
Docker has announced the Docker Content Trust a move that adds digital signatures to containers to provide users with a more trustworthy environment.
The announcement was one of three blogs issued by Docker yesterday. On a busy day around the release of Docker Engine 1.8 they gave more details on Content Trust, Toolbox, Registry 2.1 and updates to Orchestration.
Docker Content Trust using digital signatures
One of the concerns that has been raised around the use of containers is security. Much of the concern has been around the ability to verify that the container being used can be trusted. The basis for the concern is well founded. In the mobile app world cybercriminals have been modifying apps so that while the user thinks they are downloading an original version of an app, they are in fact downloading something that contains malware.
With containers the risk is not just to a user but to a business. As Service Providers begin to build their own container repositories, they needed a way to reassure users that containers had not been altered. The Docker Content Trust will add a digital signature to each container that will be verified when the container is activated by a user. This approach means that unless a user ignores the digital signature or chooses to download containers that have not been signed they should be able to trust the veracity of the container.
The feature has been added to Docker Engine 1.8 and Docker has taken the decision to make its use opt-in. One of the major problems of the software industry over the last three decades has been the use of unsigned code. Even with attempts over the last 15 years to make code signing best practice and part of the software distribution mechanism, there is still a lot of unsigned code in the market.
Much of this unsigned code comes from internal developers who argue that they should not need to sign their code as it won’t leave the enterprise. Using an opt-out mechanism would still enable these developers to leave their containers unsigned during their testing phase or for private use. It would then allow operations teams to only allow signed containers to be used in production and it will be interesting to see how quickly this actually happens.
Overview of Docker Content Trust
The blog from Diogo Mόnica describes how the Docker Content Trust works:
“The diagram below provides an overview of how Docker Content Trust works. When images are pushed to a repository, they are signed with private keys held by the content publisher. When a user interacts with the image for the first time, they establish trust with that publisher and then all subsequent interactions require a valid signature verification from that same publisher. This is similar to the trust on first use model of SSH that developers are familiar with, except for the added security benefit of the initial trust being established over HTTPS using the corresponding public PKI.”
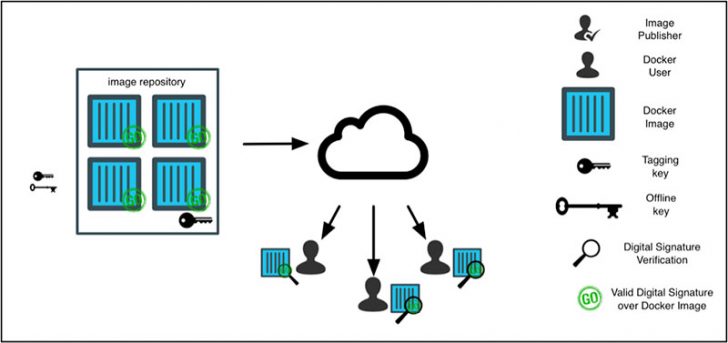
A well thought out process
One of the challenges of using any digital signature process is maintaining the keys and ensuring that they underlying process is robust. Reading through the blog announcing the Docker Content Trust, there are clear examples of how the process works and how it will protect against a range of different attacks.
Docker has chosen two open source products, Notary and The Update Framework (TUF) to provide the infrastructure for the Docker Content Trust. This is a sensible move that allows them to take advantage of two solutions that are already beginning to be widely used in the open source community and beyond.
Being able to revoke a key is a critical part of the process. In the mobile world we have seen safe versions of apps distributed for two or three releases before the malware payload has been added. Just because a container is signed does not mean that the contents are safe to use. However, a fully signed environment would enable a key to be quickly revoked and everyone using a container with that key would then be notified that it is untrusted.
The blog provides pointers to a number of reference documents that developers, operations and security teams should take time to read. These provide a good look at how the key mechanism works, how to revoke keys, how the process protects against attacks and more.
Conclusion
This is a key moment for Docker in its move to set the agenda in the container market. Introducing digital signatures, albeit with an initial opt-in approach, will provide reassurance for CIOs and CISOs that this is a trusted approach to computing.
The next step is to get Service Providers who are already using containers to announce that they are going to enforce Docker Content Trust for all production containers. This will send a strong message to their customers that this improves the security around the use of containers.
Of course there are still things that need to be done. There are a lot of containers out there that will need to be signed before this process can become ubiquitous. This will take time and it will be interesting to see which vendors see this as being important enough to prioritise.


























