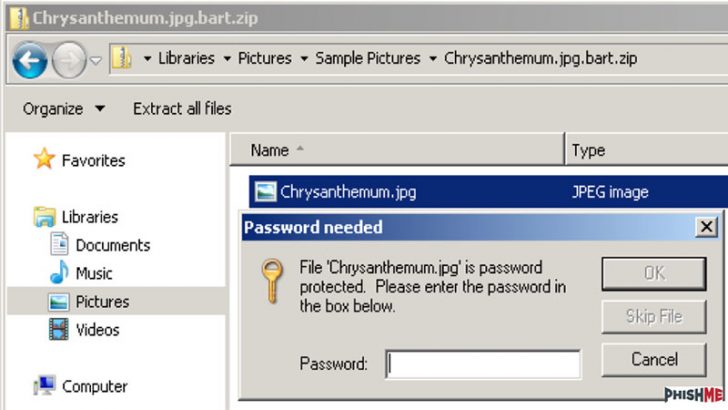
Files are first moved into a password protected zip archive and then “.bart.zip” is added to the filename. This is another move to evade security programs. Security programs look for sudden moves to encrypt large numbers of files. Moving files into a zip archive makes it look as if a backup is taking place. Detecting the difference between Bart and a user archive data will not be easy.
The ransom
Bart places two files in each directory once it has encrypted the files. These are “recover.txt” and “recover.bmp”. These files contain the details of where to pay the ransom and the unique identifier of each user. For users who do not know how to obtain bitcoins, the file also contains instructions on how to do this.
Conclusion
This is a sophisticated attack that is designed to evade the current generation of anti-ransomware software. By not talking to a C&C server and using zip archives it buys itself time to lock up files.
What will worry many security companies is the size of the ransom. So far the price for removing ransomware has been relatively low per computer. By jumping to 3 bitcoins per machine ($2,000), the authors are raising the stakes. It could be that they are arrogant enough to believe no-one can find them. The alternative is that they are looking to get as much as they can before someone develops a decrypter.
As with all of these security attacks prevention is about basic email safety. The most important is not to open attachments if you cannot be sure they have come from someone who can be trusted.


























